|
Reference: https://www.virustotal.com/en/file/1f8c42caeacb44f2a738ee2104457220eca6d7a7416f953d01bc716a63b3db8d/analysis/ Objective:
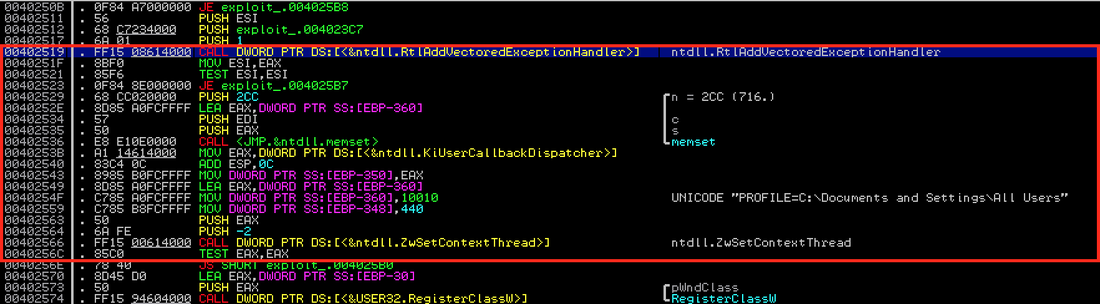
LPE Implementation and Functionality:
Additional Analysis:
Dumped Process:
PDB Path:
Kernel31 Api Log: -------------------------------------------------- ***** Installing Hooks ***** 71ab74df RegOpenKeyExA (HKLM\System\CurrentControlSet\Services\WinSock2\Parameters) 71ab80c4 RegOpenKeyExA (Protocol_Catalog9) 71ab2623 WaitForSingleObject(794,0) 71ab87c6 RegOpenKeyExA (NameSpace_Catalog5) 71ab835b RegOpenKeyExA (Catalog_Entries) 71ab2623 WaitForSingleObject(78c,0) 71aa1af2 RegOpenKeyExA (HKLM\System\CurrentControlSet\Services\Winsock2\Parameters) 71aa198e GlobalAlloc() 7c80b719 ExitThread() 5ad8bdf9 GetCurrentProcessId()=3644 5ad7a0e2 IsDebuggerPresent() 773d3faf LoadLibraryA(UxTheme.dll)=5ad70000 773ea4a1 GetCurrentProcessId()=3644 Yara Signature: /* Global Rule -------------------------------------------------------------- */ /* Will be evaluated first, speeds up scanning process, remove at will */ global private rule gen_characteristics { condition: ( uint16(0) == 0x5a4d or uint16(0) == 0x0000 ) and filesize < 70KB } /* Rule Set ----------------------------------------------------------------- */ rule crime_zeroaccess_lpe_win { meta: description = "Detects the ZeroAccess trojan local privilege exploit realted to CVE-2015-1701" author = "Vitali Kremez" reference = "https://www.virustotal.com/en/file/1f8c42caeacb44f2a738ee2104457220eca6d7a7416f953d01bc716a63b3db8d/analysis/" date = "2016-05-23" md5 = "b5dadaaf9c8fedf84542dd69c9776b04" strings: $s0 = "<assemblyIdentity type='win32' name='Microsoft.Windows.Common-Controls' version='6.0.0.0' processorArchitecture='*' publicKeyTok" ascii $s1 = "\\KnownDlls\\user32.dll" fullword wide $s2 = "\\KnownDlls\\kernel32.dll" fullword wide $s3 = "<requestedExecutionLevel level='asInvoker' uiAccess=\"false\"/>" fullword ascii $s4 = "d:\\ZZZ\\release\\ui.pdb" fullword ascii $s5 = "%p->VirtualProtect([%p, %p) %08X, %s)" fullword ascii $s6 = "%p->VirtualAlloc(%p, %08X)" fullword ascii $s7 = "%p SSL_SetURL(%s)=%p" fullword ascii $s8 = "@Microsoft Unified Security Protocol Provider" fullword wide $s9 = "rrrrtm" fullword ascii $s10 = "ddddtt" fullword ascii $s11 = "%p %s=%p" fullword ascii $s12 = "AQAPRQH" fullword ascii $s13 = "6\"60696G6P6^6g6u6~6" fullword ascii $op0 = { 3b 58 34 74 0c bf 03 00 00 40 eb 05 bf 01 00 00 } /* Opcode */ $op1 = { c3 e9 3a 05 00 00 48 8d 05 01 } /* Opcode */ $op2 = { 8b 45 fc ff 70 10 68 72 72 72 72 8b 4d fc e8 9c } /* Opcode */ condition: uint16(0) == 0x5a4d and filesize < 70KB and all of ($s*) and 1 of ($op*) }
0 Comments
Leave a Reply. |
AuthorVitali Kremez Archives
September 2016
Categories |
 RSS Feed
RSS Feed
