|
Source: https://www.computersecuritystudent.com/FORENSICS/VOLATILITY/VOLATILITY2_2/lesson2/ Basic Stuxnet Description (sophisticated APT worm-like trojan):
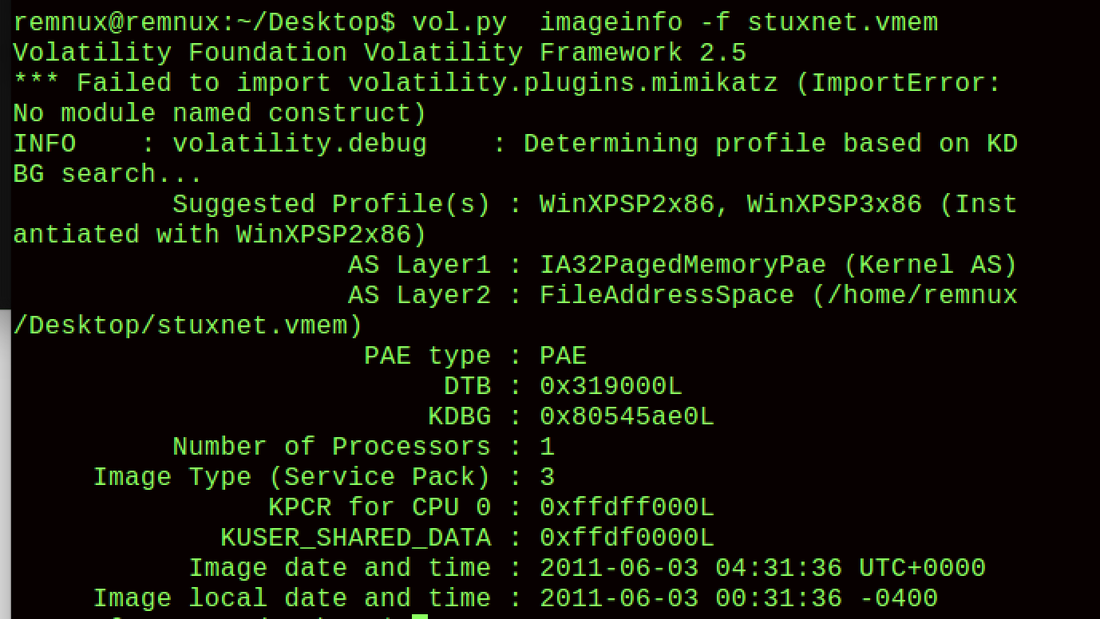
2. vol.py imageinfo=WinXPSP3x86 -f stuxnet.vmem
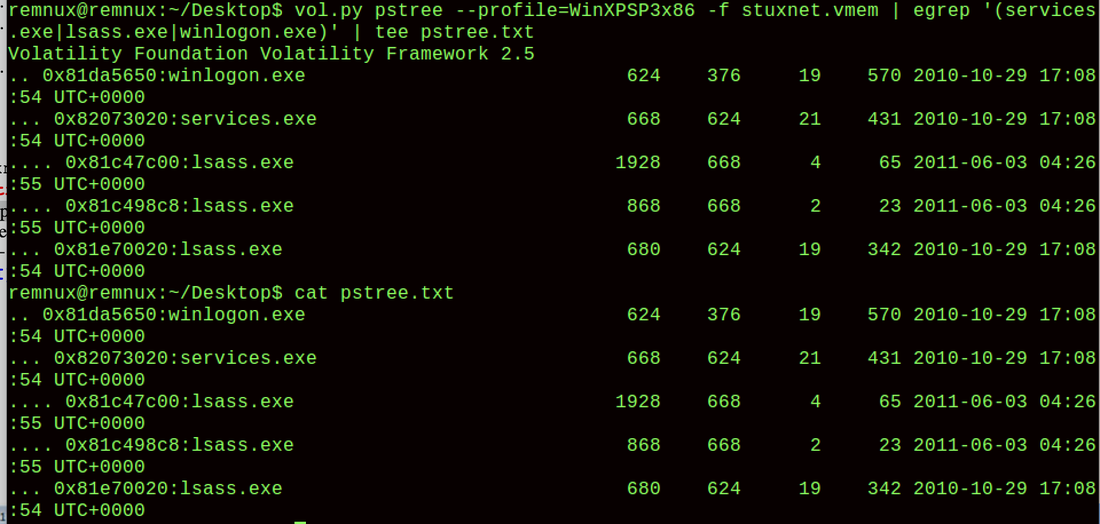
Analyze Stuxnet Process Tree 3. vol.py pstree --profile=WinXPSP3x86 -f stuxnet.vmem | egrep '(services.exe|lsass.exe|winlogon.exe)' | tee pstree.txt
0 Comments
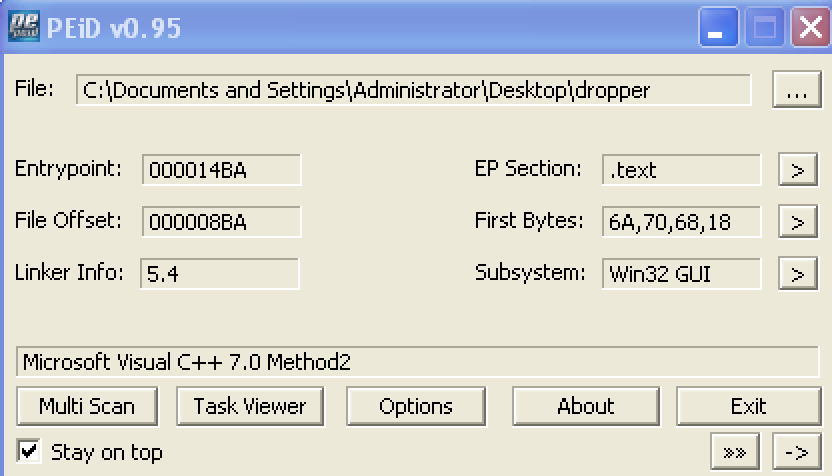
Source: SysAnalyzer, Immunity Debugger, IDA Pro File: necurs_dropper.exe Size: 97792 Bytes MD5: 6B3D2D146E683DAF0DEB906D57393E22 Mutex: PID Name * -------------------------------------------------- 1212 Instance0: ESENT Performance Data Schema Version 40 Processes: PID ParentPID User Path -------------------------------------------------- 2688 872 USER-06EF21E8DC:Administrator C:\Documents and Settings\Administrator\Desktop\dropper.exe Ports: Port PID Type Path -------------------------------------------------- 3417 2688 TCP C:\Documents and Settings\Administrator\Desktop\dropper.exe 3418 3536 TCP C:\Documents and Settings\Administrator\Desktop\dropper.exe 3419 384 TCP C:\Documents and Settings\Administrator\Desktop\dropper API Logger: 91222 CreateFileA(\\.\NtSecureSys) 912c6 GetCurrentProcessId()=2688 771bd3a9 connect( 69.50.214.54:80 ) Scanning for 19 signatures
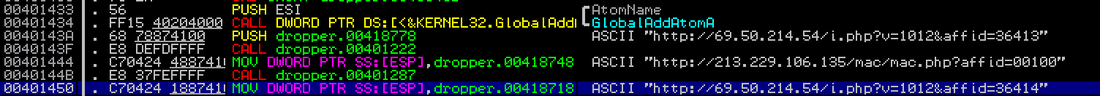
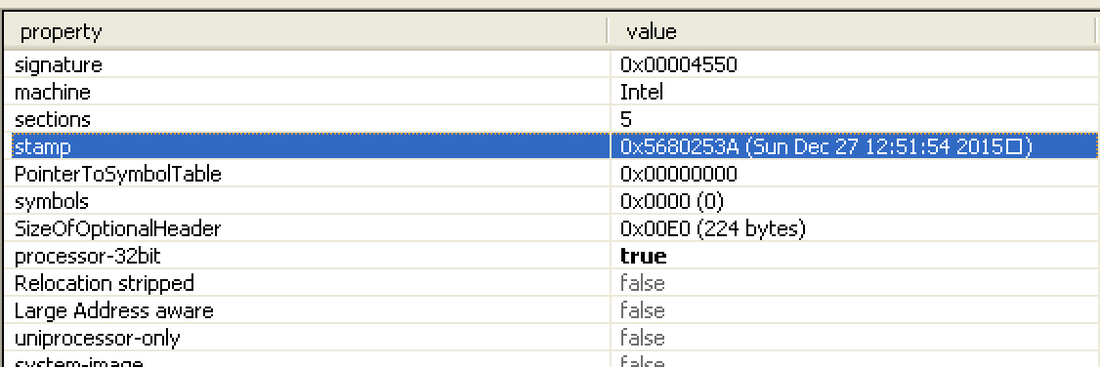
Scan Complete: 108Kb in 0 seconds Urls -------------------------------------------------- <html><head><title>504 Connect to %s failed: host unreachable.</title></head><body><h1>504 Connect to %s failed: host unreachable</h1><p>The following error occurred while trying to access <strong>http://%s%s</strong>:<br><br><strong>504 Connect to %s failed: host unreachable</strong></p></body></html> http://69.50.214.54/i.php?v=1012&affid=36411 http://69.50.214.54/i.php?v=1012&affid=36414 http://213.229.106.135/mac/mac.php?affid=00100 http://69.50.214.54/i.php?v=1012&affid=36413 http://69.50.214.54/i.php?v=1012&affid=36412 http://69.50.214.54/i.php?v=1012&affid=36410 Sample: 9e980cd01f46224e27b72369e988d8213436d50e7c3bd24344a8560c4fd23a04 VirusTotal : 2/55 McAfee-GW-Edition,BehavesLike.Win32.Ransom.mm,23.01.2016,132 Qihoo-360,HEUR/QVM20.1.Malware.Gen,23.01.2016,132 Compilation Timestamp: 0x5680253A (Sun Dec 27 12:51:54 2015) Here are the imported libraries:
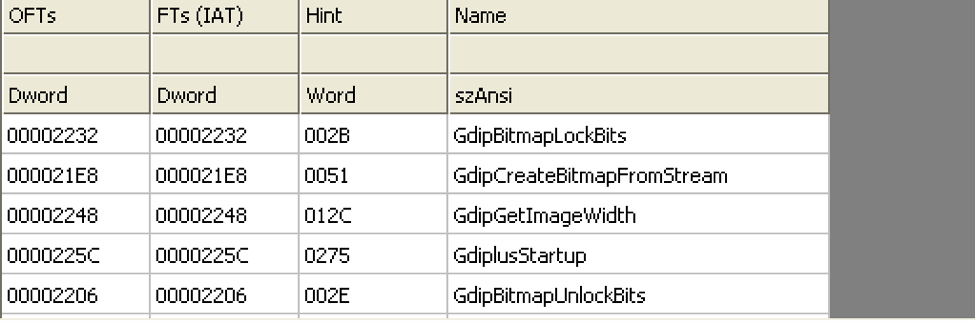
Here are the imported blacklisted calls:
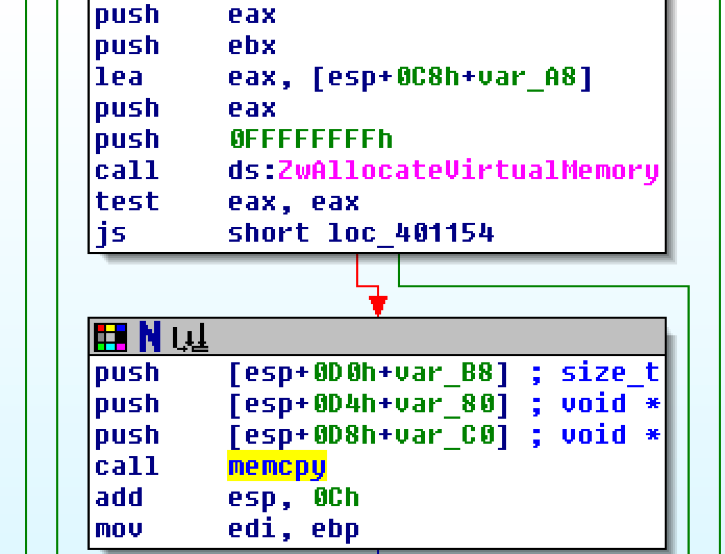
Here are indicators of the PNG dropper calls from gdiplus.dll (enables applications to use graphics and formatted text on both the video display and the printer): Red Flags:
Yara Signature: ZeroAccess v3 Dropper
global private rule gen_characteristics { condition: ( uint16(0) == 0x5a4d or uint16(0) == 0x0000 ) and filesize < 85KB } rule zeroaccess_9e980cd01f46224e27b72369e988d8213436d50e7c3bd24344a8560c4fd23a04 { meta: description = "samle_9e980cd01f46224e27b72369e988d8213436d50e7c3bd24344a8560c4fd23a04" author = "Vitali Kremez" reference = "Detects the ZeroAccess v3 Dropper" date = "2016-06-03" hash = "9e980cd01f46224e27b72369e988d8213436d50e7c3bd24344a8560c4fd23a04" strings: $s0 = "<requestedExecutionLevel level='asInvoker' uiAccess=\"false\"/>" fullword ascii $op0 = { 83 c4 0c 8b fd 8d 44 24 40 50 ff 74 24 18 ff 15 } /* Opcode */ $op1 = { 8d 44 24 38 89 5c 24 3c 50 ff 74 24 18 89 5c 24 } /* Opcode */ $op2 = { 8d 44 24 14 50 56 ff 15 14 20 40 00 85 c0 0f 85 } /* Opcode */ condition: uint16(0) == 0x5a4d and filesize < 85KB and all of them } |
AuthorVitali Kremez Archives
September 2016
Categories |
 RSS Feed
RSS Feed
