|
Reference: https://www.virustotal.com/en/file/1f8c42caeacb44f2a738ee2104457220eca6d7a7416f953d01bc716a63b3db8d/analysis/ Objective:
LPE Implementation and Functionality:
0 Comments
Source: fumalwareanalysis.blogspot.com
Learning Goals:
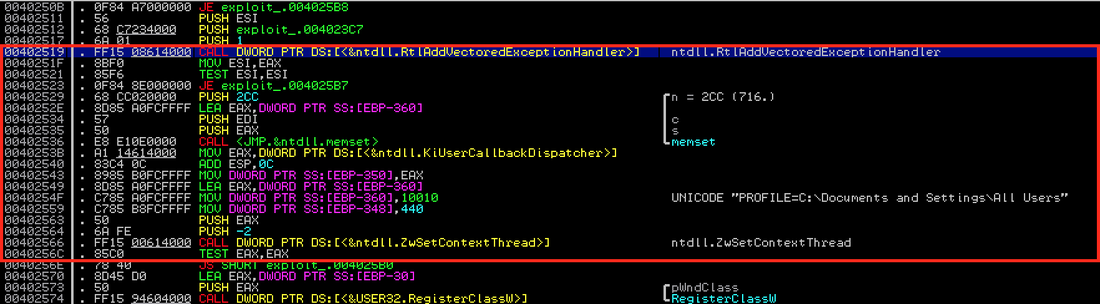
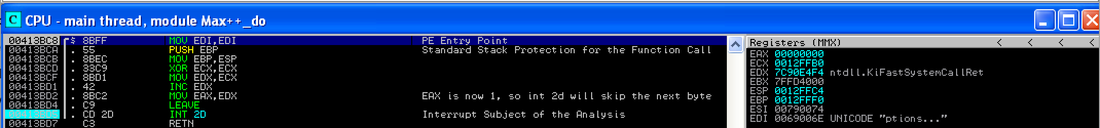
The general anti-debugging techniques are as follows: (1) to detect the existence of a debugger, and behave differently when a debugger is attached to the current process; and, (2) to disrupt or crash a debugger. The instruction we are trying to analyze is the "INT 2D" instruction located at 0x00413BD5 (as shown in Figure 1). By single-stepping the malware, you might notice that the program's entry point is 0x00413BC8. After the execution of the first 8 instructions, right before the "INT 2D" instruction, the value of EAX is 0x1. This is an important fact you should remember in the later analysis. |
AuthorVitali Kremez Archives
September 2016
Categories |
 RSS Feed
RSS Feed
