|
Source: OpenSecurityTraining
0 Comments
Inspired by: http://sgros-students.blogspot.com/2014/09/reversing-with-immunity-debugger.html
Goal:
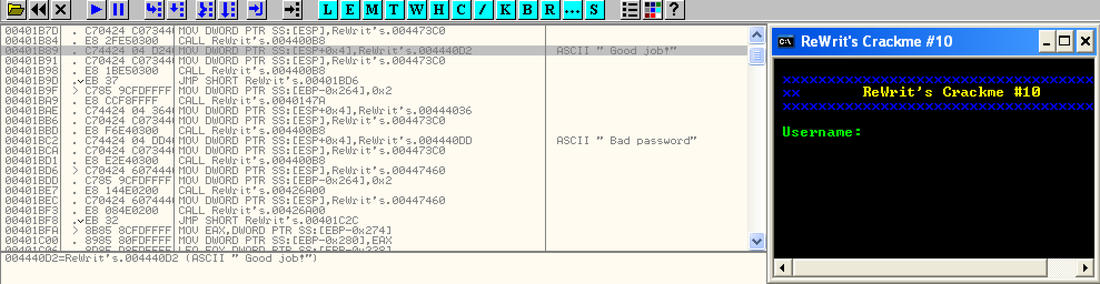
We see that in case when our password is incorrect we get message Bad password. So lets try to find where that message is loaded up and displayed. To do that we shall search binary file for string Bad password, or to be more precise, we shall search binary for all strings which are referenced to in the code. This method is effective only if binary isn't packed, obfuscated or encrypted in any way. |
AuthorVitali Kremez Archives
August 2016
Categories |
 RSS Feed
RSS Feed
