|
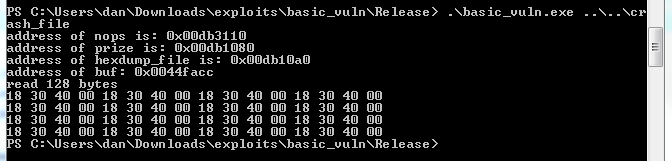
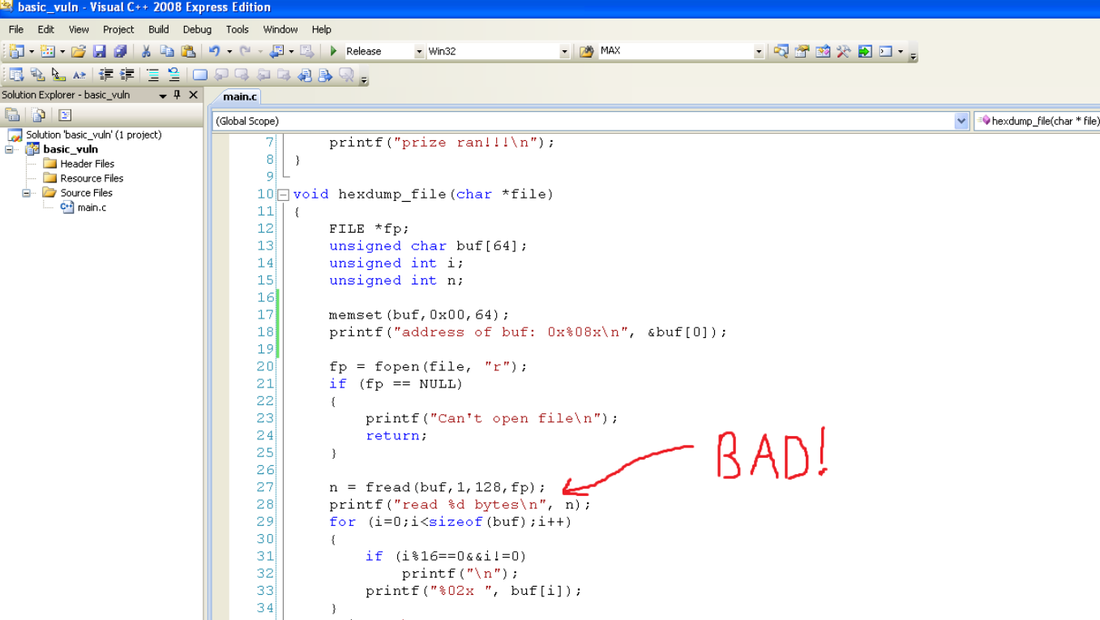
Source: OpenSecurityTraining.info Part 1 Fuzzing and crash dump analysis From crash dump to working exploit lab in WinDBG Here is a very basic program to help us explore our exploit environment. The
basic_vuln program reads in a binary file and displays the first 64 hexadecimal bytes from that file. The program prints various meta data such as the location of variables and functions in the process address space. This meta information will help simplify the exploitation process as we are learning.
0 Comments
|
 RSS Feed
RSS Feed
