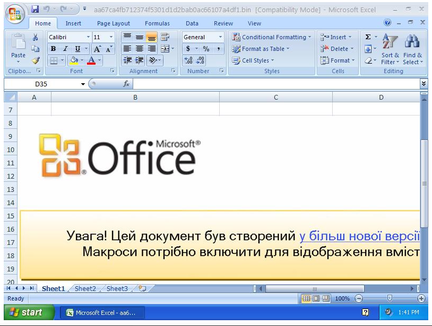
 This is the analysis of the first dropper Excel file used in APT's attack known as "Ukraine's Power Grid Incident" that occurred on December 23, 2015 in Prykarpattya Oblenergo ["Prikarptya Regional Energy Company" from Ukrainian] in Ivano-Frankivsk, Ukraine. Outline: I. File Characteristics II. Malicious VBA payload III. Dropped Files IV. Yara Signature V. Anti-Virus Report This Excel requires enabled macros. [translated from Ukrainian] I. File Characteristics Malware Sample Source: malwr File Name: BlackEnergy.xls, Додаток1.xls ["Supplemental" - from Ukrainian] Last Author: LSW Creation Datetime: 2015-02-04 07:35:08 Author: user1 Last Saved: 2015-03-18 07:41:04 Application Name: Microsoft Excel Code Page: Cyrillic [Ukrainian] File Size: 717.5 KB
0 Comments
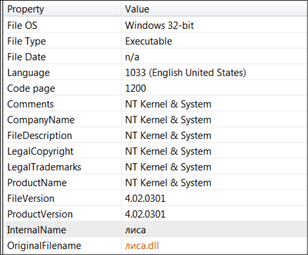 Source: VirusShare Malware Family: Backdoor, Implant, RAM Scraper Static Analysis Tools: pestudio, Immunity Debugger, CFF Explorer, PEID, BinText, IDA Pro Dynamic Analysis Tools: pexplorer, ProcMon, RegShot, ProcDump, Autoruns, Wireshark, Sandboxie, VMWare, Comodo, Payload Security Sandbox Reports: (1) Comodo: http://camas.comodo.com/cgi-bin/submit?file=4dae7fcde64a7ed61c51b17a57ffd2510381271a53d59beee730f59ae6c75352 (2) VirusTotal: https://www.virustotal.com/en/file/74fe8c68d878cc9699a2781be515bb003931ffa2ad21dc0c2c48eb91caba4b44/analysis/1450745229/ I . Static Analysis: Filename: loader.exe File Type: Win32 EXE Original Name: лиса. Dll [“fox” in Russian] Product: NT Kernel & System Target machine: Intel 386 or later processors and compatible processors Compilation Timestamp: 2015-06-18 04:37:16 Entry Point: 0x000011FC Subsystem: Windows GUI Number of Sections: 3 File Info: Microsoft Visual Basic 6.0 (when unpacked) Source: OpenSecurityTraining
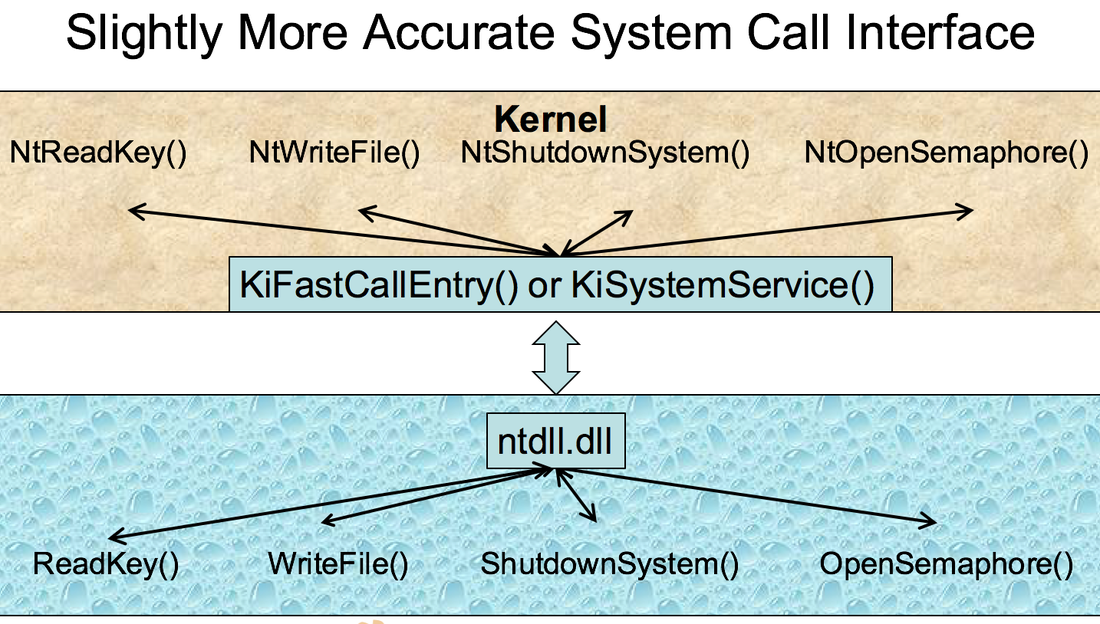
System Calls Revisited •You need to see the full path, and know that attackers can hook basically everywhere along the path. Source: OpenSecurityTraining Purpose of the course
• Give you a deep understanding of the mechanics of software exploitation • Prepare you to identify vulnerabilities in software source code • Help you understand the how and why of exploit mitigation technology • Depth not breadth. We will cover a few key concepts deeply, rather than covering many topics briefly. Course Outline 1 • Basic stack overflows • Shellcode • More on stack overflows • Heaps and Heap overflows Course outline 2 • Other Vulnerable Scenarios • Recognizing vulnerabilities • Finding Vulnerabilities • Exploit mitigation technology What are we trying to achieve? • Arbitrary code execution • Examples – Forcing ssh to give you root access to the power grid (like Trinity in the previous slide!) – Turning your vanilla HTTP session with a web server into a root shell session. – Forcing a privileged administrator process to execute code your normally wouldn’t be able to. – Etc…. x86 Review Lab - The EBP register points to the base of the stack frame. Local variables, which are stored on the stack, are referenced via this base pointer. - Every time a function is called, a new stack frame is setup so that the function has its own fresh context (its own clean set of local variables). - The call instruction also puts a return address on the stack so that the function knows where to return execution to. - Key point: local function variables are stored in the same place where return addresses are. Source: fumalwareanalysis
OllyDBG Cheat Sheet:
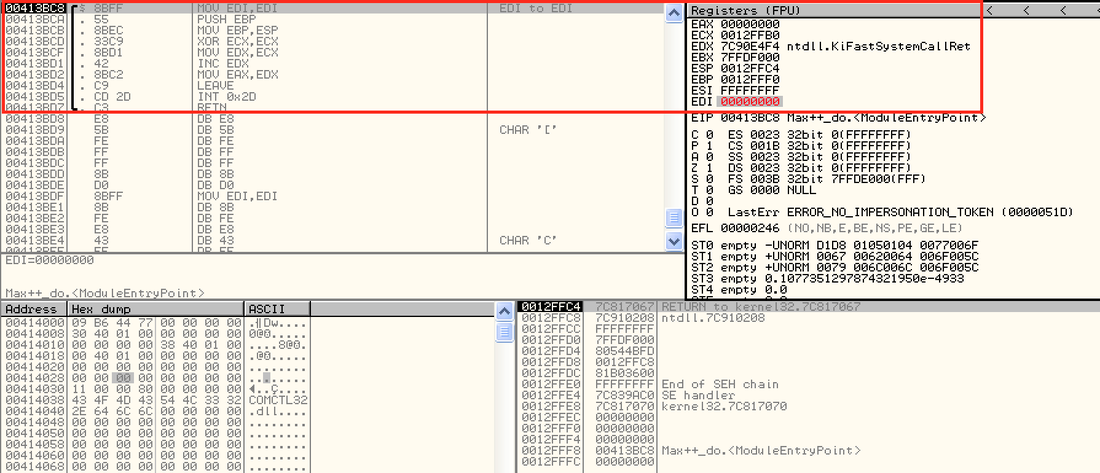
Change the EIP instruction in Immunity Debugger: From a Python Shell >>> imm = immlib.Debugger() >>> imm.setReg('EIP',int("hex value",16)) F9 (continue) is often used to continue from a breakpoint. Notice that the debugger automatically handles a lot of exceptions for you. If you want to intercept all exceptions, you should use SHIFT+F9 Goal: The objective today is to analyze the code snippet from 0x413BC8 to 0x413BD8. Answer the following questions. We will post the solution to these questions in the comments area. Q1. What is the value of EAX at 0x413BD5 (right before int 2d is executed)? The value of EAX is 00000001 at the memory location. Q2. Is the instruction "RET" at 0x413BD7 ever executed? No, EAX is an interrupt instruction; it skips the RET function. Q3. If you change the value of EAX to 0 (at 0x413BD5), does it make any difference for Q2? Yes. It makes its way to the RET function. Q4. Can you change the value of EIP at 0x413BD5 so that the int 2d instruction is skipped? Yes. Done in Immunity Debugger via ImmLib Python script. Q5. Modify the int 2d instruction at (0x413BD7) to "NOP" (no operations) and save the file as "max2[.]exe". Execute max2[.]exe. Do you observe any difference of the malware behavior? The sample does not run without the INT 2D function. Sophisticated, advanced rootkit dropper/trojan
Source: InfoSec Institute [http://resources.infosecinstitute.com/step-by-step-tutorial-on-reverse-engineering-malware-the-zeroaccessmaxsmiscer-crimeware-rootkit/]
Usually, when a rootkit infects a host, the workflow is structured as follows:
ZeroAccess has some powerful rootkit capabilities, such as:
|
AuthorVitali Kremez Archives
September 2016
Categories |
 RSS Feed
RSS Feed
