Author: Vitali Kremez
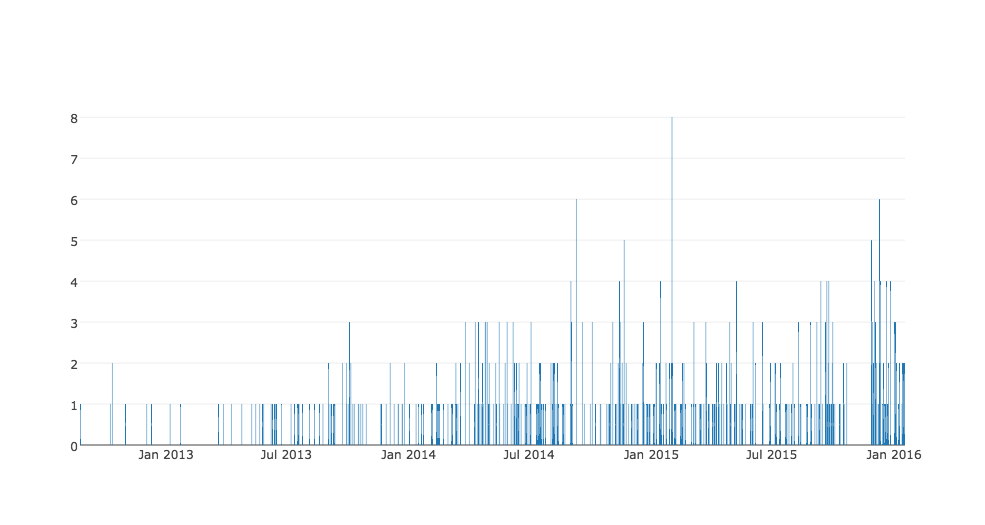
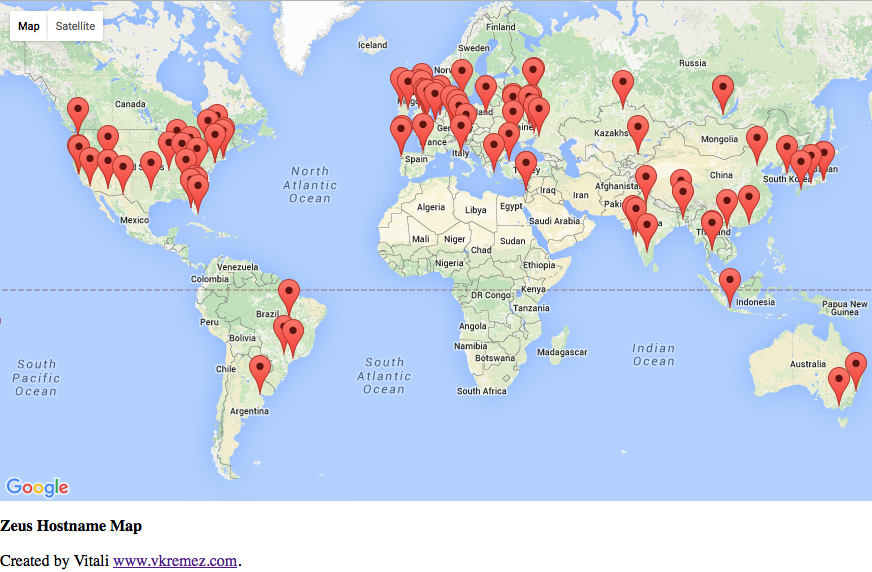
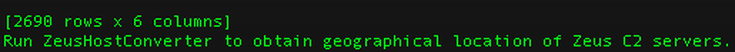
Data Source: (1) zeustracker.abuse.ch (2) cybercrime-tracker.net Language: Python, Regular Expressions, SQLite, JavaScript, HTML API: Google Maps Geocoding API, IP-API JSON API, plotly We see the largest number of ZeusC2 in the first quarter of 2015. *Creates a SQL table with 2,690 Zeus Command-and-Control servers and visualizes the database via Google Maps Geocoding API. Goal: Obtain geographical location coordinates of current and historical Zeus servers and visualize them on the Google Map. Method of Operation: *Creates SQL database "ZeusC2Tracker.sqlite" with columns mdate, url, ip, rtype, rsource; *Converts Zeus hostnames to cities using ip-api.com JSON API; *Obtains lat/long values using GeoCode API, and stores values in another SQL database "geodata.sqlite"; *Maps the data from "geodata.sqlite" to Javascript file "where.js"; *Creates viewable Google-mapped values in "where.html" that point to "where.js".
Usage:
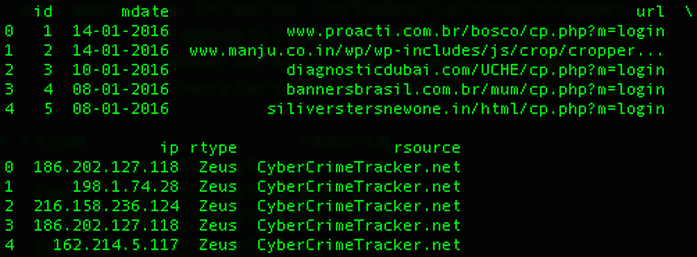
1) Run Zeusloader.py to create monolithic "ZeusC2Tracker.sqlite" database with columns mdate, url, ip, rtype, rsource; (2) Run ZeusHostConverter.py to convert hostnames to cities using /ip-api.com JSON API and post data to new"where.data" file; (3) Run Geoload.py to parse "where.data", obtain lat/long values using GeoCode API, and store values in SQL database "geodata.sqlite"; (4) Run Geodump.py to map the data from "geodata.sqlite" to new Javascript file "where.js"; and (5) View the Google-mapped values in "where.html" that point to "where.js". Example of SQL query "SELECT * From ZeusC2Tracker;" in Terminal:
Here are some interesting findings based on this SQL ZeusC2Tracker database of 2,690 ZeusC2's:
(1) We have 90 .ru [Russian] domains associated with ZeusC2's. (2) We have 6 domains that contain string "bank" associated with ZeusC2's. (3) We have 1,442 default Zeus installs associated with ZeusC2. They are identified by default control panel path "/cp.php?m=login". (4) We have 16 TOR [onion] domains associated with ZeusC2's. (5) We have 1,092 .com domains associated with ZeusC2's. (6) We have 35 .ua [Ukrainian] domains associated with ZeusC2's. (7) We have 5 .cc [Cocos (Keeling) Islands - often used by carding community] domains associated with ZeusC2's. (8) We have 28 .su [Soviet Union] domains associated with ZeusC2's. (9) We have 2 .gov [1 - Colombian, 1- Turkish] domains associated with ZeusC2's. (10) We have 3 most popular IPs 199.192.231.250 [26 domains], 198.1.80.203 [21 domains], 162.144.127.104 [16 domains] associated with with ZeusC2's.
4 Comments
Author: Vitali Kremez
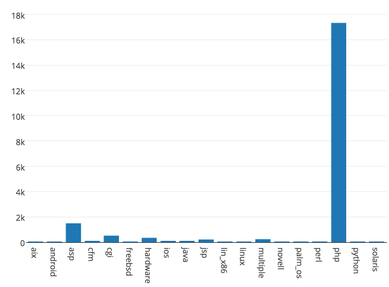
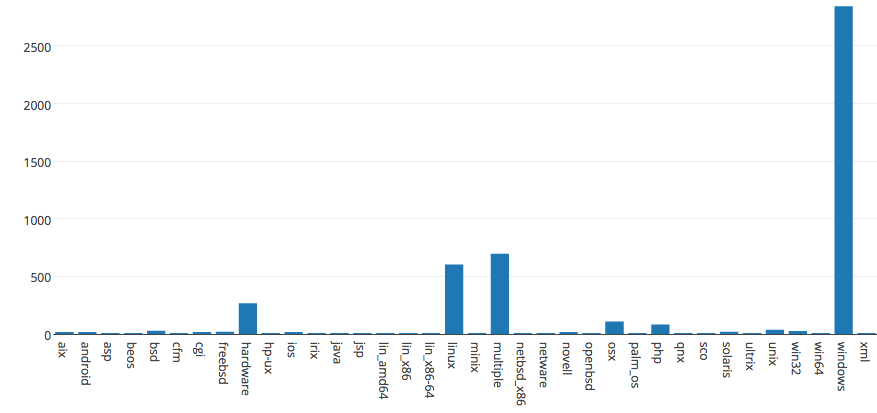
This iPython notebook creates and explores a SQL database of all known public exploits. Source: https://raw.githubusercontent.com/offensive-security/exploit-database/master/files.csv
PHP has the largest number of exploits in the SQL database. Function: (1) Creates and queries the SQL database with approx. 40,000 rows and 9 columns of public exploits; (2) Creates a graph "Number of remote exploits by platform"; [1] Windows OS has 3,340 remote exploits, the largest number of remote exploits in the SQL database. [2] Linux OS has 825 remote exploits, the second largest number in the database (3) Creates a graph "Number of webapps exploits by platform"; [1] We have approx. 17,335 of PHP webapp exploits, the largest number of webapp exploits in the SQL database. [2] We have only 1,498 asp webapp exploits, the second largest number in the database. (4) Creates a graph "Number of local exploits by platform"; [1] We have 1,561 of local Windows exploits, the largest number of local exploits in the SQL database. [2] We have only 819 Linux local exploits, the second largest number in the database. (5) Creates a graph "Number of Denial- of-Service (DOS) exploits by platform"; [1] We have 2,845 of DOS Windows exploits, the largest number of DOS exploits in the SQL database. [2] We have only 603 Linux DOS exploits, the second largest number in the database. (6) Creates a graph "Number of exploits by platform"; [1] We have approx. 17,590 of PHP exploits, the largest number of exploits in the SQL database. [2] We have only 603 Linux exploits, the second largest number in the database. (7) Queries the SQL database for Windows exploits; We have 7,921 Windows exploits in the database. (8) Creates a graph "Number of exploits by date"; We have the largest number of exploits developed in 2010 among other years. Windows has the largest number of DOS exploits among other platforms.
Inspired by Bryan Downing's "QuantsLab HFT"
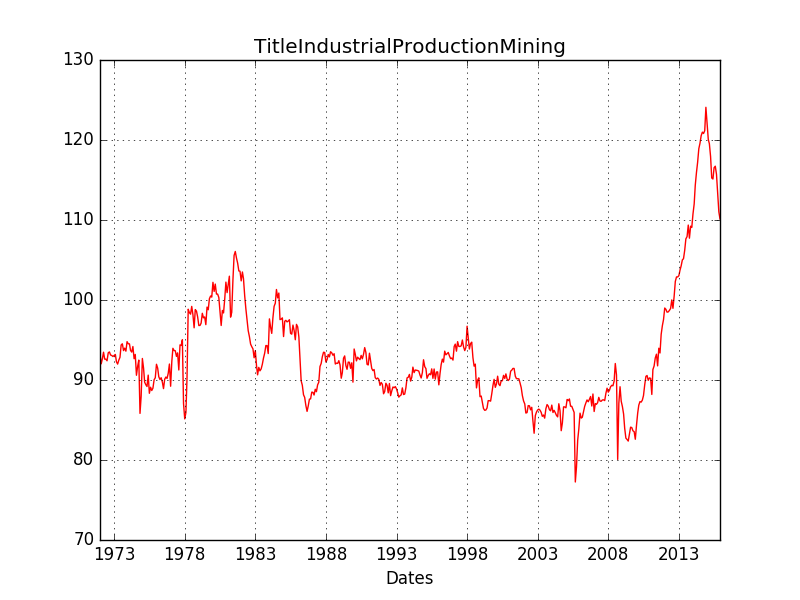
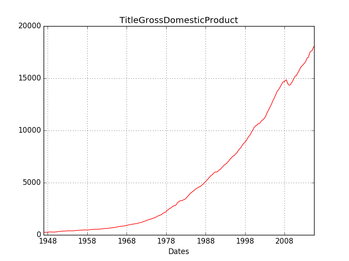
This Python iNotebook analyzes and visualizes most important U.S. economic indices using Matlab. Data Source: St.Louis Fed FRED Economic Research Here are the analyzed indices: # [1] U.S. Gross Domestic Product from 1948-2015 # [2] U.S. New Orders Nondefense Capital Goods Excluding Aircraft Index # [3] U.S. ISM Manufacturing PMI Composite Index # [4] U.S. Industrial Production Mining Index # [5] U.S. Industrial Production Business Equipment Index # [6] U.S. Continued Claims Insured Unemployment Index # [7] U.S. New Private Housing Units Authorized by Building Permits Index # [8] U.S. Industrial Production Materials Index Website: https://vitali-fusion.herokuapp.com/
Courtesy of Derek Eder [https://github.com/derekeder/FusionTable-Map-Template-Heroku] |
AuthorVitali Kremez Archives
January 2016
Categories |
 RSS Feed
RSS Feed
