|
Website: vitali-honeypot.herokuapp.com
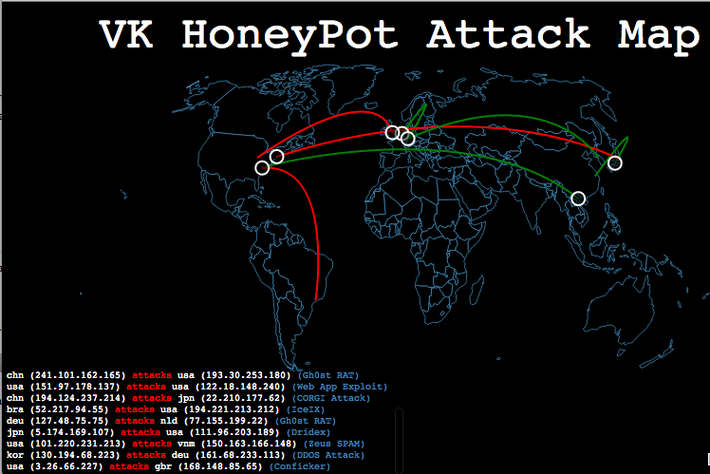
Source: https://github.com/mlsecproject/pewpew This web app uses D3 / javascript visualization to display cartographic IP data using Datamaps using javascript event timers and data queues. Examples of Usage: http://vitali-honeypot.herokuapp.com/index.html?china_mode=1&org_name=[INSERT ANY COMPANY NAME]&bad_day=1 http://vitali-honeypot.herokuapp.com/index.html?org_name=[INSERT ANY COMPANY NAME]&drill_mode=1&lat=[INSERT ANY FLOAT VALUE]&lon=[INSERT ANY FLOAT VALUE] http://vitali-honeypot.herokuapp.com/index.html?org_name=[INSERT ANY COMPANY NAME]&employee_mode=1&employee_fname=[INSERT ANY FIRST NAME]&employee_lname=[INSERT ANY LAST NAME]&lat=[INSERT ANY FLOAT VALUE]&lon=[INSERT ANY FLOAT VALUE]
0 Comments
Author: Vitali Kremez
Here are the following 12 point-of-sample malware samples that were analyzed for indicators of compromise (IoCs): (1) GetMyPass POS Malware (2) Neutrino POS Malware (3) BackOff POS Malware (4) Framework POS Malware (5) Alina POS Malware (6) vSkimmer POS Malware (7) Gorynych DiamondFox POS Botnet (8) PoSeidon POS Malware (9) Dexter POS Malware (10) Lucy TOR POS Malware (11) JackPOS Malware (12) Kaptoxa POS Malware The IoCs include Yara signatures and Sourcefire rules for each particular point-of-sale malware sample listed above. ================================================================= |
AuthorVitali Kremez Archives
July 2016
Categories |
 RSS Feed
RSS Feed
