|
[*] MD5 : 2dfddbc240cd6e320f69b172c1e3ce58
[*] SHA-1 : e573a6fd61fd3928201d85dbffe5aefe21e49192 [*] SHA-256 : e70614382ad300bd8c1f2cedb3259212057c40433e22ffeee7292ae576c4eae2 [+] File Type: EXE [+] Address of entry point : 0x00005a82 [+] Image Base Address : 0x00400000 [+] Packer / Compiler: MS Visual C++ 8.0 ------------------------------------------------------------ Executable \Windows\explorer.exe Executable \jucheck.exe Web Page logmeinrescue[.]us[.]com/system/oauth/gate[.]php Library ADVAPI32.dll Library KERNEL32.dll Library SHELL32.dll Library USER32.dll Library USERENV.dll Library WINHTTP.dll Database C:\work\treasureHunter\Release\treasureHunter [+] Sections Name: .text Virtual Address: 0x00001000 Size: 0x0000fcda Entropy: 6.667572 Name: .rdata Virtual Address: 0x00011000 Size: 0x00005eb2 Entropy: 4.641277 Name: .data Virtual Address: 0x00017000 Size: 0x00002fe0 Entropy: 3.331543 Name: .rsrc Virtual Address: 0x0001a000 Size: 0x000001e0 Entropy: 4.710061 Name: .reloc Virtual Address: 0x0001b000 Size: 0x000012a4 Entropy: 6.678696
0 Comments
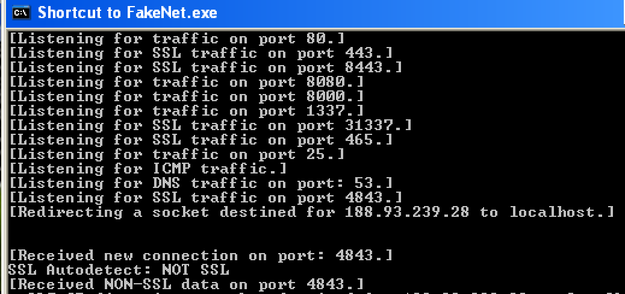
Tools: CFF Explorer, Ollydbg, FakeNet, IDAPro, ExeScan, SysAnalyzer, pestudio Environment: Microsoft XP SP1 (Victim), Remnux VM (Analyst) Takeaways:
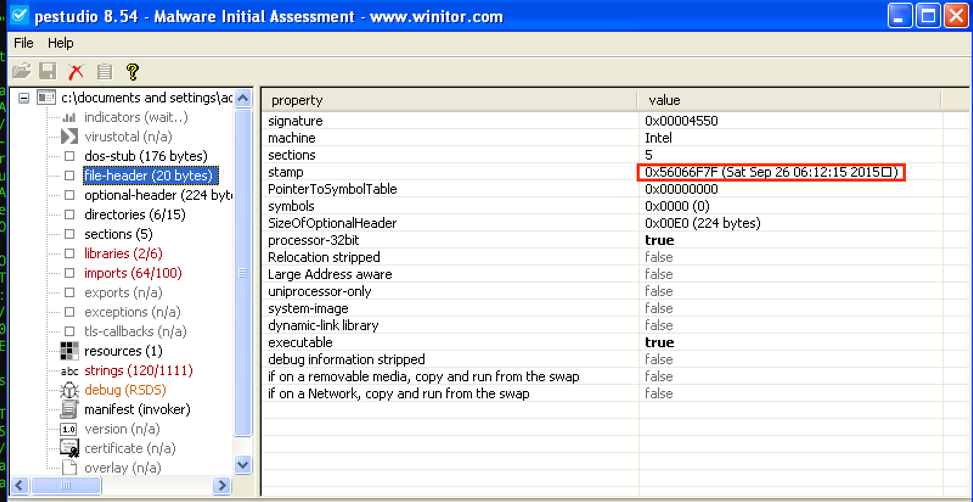
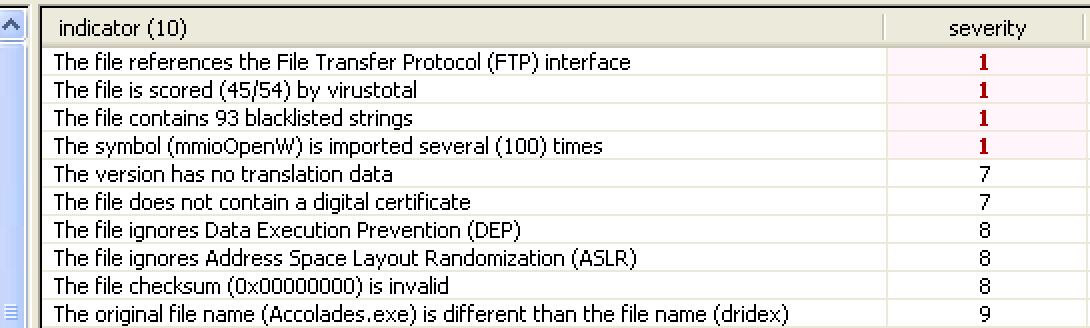
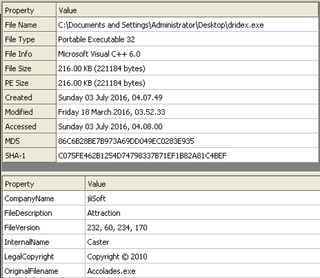 File: dridex.exe Size: 221184 Unpacked at OEP 00422856 (Armadillo Packer) Processes: PID ParentPID User Path -------------------------------------------------- 4776 5124 USER-06EF21E8DC:Administrator C:\Documents and Settings\Administrator\Desktop\dridex.exe [*] MD5 : 86c6b28be7b973a69dd049ec0283e935 [*] SHA-1 : c075fe462b1254d74798337b71ef1b82a81c4bef [*] SHA-256 : a9dd22723f0ad6316c2c87727f5b01319cf703d03799efad44f9d8930c4ce5eb [*] Imphash : a8c14b423f16267d80724d4045aa5bb7 [+] File Type: EXE [+] Signature [Compiler/Packer] ['Armadillo v1.71'] [+] Address of entry point : 0x00022b56 [+] Image Base Address : 0x00400000 [+] Sections Name: .text Virtual Address: 0x00001000 Size: 0x00021cec Entropy: 7.198276 Name: .rdata Virtual Address: 0x00023000 Size: 0x0000a896 Entropy: 6.127880 Name: .data Virtual Address: 0x0002e000 Size: 0x0001efe4 Entropy: 4.501903 Name: .rsrc Virtual Address: 0x0004d000 Size: 0x00003120 Entropy: 4.565060 [+] Anomalies Check [*] Header Checksum is zero! [-] Import Table IA: 0x004230c0 CreateRemoteThread IA: 0x004231bc HttpSendRequestExA IA: 0x00423184 HttpQueryInfoA IA: 0x004231a4 HttpSendRequestW IA: 0x00423110 InternetCloseHandle IA: 0x004231ac InternetGetConnectedState IA: 0x004231a0 InternetReadFileExA |
AuthorVitali Kremez Archives
September 2016
Categories |
 RSS Feed
RSS Feed
