|
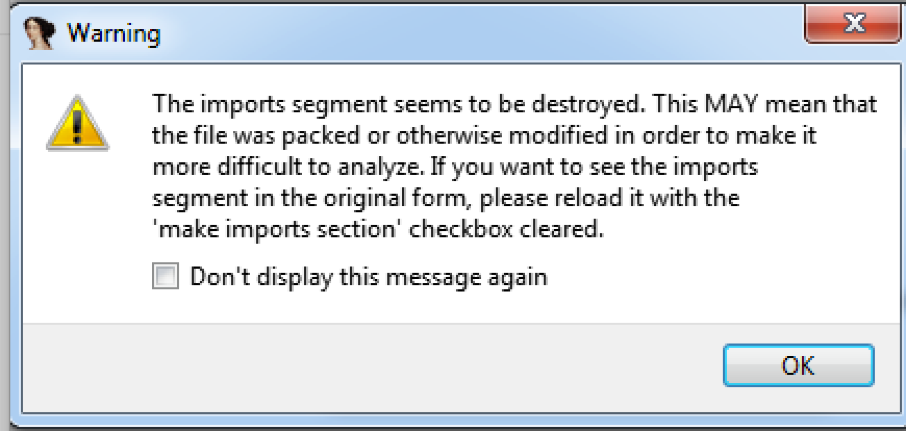
Source: hexrays.com Goal: Advance IDA Pro understanding Step: Load file using as Portable Executable for 80386 (metapc) reveals multiple errors and “Warning” tab informing about possible obfuscation routines. The following flags are checked out as well:
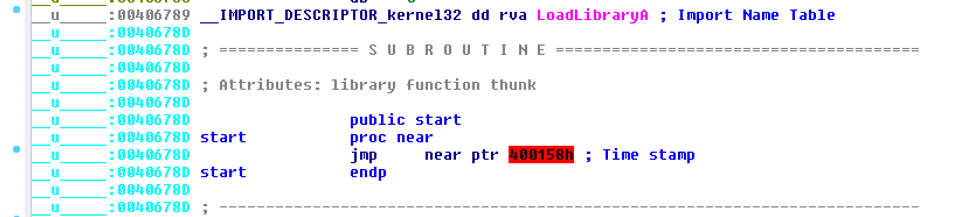
The subroutine reveals the unresolvable jmp call to nowhere, as marked in red.
0 Comments
Source: Intro to Intel x86, OpenSecurityTraining
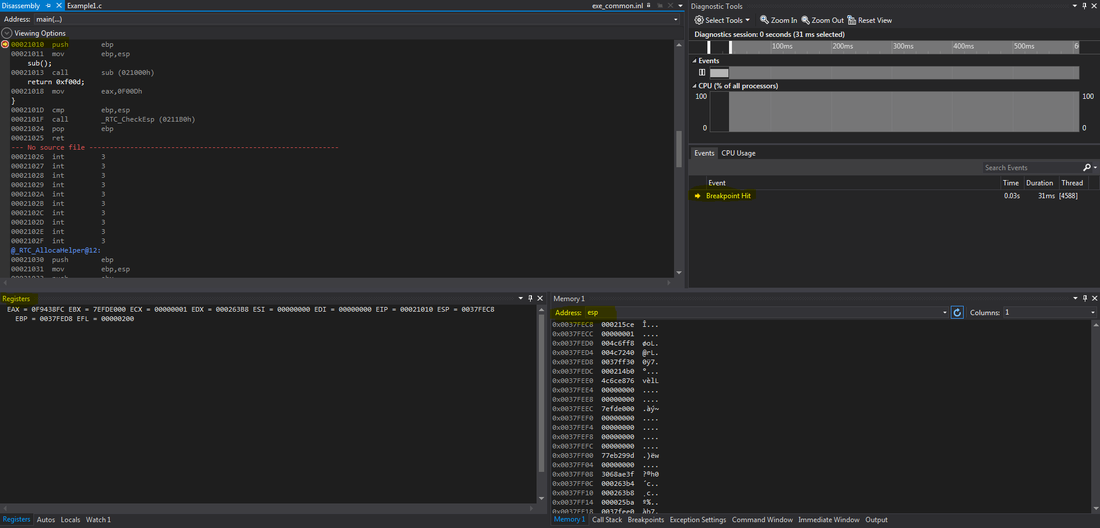
1 - Fix C++/ Linker Setup Properties * Program Database (/Zi) * Disable Security Check * __cdecl (/Gd) or __stdcall (/Gz) * Linker/Enable Incremental Linking (No) 2 - Breakpoint on Main -> Go to Disassembly 3 - Windows/Memory -> Address on ESP (hexadecimal display and 4-byte integers) 4 - Windows/Registers |
AuthorVitali Kremez Archives
August 2016
Categories |
 RSS Feed
RSS Feed
