|
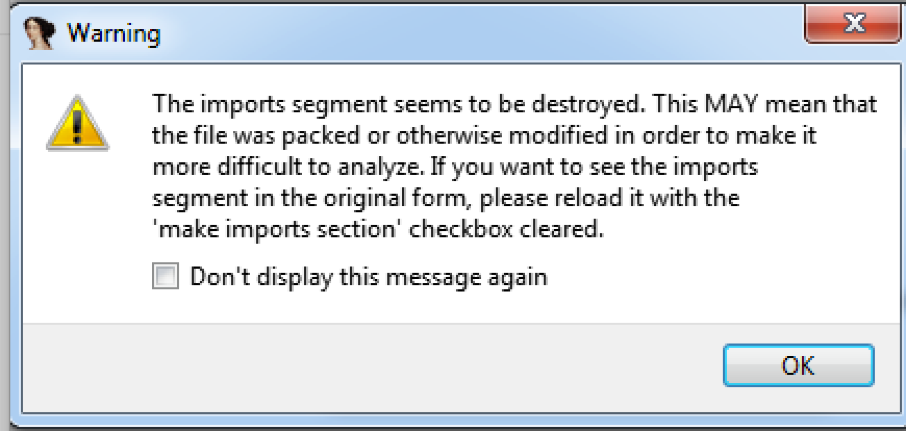
Source: hexrays.com Goal: Advance IDA Pro understanding Step: Load file using as Portable Executable for 80386 (metapc) reveals multiple errors and “Warning” tab informing about possible obfuscation routines. The following flags are checked out as well:
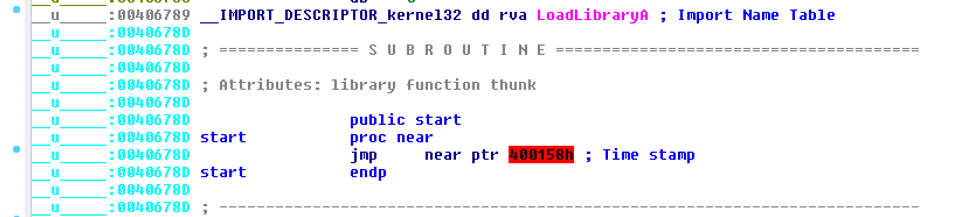
The subroutine reveals the unresolvable jmp call to nowhere, as marked in red.
0 Comments
Source: Intro to Intel x86, OpenSecurityTraining
1 - Fix C++/ Linker Setup Properties * Program Database (/Zi) * Disable Security Check * __cdecl (/Gd) or __stdcall (/Gz) * Linker/Enable Incremental Linking (No) 2 - Breakpoint on Main -> Go to Disassembly 3 - Windows/Memory -> Address on ESP (hexadecimal display and 4-byte integers) 4 - Windows/Registers Source: OpenSecurityTraining
Inspired by: http://sgros-students.blogspot.com/2014/09/reversing-with-immunity-debugger.html
Goal:
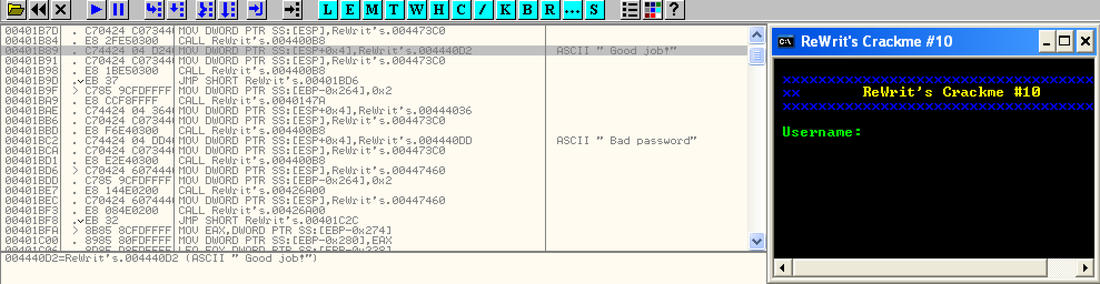
We see that in case when our password is incorrect we get message Bad password. So lets try to find where that message is loaded up and displayed. To do that we shall search binary file for string Bad password, or to be more precise, we shall search binary for all strings which are referenced to in the code. This method is effective only if binary isn't packed, obfuscated or encrypted in any way. Unpacker Tail Transitions
mov ecx, 0x400000
mov [ecx], 0x53 // 'S' inc ecx mov [ecx], 0x54 // 'T' inc ecx mov [ecx], 0x52 // 'R' inc ecx mov [ecx], 0x00 This sequence would put the ASCII string “STR” at the memory location 0x400000. A variant of this is to construct the string via one or more PUSH instructions:
Source: OpenSecurityTraining
#include <idc.idc> static main() {
auto start, end, addr, mnem, count, opnd, opnd1, opnd2; start = SegStart( ScreenEA() ); nd = SegEnd( ScreenEA() ); addr = start; count = 0; while( addr < end ) { mnem = GetMnem( addr ); // Common VM detect instructions if( mnem == "sidt" || mnem == "sgdt" || mnem == "sldt" || mnem == "smsw" || mnem == "str" ) { Message( "%08x: Found %s\n", addr, mnem ); SetColor( addr, CIC_ITEM, 0x0088ff ); // orange } // Read Time Stamp Counter if( mnem == "rdtsc" ) { Message( "%08x: Found %s\n", addr, mnem ); SetColor( addr, CIC_ITEM, 0xff8800 ); // blue } // Exception Handling or other PEB/TEB access opnd = ""; opnd1 = GetOpnd( addr, 0 ); opnd2 = GetOpnd( addr, 1 ); if( strstr( opnd1, "fs:" ) > -1 ) { opnd = opnd1; } else { if( strstr( opnd2, "fs:" ) > -1 ) opnd = opnd2; } if( opnd != "" ) { Message( "%08x: Found %s\n", addr, opnd ); SetColor( addr, CIC_ITEM, 0xff8888 ); // purple } addr = NextHead( addr, BADADDR ); count = count + 1; } Message( "Processed %d instructions from %08x to %08x\n", count, start, end ); } Source: OpenSecurityTraining.info
Some Notable JCC Instructions • JZ/JE: if ZF == 1 • JNZ/JNE: if ZF == 0 • JLE/JNG : if ZF == 1 or SF != OF • JGE/JNL : if SF == OF • JBE: if CF == 1 OR ZF == 1 • JB: if CF == 1 |
AuthorVitali Kremez Archives
August 2016
Categories |
 RSS Feed
RSS Feed
