|
Tools: CFF Explorer, Ollydbg, FakeNet, IDAPro, ExeScan, SysAnalyzer, pestudio Environment: Microsoft XP SP1 (Victim), Remnux VM (Analyst) Takeaways:
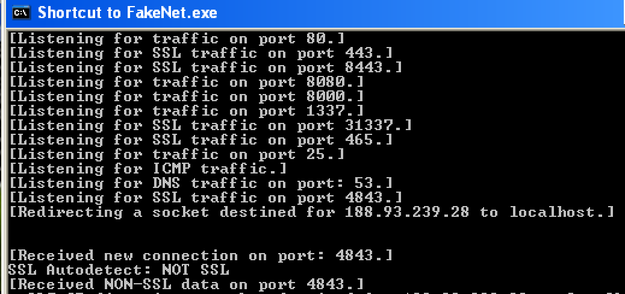
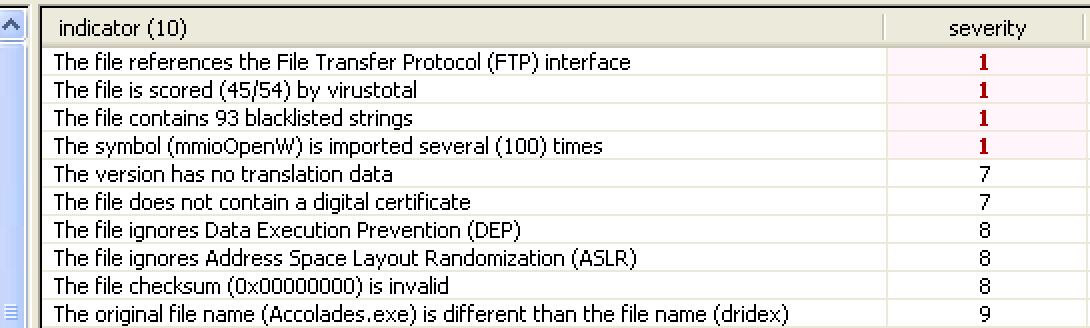
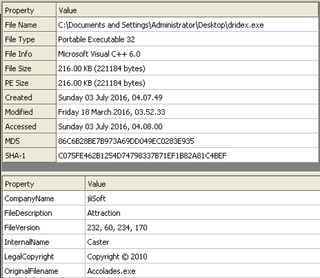 File: dridex.exe Size: 221184 Unpacked at OEP 00422856 (Armadillo Packer) Processes: PID ParentPID User Path -------------------------------------------------- 4776 5124 USER-06EF21E8DC:Administrator C:\Documents and Settings\Administrator\Desktop\dridex.exe [*] MD5 : 86c6b28be7b973a69dd049ec0283e935 [*] SHA-1 : c075fe462b1254d74798337b71ef1b82a81c4bef [*] SHA-256 : a9dd22723f0ad6316c2c87727f5b01319cf703d03799efad44f9d8930c4ce5eb [*] Imphash : a8c14b423f16267d80724d4045aa5bb7 [+] File Type: EXE [+] Signature [Compiler/Packer] ['Armadillo v1.71'] [+] Address of entry point : 0x00022b56 [+] Image Base Address : 0x00400000 [+] Sections Name: .text Virtual Address: 0x00001000 Size: 0x00021cec Entropy: 7.198276 Name: .rdata Virtual Address: 0x00023000 Size: 0x0000a896 Entropy: 6.127880 Name: .data Virtual Address: 0x0002e000 Size: 0x0001efe4 Entropy: 4.501903 Name: .rsrc Virtual Address: 0x0004d000 Size: 0x00003120 Entropy: 4.565060 [+] Anomalies Check [*] Header Checksum is zero! [-] Import Table IA: 0x004230c0 CreateRemoteThread IA: 0x004231bc HttpSendRequestExA IA: 0x00423184 HttpQueryInfoA IA: 0x004231a4 HttpSendRequestW IA: 0x00423110 InternetCloseHandle IA: 0x004231ac InternetGetConnectedState IA: 0x004231a0 InternetReadFileExA Kernel31 Api Log (Interesting Anti-Analysis): -------------------------------------------------- ***** Installing Hooks ***** 771b9296 CreateMutex((null)) 771b180c WaitForSingleObject(71c,ffffffff) 71ad108d GetCurrentProcessId()=4776 771bac3b LoadLibraryA(wsock32)=71ad0000 771bacdf LoadLibraryA(ws2_32)=71ab0000 405a7c RegOpenKeyExA (HKLM\SOFTWARE\TrendMicro\Vizor) 405a45 RegOpenKeyExA (HKLM\SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName) 405a45 RegOpenKeyExA (HKCU\Volatile Environment) 77de98fb RegOpenKeyExA (SOFTWARE\Microsoft\Cryptography\Providers\Type 001) 77de998b RegOpenKeyExA (HKLM\SOFTWARE\Microsoft\Cryptography\Defaults\Provider Types\Type 001) 77de7a5b RegOpenKeyExA (HKLM\SOFTWARE\Microsoft\Cryptography\Defaults\Provider\Microsoft Strong Cryptographic Provider) 77de8d4c ReadFile() 7c821a7c CreateFileA(C:\WINDOWS\system32\rsaenh.dll) 68026005 ReadFile() 680265ce RegOpenKeyExA (HKLM\Software\Policies\Microsoft\Cryptography) 77de8810 LoadLibraryA(rsaenh.dll)=68000000 680223ff RegOpenKeyExA (HKLM\Software\Microsoft\Cryptography) 680257b0 RegOpenKeyExA (HKLM\Software\Microsoft\Cryptography\Offload) 405a45 RegOpenKeyExA (HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall) 40923e RegEnumKeyA(Fiddler2) 405a45 RegOpenKeyExA (7-Zip) 405a45 RegOpenKeyExA (AddressBook) 405a45 RegOpenKeyExA (Connection Manager) 405a45 RegOpenKeyExA (DirectAnimation) 405a45 RegOpenKeyExA (DirectDrawEx) 405a45 RegOpenKeyExA (DXM_Runtime) 405a45 RegOpenKeyExA (Explorer Suite_is1) 405a45 RegOpenKeyExA (Fiddler2) 405a45 RegOpenKeyExA (Fontcore) 405a45 RegOpenKeyExA (ICW) 405a45 RegOpenKeyExA (IDA Pro Free_is1) 405a45 RegOpenKeyExA (IE40) 405a45 RegOpenKeyExA (IE4Data) 405a45 RegOpenKeyExA (IE5BAKEX) 405a45 RegOpenKeyExA (IEData) 405a45 RegOpenKeyExA (Malcode Analyst Pack_is1) 405a45 RegOpenKeyExA (Microsoft .NET Framework 4 Client Profile) 405a45 RegOpenKeyExA (Microsoft .NET Framework 4 Extended) 405a45 RegOpenKeyExA (Microsoft Help Viewer 1.0) 405a45 RegOpenKeyExA (MobileOptionPack) 405a45 RegOpenKeyExA (Mozilla Firefox 43.0.1 (x86 en-US)) 405a45 RegOpenKeyExA (MozillaMaintenanceService) 405a45 RegOpenKeyExA (MPlayer2) 405a45 RegOpenKeyExA (NetMeeting) 405a45 RegOpenKeyExA (OutlookExpress) 405a45 RegOpenKeyExA (PCHealth) 405a45 RegOpenKeyExA (SchedulingAgent) 405a45 RegOpenKeyExA (SDKSetup_7.1.7600.0.30514) 405a45 RegOpenKeyExA (SysAnalyzer_is1) 405a45 RegOpenKeyExA (WIC) 405a45 RegOpenKeyExA (WinPcapInst) 405a45 RegOpenKeyExA (Wireshark) 771c2949 RegOpenKeyExA (HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Http Filters\RPA) 771c2969 RegOpenKeyExA (HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Http Filters\RPA) 77a8a881 RegOpenKeyExA (HKLM\Software\Microsoft\Cryptography\OID) 77a8a74e RegEnumKeyA(EncodingType 0) 77a8a769 RegOpenKeyExA (EncodingType 0) 77a8a769 RegOpenKeyExA (CertDllOpenStoreProv) 77a8a74e RegEnumKeyA(#16) 77a8a769 RegOpenKeyExA (#16) 77a8a74e RegEnumKeyA(Ldap) 77a8a769 RegOpenKeyExA (Ldap) 77a8a74e RegEnumKeyA(EncodingType 1) 77a8a769 RegOpenKeyExA (EncodingType 1) 77aa3643 LoadLibraryA(VERSION.dll)=77c00000 769c4e0b GlobalAlloc() 77aa3acd LoadLibraryA(userenv.dll)=769c0000 769c7c18 ReadFile() 77abf798 ReadFile() 76c31b3f CreateMutex((null)) 771fdb05 LoadLibraryA(wintrust.dll)=76c30000 77238600 LoadLibraryA(VERSION.dll)=77c00000 771fde83 LoadLibraryA(schannel)=767f0000 771b16f6 GetSystemTime() 771bcb80 WaitForSingleObject(710,ffffffff) 771bc7b4 WaitForSingleObject(714,ffffffff) 771cd245 GetVersionExA() 771cd1ca GetVersionExA() 76ee36b4 GlobalAlloc() 76ee3aa4 GlobalAlloc() 76ee3a16 CreateMutex(RasPbFile) 771cd128 LoadLibraryA(RASAPI32.DLL)=76ee0000 77f70640 RegOpenKeyExA (Domains\188.93.239.28) 77f68c60 RegOpenKeyExA (HKLM\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\188.93.239.28) 7e1ebd98 LoadLibraryA(WININET.dll)=771b0000 77f70640 RegOpenKeyExA (ProtocolDefaults\) 7e1ea432 WaitForSingleObject(798,ffffffff) 771bd320 socket(family=2,type=1,proto=6) 21a962 GetCurrentProcessId()=4776 212354 GetCommandLineA() 1f977e RegOpenKeyExA (HKLM\software\komodia) 1f9660 GetVersionExA() 71ab78f1 LoadLibraryA(C:\WINDOWS\system32\ASProxy.dll)=1e0000 7c8106e5 CreateRemoteThread(h=ffffffff, start=1ec3c0) 1ecc5d GetSystemTime() 7c8106e5 CreateRemoteThread(h=ffffffff, start=2067c0) 77de6dd6 WaitForSingleObject(62c,2bf20) 77e9f2ff RegOpenKeyExA (HKLM\Software\Microsoft\Rpc\SecurityService) 71a56c59 LoadLibraryA(C:\WINDOWS\system32\MSWSOCK.dll)=71a50000 20411f WaitForSingleObject(61c,64) 71aa17d6 GlobalAlloc() 71ab78f1 LoadLibraryA(C:\WINDOWS\system32\mswsock.dll)=71a50000 1f7a50 GetVersionExA() 71aa39d4 GlobalAlloc() 7c8106e5 CreateRemoteThread(h=ffffffff, start=71aa2af1) 771bd363 bind(604, port=0) 771bd3a9 connect( 188.93.239.28:4843 ) 71aa2b53 LoadLibraryA(C:\WINDOWS\system32\WS2HELP.dll)=71aa0000 20411f WaitForSingleObject(5f4,4e20) 5ad8bdf9 GetCurrentProcessId()=4776 5ad7a0e2 IsDebuggerPresent() 20411f WaitForSingleObject(5f0,32) 771bfb5a closesocket(604) Raw Strings: -------------------------------------------------- File: dridex_dmp.exe_ MD5: aeedb82a2dfd267c7fb5cf25e2891e89 Size: 331778 VS_FIXEDFILEINFO: FileVersion : 0.230.46.255 ProductVersion : 0.168.135.68 StrucVersion : 0x10000 FileFlagsMask : 0x3f FileFlags : 0 FileOS : 0x40004 FileType : 1 FileSubtype : 0 # StringTable 000004b0: CompanyName : "jiiSoft" FileDescription : "Attraction" FileVersion : "232, 60, 234, 170" InternalName : "Caster" LegalCopyright : "Copyright © 2010" OriginalFilename : "Accolades.exe" ProductVersion : "67, 173, 162, 182" === Compiler === MS Visual C++ v6.0
0 Comments
Leave a Reply. |
AuthorVitali Kremez Archives
September 2016
Categories |
 RSS Feed
RSS Feed
