|
# Domain Generation Algorithm (DGA): Python Implementation
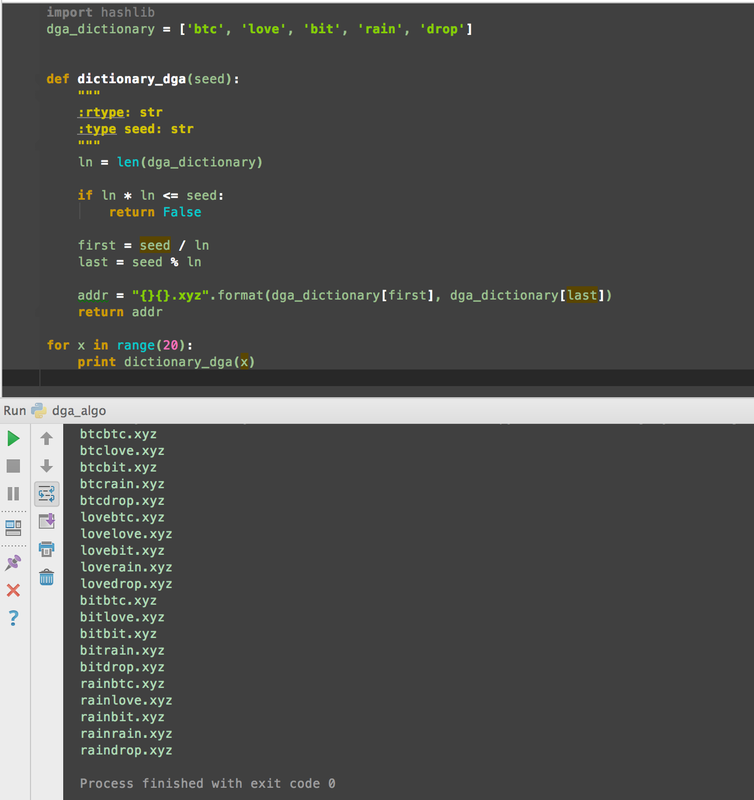
Ways to disseminate the DGA seed: (1) Spread inside the bot config (easy but insecure); (2) Generate based on the GetSystemInfo & GetCurrentUser etc. (local environment) (more secure) (3) Pull additional websites based off the seed websites' HTML source code . Example, <p> ROEbG92ZXJhaW4ueHl6ROE </p> # ROE is a marker for Base64-encoded loverain.xyz 1. # -*- coding: utf-8 -*- import hashlib def md5_dga(seed): var = hashlib.md5() # hash the seed using the entry algorithm var.update(seed) name = var.hexdigest() # cut all the strings after the 10th one part = name[:10] return "{}.xyz".format(part) seed = "cm9jayduJ3JvbGw=" # ASCII: rock'n'roll for x in range(12): seed = md5_dga(seed) print seed 2. # -*- coding: utf-8 -*- import hashlib dga_dictionary = ['btc', 'love', 'bit','rain','drop'] def dictionary_dga(seed): ln = len(dga_dictionary) # check the maximum length of the DGA dictionary if ln * ln <= seed: return False # choose 2 words first = seed / ln last = seed % ln # create an address concatenating variable 1 + variable 2 addr = "{}{}.xyz".format(dga_dictionary[first],dga_dictionary[last]) return addr for x in range(20): print dictionary_dga(x)
0 Comments
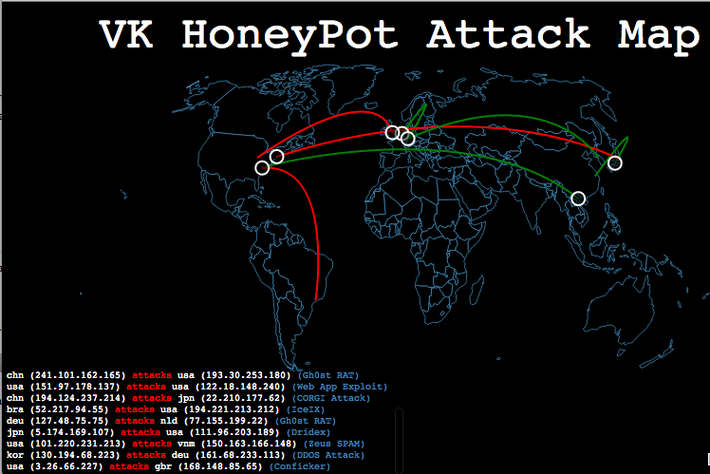
Website: vitali-honeypot.herokuapp.com
Source: https://github.com/mlsecproject/pewpew This web app uses D3 / javascript visualization to display cartographic IP data using Datamaps using javascript event timers and data queues. Examples of Usage: http://vitali-honeypot.herokuapp.com/index.html?china_mode=1&org_name=[INSERT ANY COMPANY NAME]&bad_day=1 http://vitali-honeypot.herokuapp.com/index.html?org_name=[INSERT ANY COMPANY NAME]&drill_mode=1&lat=[INSERT ANY FLOAT VALUE]&lon=[INSERT ANY FLOAT VALUE] http://vitali-honeypot.herokuapp.com/index.html?org_name=[INSERT ANY COMPANY NAME]&employee_mode=1&employee_fname=[INSERT ANY FIRST NAME]&employee_lname=[INSERT ANY LAST NAME]&lat=[INSERT ANY FLOAT VALUE]&lon=[INSERT ANY FLOAT VALUE] Author: Vitali Kremez
Here are the following 12 point-of-sample malware samples that were analyzed for indicators of compromise (IoCs): (1) GetMyPass POS Malware (2) Neutrino POS Malware (3) BackOff POS Malware (4) Framework POS Malware (5) Alina POS Malware (6) vSkimmer POS Malware (7) Gorynych DiamondFox POS Botnet (8) PoSeidon POS Malware (9) Dexter POS Malware (10) Lucy TOR POS Malware (11) JackPOS Malware (12) Kaptoxa POS Malware The IoCs include Yara signatures and Sourcefire rules for each particular point-of-sale malware sample listed above. ================================================================= "Who's Using Cyberthreat Intelligence and How?" By Dave Shackleford
[Source: http://www.sans.org/reading-room/whitepapers/analyst/cyberthreat-intelligence-how-35767] Outline: Threat Intelligence - the set of data collected, assessed and applied regarding security threats, threat actors, exploits, malware, vulnerabilities and compromise indicators Purpose of CTI: • Ability to see attacks in context • Accuracy of detection and response • Faster detection and response Data Collection Points: "In addition to the 59% stating they are gathering intelligence from their internal systems, 76% of respondents say their organizations are gathering intelligence from the security community at large. The external sources they are gathering information from include: • 56% gather intelligence from their vendor product’s CTI feeds • 54% gather intelligence from their public CTI feeds • 53% gather intelligence from open source feeds A small number of answers in the “Other” category included private feeds for government agencies and law enforcement, as well as social media and sites such as the SANS Internet Storm Center (ISC). " Intelligence Feeds "We asked those who selected “vendor-driven CTI feeds” what types of vendors were providing these. The range of responses was very broad, and many teams are obviously using CTI data from a number of different types of vendors. Endpoint security vendors led with 51%, but 43% of respondents are also getting CTI information from unified threat management (UTM)/firewall/IDS vendors and 40% from CTI platform vendors, vulnerability management providers and SIEM vendors. " Planning for CTI Organizations planning to invest in CTI feeds, tools and internal capabilities should assess their readiness for using CTI now and in the future. 1. Decide what you intend to do with CTI data and to whom you will assign to CTI planning duties. Most organizations that attempt to implement CTI ad hoc, with no budget, staff, tools or goals, tend to reap minimal rewards. 2. Focus on tools and feeds. Once you’ve decided what you plan to do with CTI (improve detection capabilities, add more granular correlation rules to your SIEM, add host-based forensics indicators, etc.), focus on two areas: What kinds of tools will you use to aggregate and collect CTI data? And will you use commercial feeds, open source and community data, or both? Many SIEM providers are now integrating CTI feeds and information readily. Be sure to look at standard import data formats if you are bringing in feeds. 3. Consider your goals. Once you’ve decided on the basics of what data you want and where it will be aggregated, think about the short- and long-term goals of the program and how you’ll measure progress. CTI Standards and Tools CVE and CVSS • Open Threat Exchange (OTX)—51% • Structured Threat Information Expression (STIX)—46% • Collective Intelligence Framework (CIF)—39% • Open Indicators of Compromise (OpenIOC) framework—33% • Trusted Automated eXchange of Indicator Information (TAXII)—33% • Traffic Light Protocol (TLP)—28% • Cyber Observable eXpression (CybOX)—26% • Incident Object Description and Exchange Format (IODEF)—23% • Vocabulary for Event Recording and Incident Sharing (VERIS)—20% |
AuthorVitali Kremez Archives
July 2016
Categories |
 RSS Feed
RSS Feed
